CERT-SE CTF 2023
7 min read
Published at: Dec 22, 2023

See how to capture all 7 flags of the yearly CERT-SE Capture The Flag. It involves everything between network analysis, to ciphers, and hidden radio messages!
Metadata
Meta
- Name: CERT-SE CTF 2023
- URL: https://www.cert.se/2023/09/cert-se-ctf2023
Goal
- Capture the 7 hidden flags of the yearly CERT-SE ctf!
- Flag format: CTF[...]
Cheat Sheet
Before we begin, as always there is a generic Cheat Sheet for this room which could be integrated in your own notes. You find it at at the bottom of this write-up. You can also find all of my notes at https://hailstormsec.com/posts/categories/notes.
Flags
IRC Dialog
PRIVMSG #ops :is this really safe, I mean it's not encrypted right?
:[email protected] PRIVMSG #ops :we should be safe, it's only internal traffic on the hypervisor
:[email protected] PRIVMSG #ops :and the secret management system is encrypted with TLS
PRIVMSG #ops :should we proceed then?
:[email protected] PRIVMSG #ops :yes, you have to unlock the vault with the secret stored on the secret-management server
PRIVMSG #ops :yes I know I know. Just give me a sec
:[email protected] PRIVMSG #ops :ok
PRIVMSG #ops :so, I have unlocked the vault, you can do your thing now
:[email protected] PRIVMSG #ops :thanks
PRIVMSG #ops :Hey, by the way you were saying we are listed on some target list for cyber attacks?
:[email protected] PRIVMSG #ops :yes we should keep our eyes open for anomalies
PRIVMSG #ops :ok, I will ping Christina, she is really good with the FPC and the analysis backend
PRIVMSG #ops :ping @Christina
:[email protected] PRIVMSG #ops :Hi Alice, how are you?
PRIVMSG #ops :just fine, how are you?
:[email protected] PRIVMSG #ops :o fine, just a lot of work with the new IDS. So many false positives, not really useful right now
PRIVMSG #ops :I see. Here is something to cheer you up a bit
PRIVMSG Christina :SHA-256 checksum for message.wav (remote): 4e31cddd5b972ce211770aca79dc2576099ad07c303de805b89604a7bfbc8b4c
:[email protected] PRIVMSG Alice :.DCC SEND message.wav 3232235550 51991 11888756 47.
:[email protected] PRIVMSG #ops :hahaha, that was wonderful. Thank you!
PRIVMSG #ops :Bob mentioned we are on some list of potential cyber operation targets. Please let us know if you find anything suspicious.
:[email protected] PRIVMSG #ops :yeah sure will. Do you know what kind of list and who's behind the announcement?
PRIVMSG #ops :He told me the group announcing the list is known to exfiltrate information
:[email protected] PRIVMSG #ops :ok, I'll see what I can find
:[email protected] PRIVMSG #ops :damn, I found some suspicious traffic to a known bad address
PRIVMSG #ops :Oh no
:[email protected] PRIVMSG #ops :Looks like they got in to that mail server we told operations to patch weeks ago!!
:[email protected] PRIVMSG #ops :need to investigate what data they transferred but It looks like it originates from the secret-management server.......
PRIVMSG #ops :Oh no, Bob and I used the secret earlier today
Found by following the IRC stream
Flag 1 - Rebus
-
When extracting the initial zip-file there is a file named
CERT-SE CTF2023 - CompetenceLateRoadThink.odt. -
A google search later exposes that it's an OpenOffice document file.
-
A quick download of LibreOffice later and I open the project - which grants me my first flag at the bottom of the page.
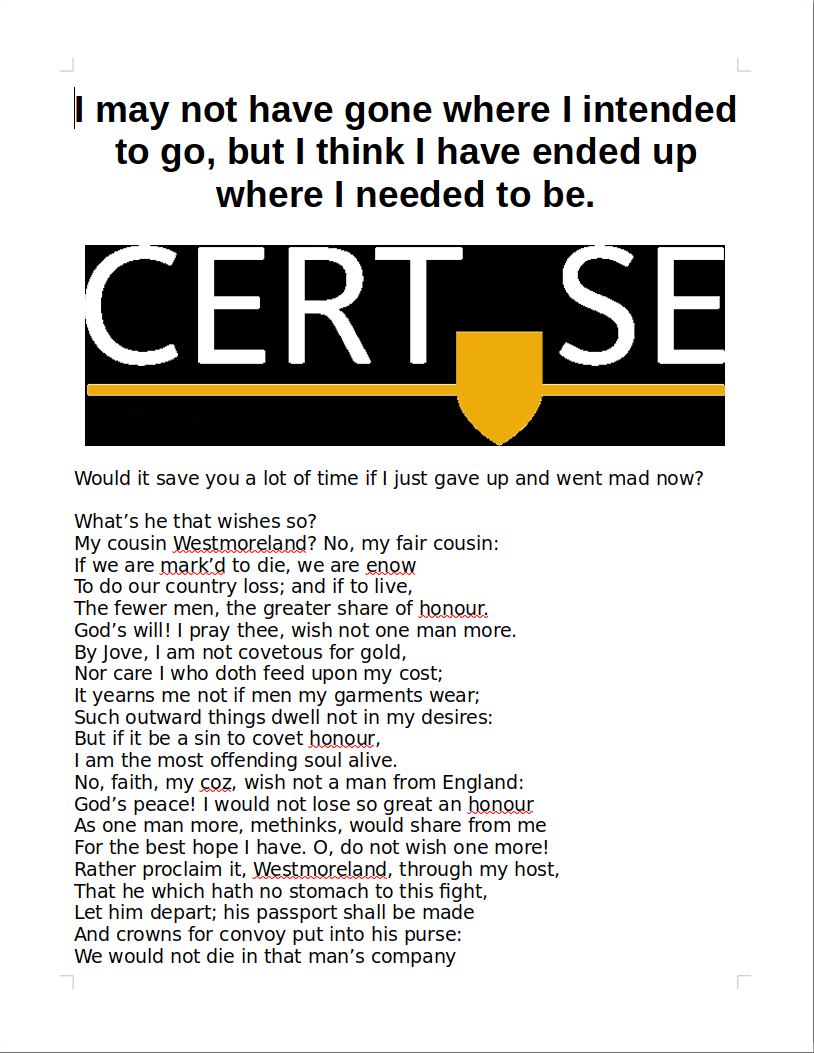
Apparently it's an excerpt from Shakespeare's play "Henry V." It is a famous soliloquy from Act 4, Scene 3. -
Now we're faced with a rebus which solves the final flag.
