Explore cybersecurity: Endless Possibilities
16 min read
Published at: Dec 7, 2023 (Updated at: Dec 11, 2023)

If you are new to the field of cybersecurity - this will be a perfect introduction of what you can expect. As well as to where you should start your journey.
Foreword
The field of cybersecurity has the same depth as the bottom of the ocean, and the possibilities are endless for what is achievable. However, it's essential to have the right expectations. The content on this page may feel overwhelming, but you cannot expect to be an expert overnight. With so much to learn, there are plenty of areas to explore and find something that suits you and brings enjoyment. At that point, studying will become much easier.
It's important to note that you do not require a budget or any past experience to enter the field, thanks to the abundance of free resources online. You can start your path in information security, regardless of your age, and almost anything you have done in the past will have a positive effect on your upcoming career. As of the time of writing this, there are more than 3.5 million unfilled jobs in cybersecurity - you are wanted in the industry.
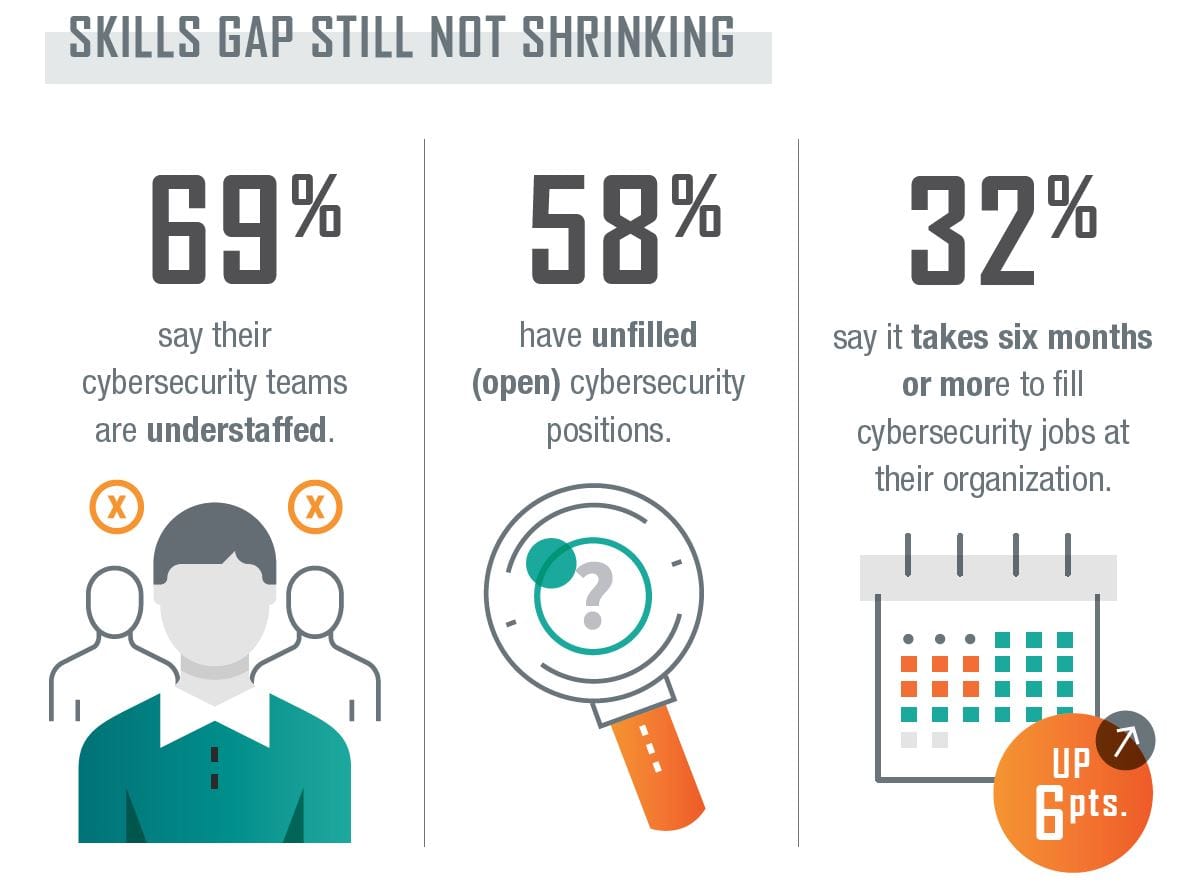
With so much to learn, I advise you to learn in a way that fits you. However, I am a strong believer that you have to perform labs and get your hands dirty before you completely understand a concept. A last note before going into the different areas of knowledge - I will emphasise that being willing to take notes will help you immensely to retain knowledge.
Notes
If you're uncertain on how you should take your notes or what software to use, read "The Ultimate Guide - How to Take Effective Digital Notes for Productivity and Success" after this.