Answers(s)
CTF[☔-ra+💿d=i+⛺t=d] -> rain-ra + cd,d=i tent,t=d -> in + ci + dent => CTF[incident]
Flag 2 - Decrypt TLS
- When looking at Export Objects (HTTP) I find two files.
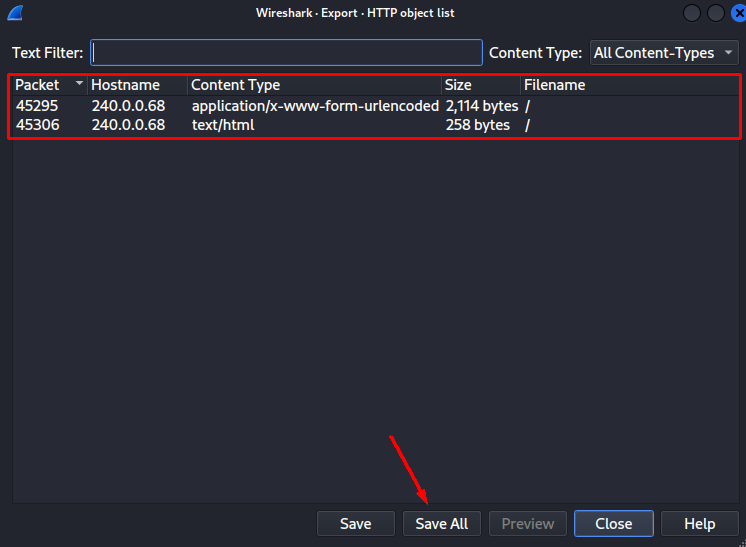
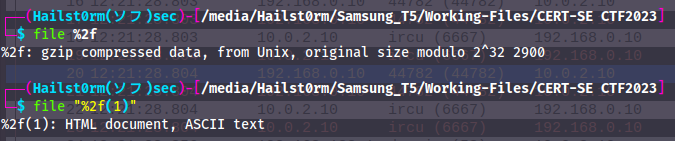
2. The HTML document is a default network simulation html file - however the gzip file contains a PEM-certificate which seem to belong to the secret-management server hinted in the IRC dialog.
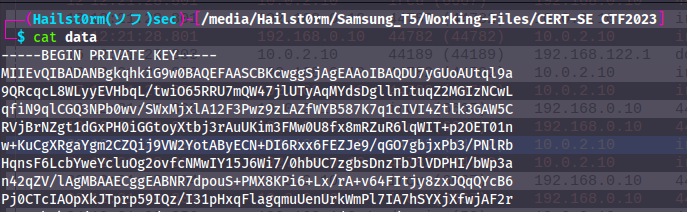
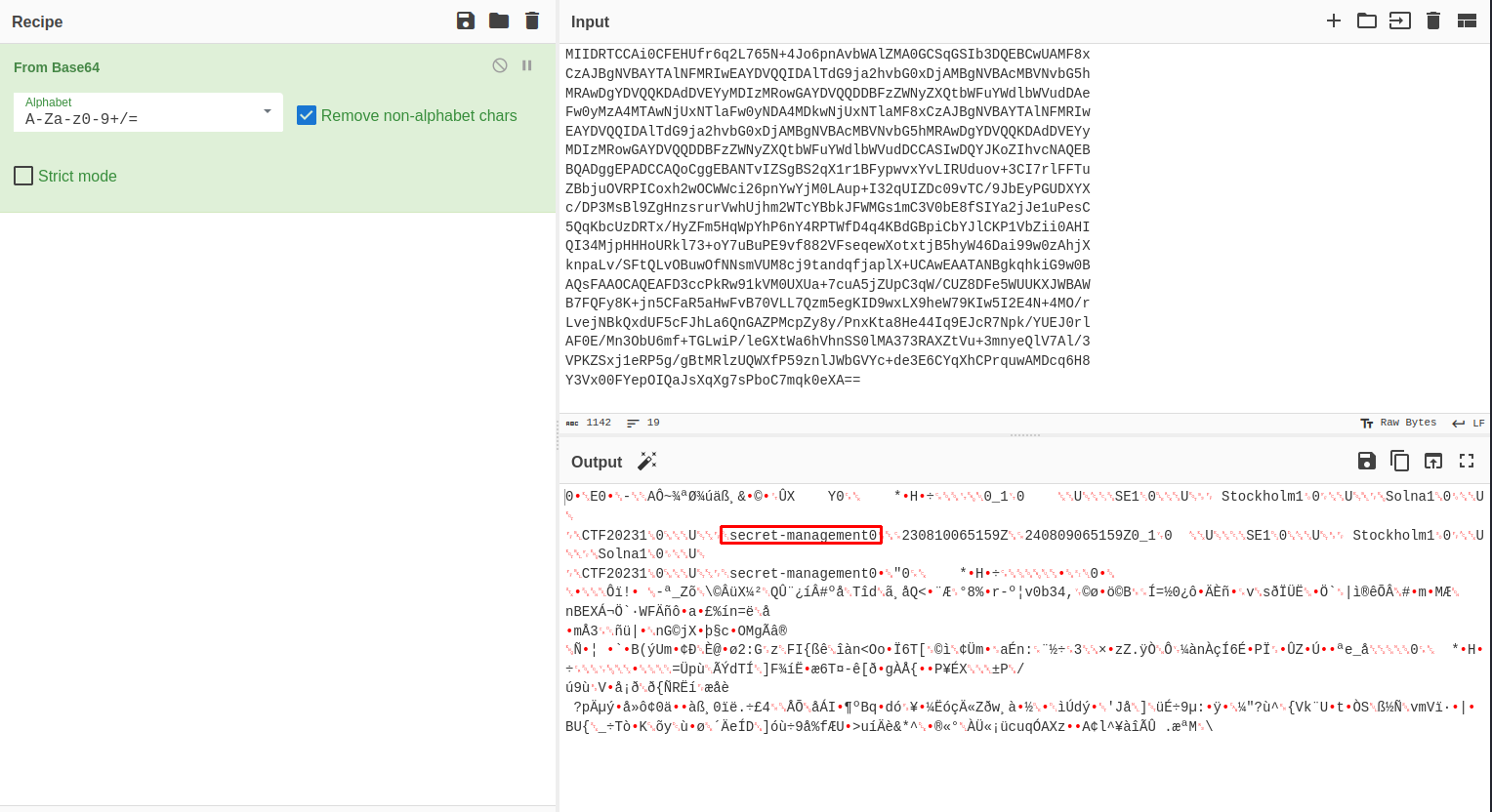
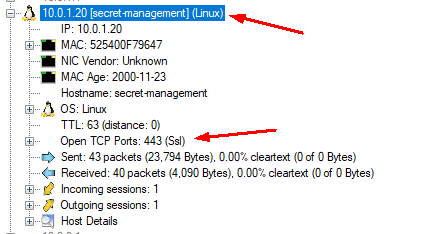
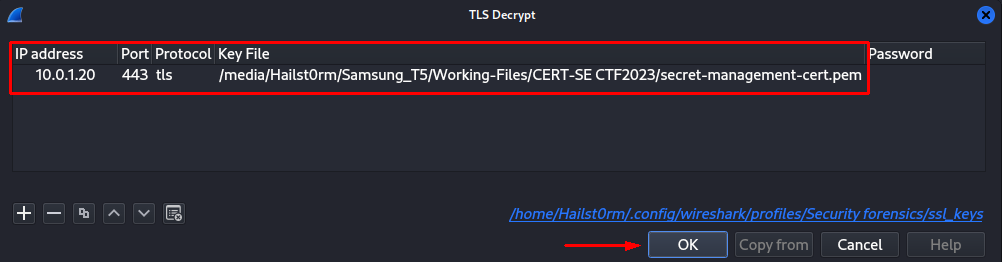
3. Now with this information we can try and decrypt the TLS (only TLSv2 possible). To do this I navigate to Preferences -> Protocols -> TLS -> RSA keys list, and fill in the information.