Groups of knowledge and structure
Every concept listed bellow will be structured into three parts:
- Purpose - Why it's necessary
- Concepts - Basic knowledge
- Resources - Free material and labs
Knowledge groups:
- Cybersecurity Fundamentals: Basic understanding of cybersecurity and its key concepts with correct terminologies.
- Endpoints and Operating systems: Familiarise with Linux, the most common operating system for security specialists and Windows, the most popular choice for end users.
- Computer Networks: Understanding how information transmit across the internet and the basics for network architecture and protocols.
- Web: The vulnerabilities within the web and protocols for name resolution and web communication.
- Programming: Programming and scripting fundamentals, data manipulation and suggested languages.
- What's next?: I'll touch on the topic of certificates and what's the road ahead!
Cybersecurity Fundamentals
Purpose
The purpose of this section is to introduce some basic concepts and terminology. Having that basic knowledge will also introduce the mindset of "how can this be exploited" when moving onto the coming knowledge groups.
Concepts
The CIA triad is famous in the information security field and stands forConfidentiality, Integrity, and Availability. These three terms form the foundation of keeping information secure and are used to govern access to and the use of sensitive data.
- Confidentiality: Protect against unauthorized access and ensure that only authorized personnel can access sensitive data.
- Integrity: Ensure the accuracy of data and prevent unauthorized modification or deletion.
- Availability: Enable authorized personnel to access the data whenever needed without interruption or delay.
With the introduction of the first acronym, CIA (Confidentiality, Integrity, and Availability - the foundation of information security), I would like to bring to your attention that the work field is filled with acronyms and unique terminology everywhere. At first, it will be difficult to remember what means what. With that said, I highly recommend creating a "terminology" document to fill in after each new occurring term. You can find inspiration in my own document. Note, however, that I recommend including a wider description of each term.
When it comes to offensive and defensive techniques, the MITRE ATT&CK and D3FEND frameworks are king. Here you can go through every step in the cyber attack chain as well as the defensive techniques to mitigate, prevent, and respond to an attack. There are too many techniques for this article to go through; however, the following are a few very common cyber attack techniques and are good to memorize:
- Phishing: A phishing attack is a type of cyber attack in which an attacker sends fraudulent emails or messages to trick individuals into providing sensitive information, such as passwords or credit card numbers.
- Spear-Phishing: Same as phishing - however, the attacker crafts the email to be directed at a specific person or organization to improve their trust, thus having a better chance of a successful attack at the expense of time and the number of emails.
- Brute force: An attack where the adversary tries a huge number of passwords until they find the correct one. This is often accomplished with a dictionary of common passwords.
- Password spraying: Very similar to a brute force attack - however, the attacker uses a single, common password with many different usernames. The advantage of this is that many systems will block a user after X-amount of failed login attempts but not when trying to access different accounts.
- DDoS: Distributed Denial of Service is where an attacker floods a service or application with traffic - which, in turn, will make it overloaded and inaccessible to legitimate users.
- MitM: Man-in-the-Middle attack is an attack where the adversary intercepts communication between two parties and either reads or manipulates the conversation. The goal of the attack is to steal sensitive information.
- Ransomware: The attacker has control over one or multiple systems and encrypts its files - inaccessible to the users. The attacker will, however, leave a ransom note with details on how to pay the ransom to regain access to the files
Resources
Endpoints and Operating systems
Purpose
Over 75% of computer operating systems are Windows - although it is the most used OS by far, cybersecurity experts tend to prefer Linux for a couple of reasons:
- Linux is considered the most secure and virus-free operating system.
- Open source - generally more privacy and community maintained.
- More customizable - with many distributions designed for different purposes.
- Wide variety of integrated tools - and easy to develop your own.
- More power for the user with system configurations.
Quite the contrary, Windows is considered a very complex piece and difficult to understand because it has to support a wide range of hardware configurations and software applications. It has a large codebase with multiple layers of software and services that interact with each other, making it easy to misconfigure or abuse. Additionally, Windows has to balance backward compatibility with new features and security updates, making it a challenging system to develop and maintain.
Concepts
Before practicing using a Linux distribution, you would need to decide on a distribution. Personally, I would recommend Ubuntu due to its friendly user interface and simple installation process. It also has a highly active and large community of users and developers.
Bare metal vs Virtual Machine
If you have an unused computer laying around, it might be worth using for a complete Linux system. However, most people do not, and thus I recommend installing Linux on a virtual machine. Think of it as a computer inside your computer. Read more on how to set up a virtual machine here. Remember to enable "virtualisation" in your system BIOS.
For the basic commands I recommend learning below, I will assume you have a Windows system ready. If not, you can follow the same procedure with a VM (Virtual Machine) together with Windows ISO.
Bash (Linux):
# Help page and manual for command
COMMAND -h
COMMAND --help
man COMMAND
# Files and directories
ls # List directory
cd # Change directory
pwd # Current directory path
mkdir # Make directory
cat # Read file
touch # Create file
nano # Edit file