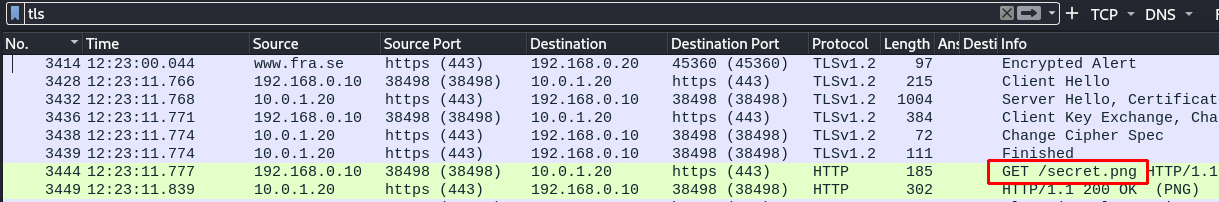
4. Looking at the TLS data we find a new file which contains the flag.
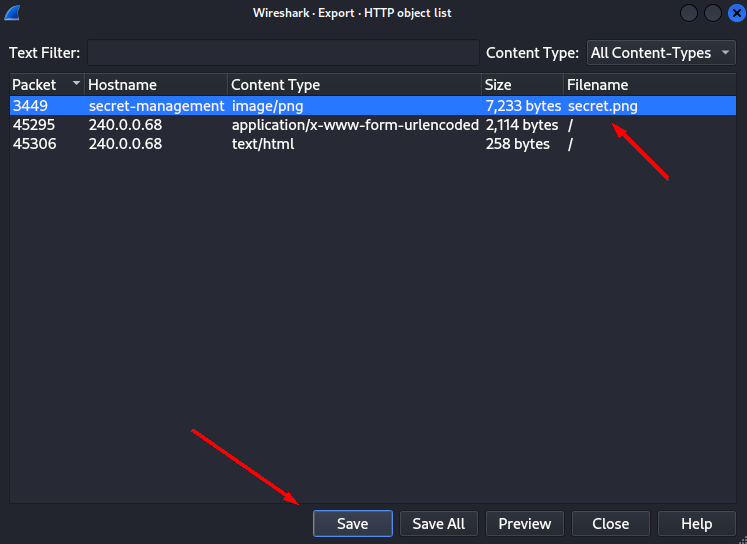
Answers(s)
CTF[GALOIS]
Flag 3 - FTP
-
Looking at used protocols I find FTP - unencrypted file share.
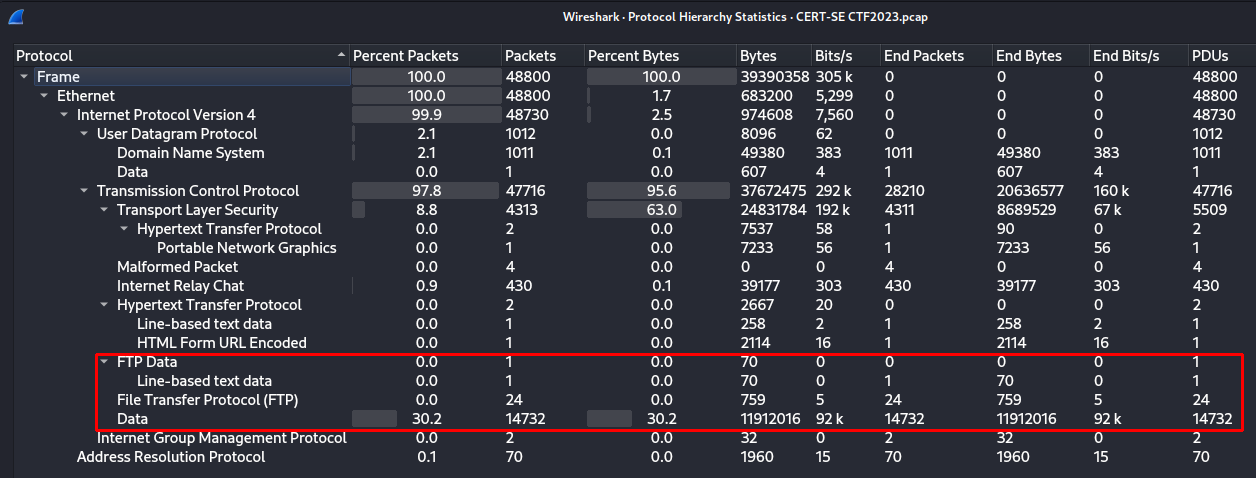
-
Searching for "ftp" and following the stream I find both the password but also an attempt at listing the files. However that data is not displayed in this stream and thus I search for the ftp ip.
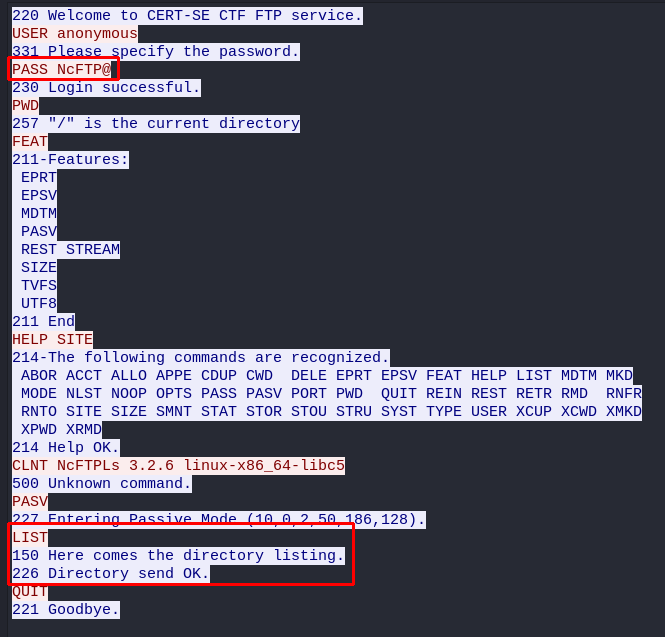
-
Here I find the data containing the flag.
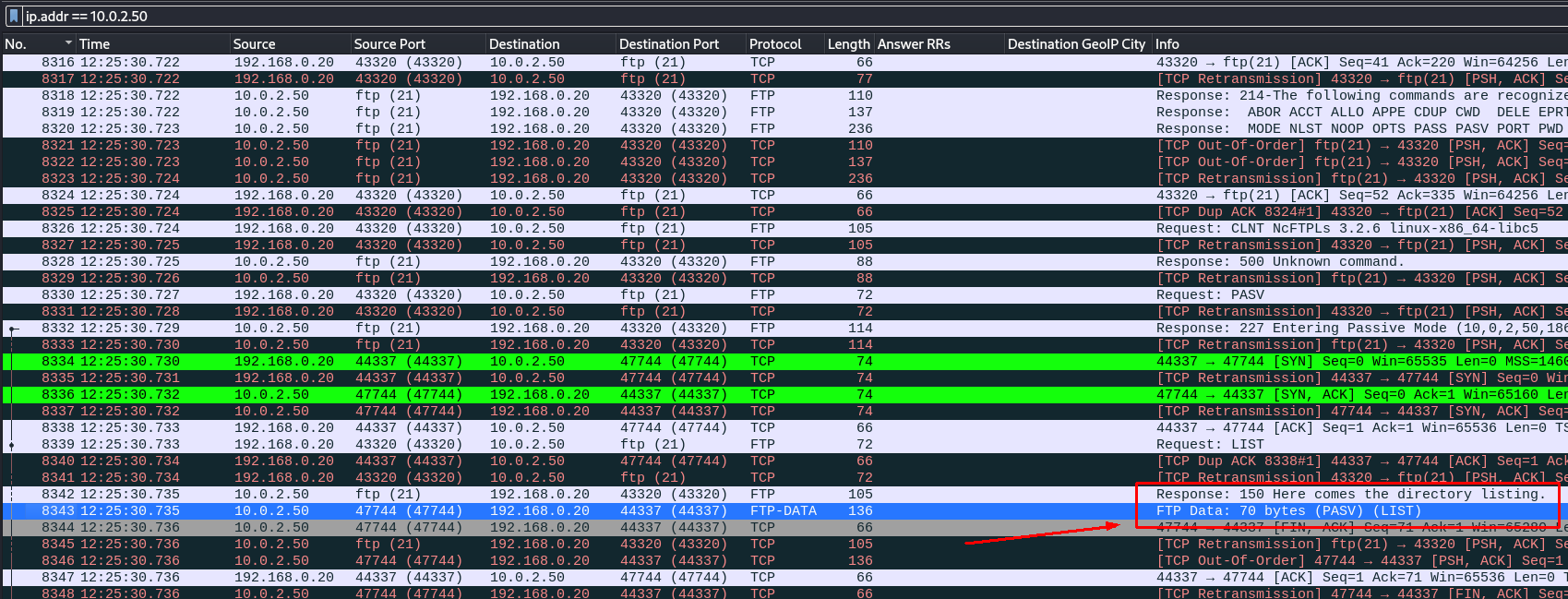
Answers(s)
CTF[HUNTER2]
Flag 4 - message.wav
- Looking at the the packet number (10728) of when the file was being sent by comparing the IRC conversation.
- Follow the TCP stream and we see it's a wav-file, as suspected. Make sure to change the conversation direction to only 192.168.0.10 as source and show data as raw before download. (Can also check against sha256 with
sha256sum).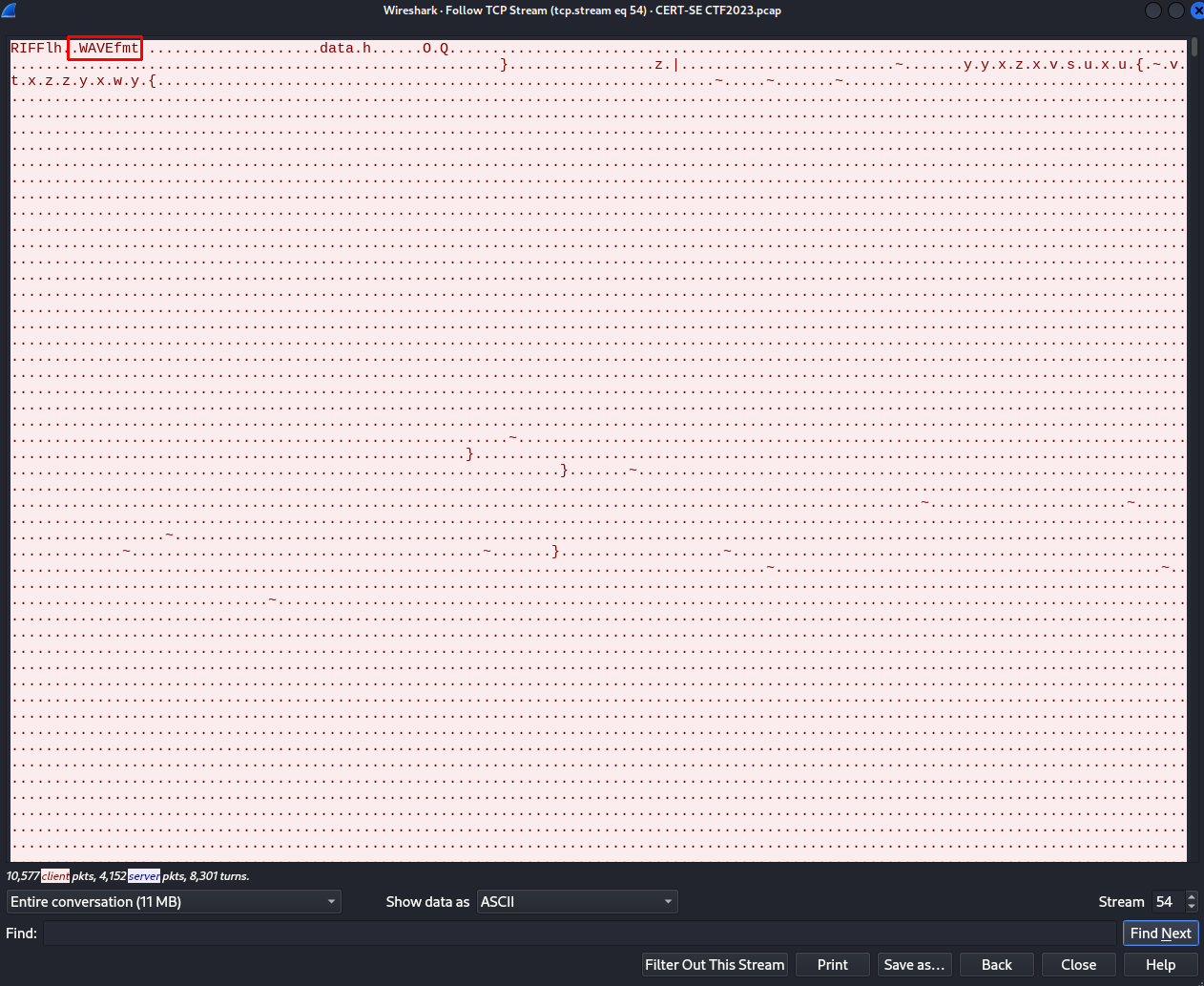
- I tried to look at strings, metadata and steganography but found nothing. When opening it in Audacity and turning on the spectrogram we find an anomaly.
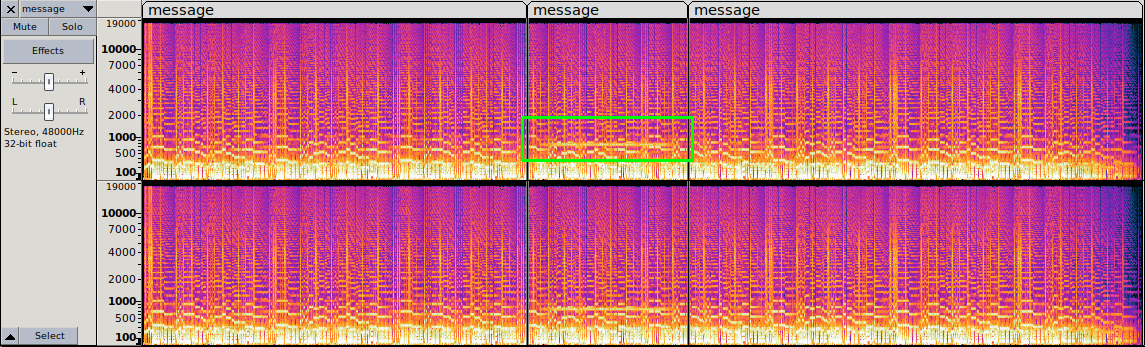
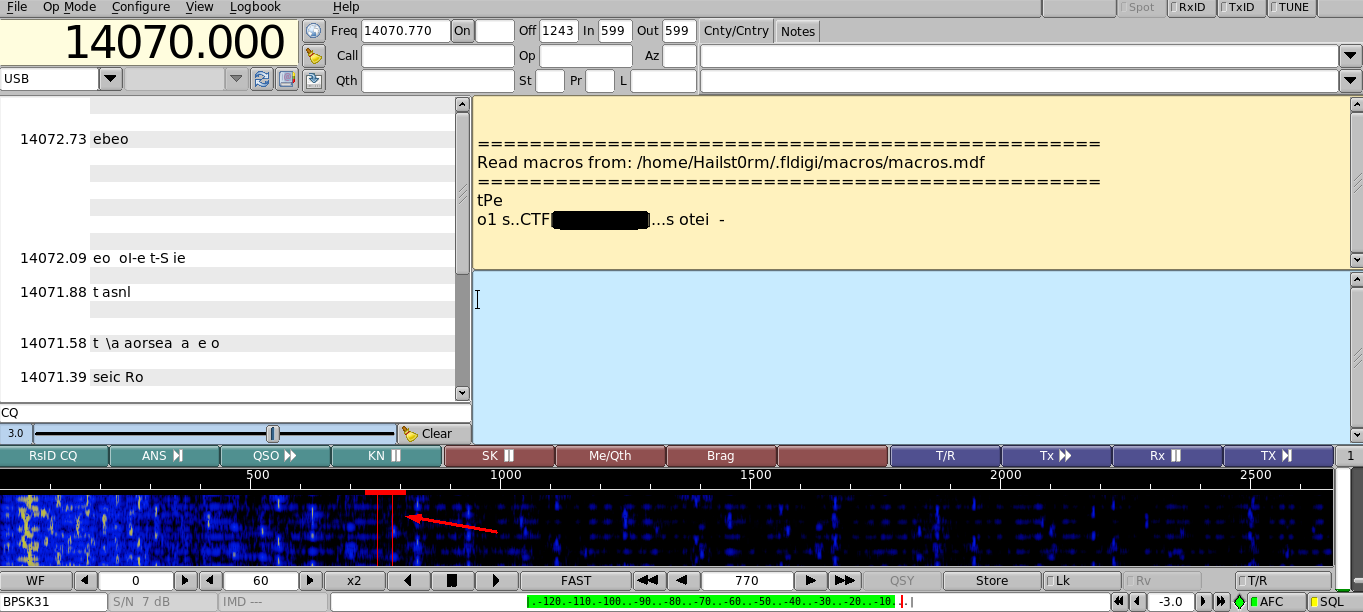
- After many rabbitholes I figured out it had something with radio to do - which led me to fldigi to capture radio. To "import" the file I navigated to Audio->Playback. Making sure to capture the correct frequency lead me to the flag.
Feedback
By far the flag I spent the most time on. To find the segment itself took a long time but the real issue is figuring out it's radio if you have no experience with radio before. Then there's the time consuming part of finding the right tool - but that is manageable. TL;DR: A hint about radio would probably be nice
Answers(s)
CTF[HAMRADIO]
Flag 5 - meta.xml
- At this point all that was left in the pcap was encrypted tcp with legitimate certificates - thus we go back to the odt file.
- I extract all source files and map it up with
tree.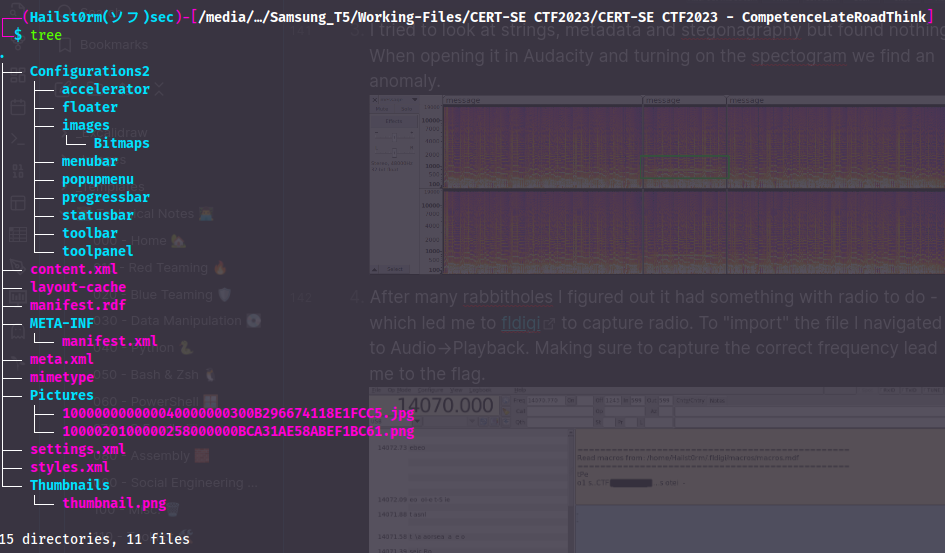
- Now I start going through the text files one by one to look for anything interesting. And look what we find in the
meta.xmlfile: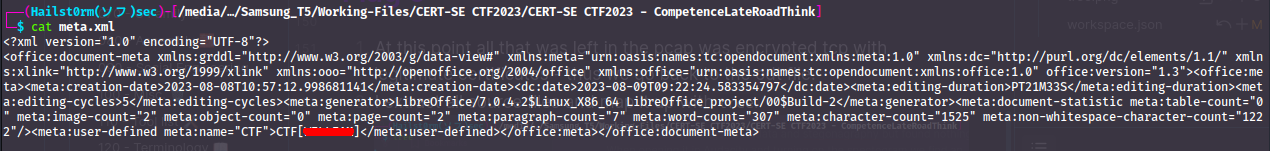
- With this realisation you can also get the flag using
exiftoolon the .odt file.
Answers(s)
CTF[WILLIAM]
Flag 6 - Sneaky Image
- I have yet to check the images that came with the odt file - so this was my natural next step.
- Looking at the metadata on the CERT-SE logo - I found that it has been modified with Gimp. This naturally makes me believe there's some "hidden ink" of some sort.
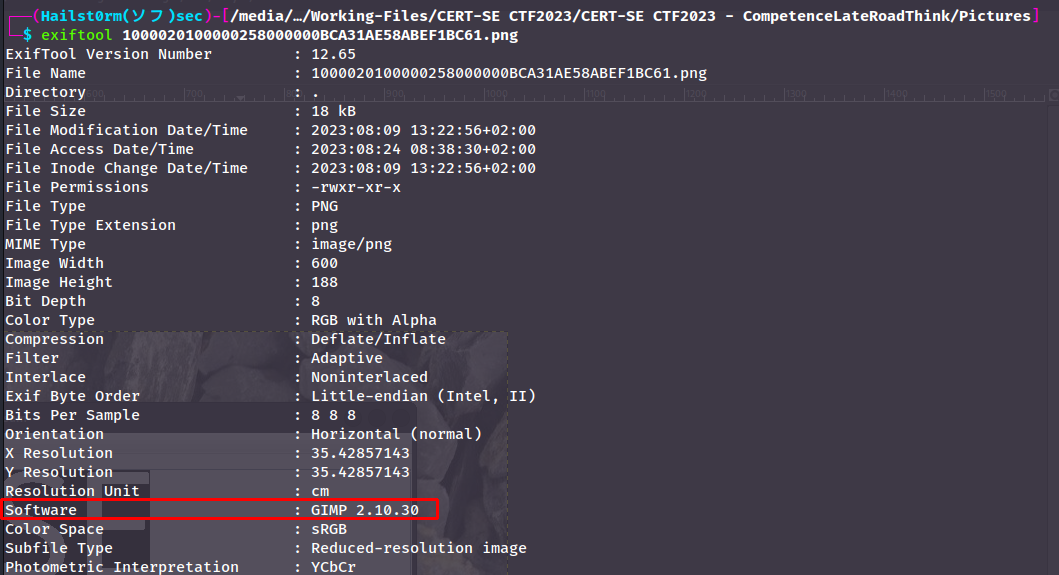
- I open it in
stegsolveand play around with the filters and find the flag. (Can also find it just playing around with colours in gimp).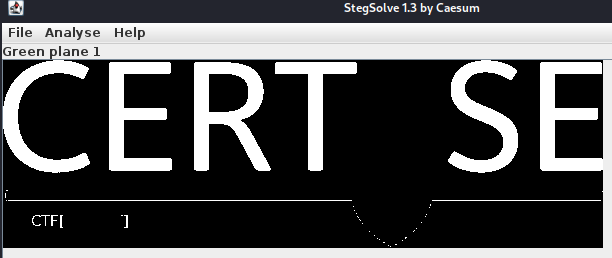
Answers(s)
CTF[SNEAKY]
Flag 7 - The stone cipher
- Now the only thing left that I can find suspicious is the image with stones. When I do strings I find that the file is ending in a weird way... Note that
FF D9indicates EOF (end of file) for a jpg.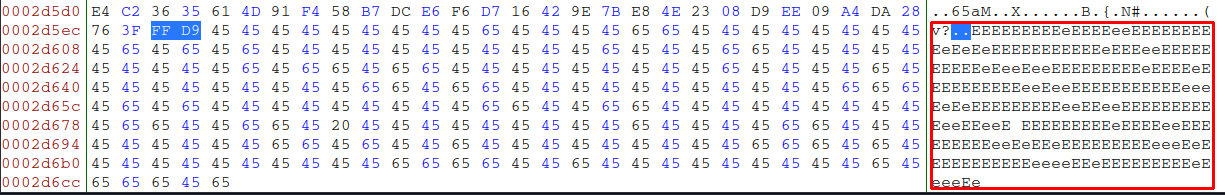
- Copying all the E:s and putting them into CyberChef gave me the flag.
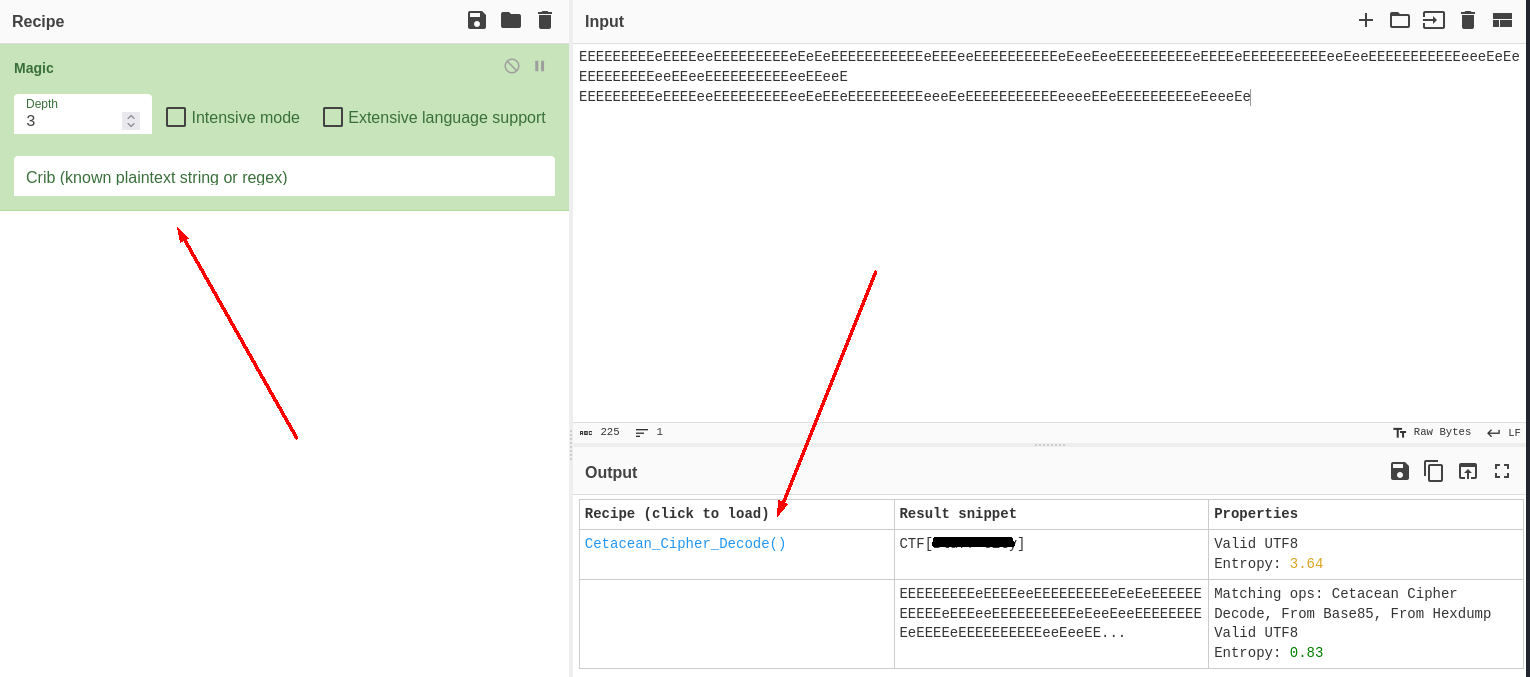
Fun fact
I managed to find what kind of rock the image contained: Black Slate. Black Slate in swedish is "Svart Shiffer", where "Shiffer", pronounced the same was as "chiffer", the swedish word for cipher. The cipher used for the flag was Cetacean Cipher.
Answers(s)
CTF[Bluff City]
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:


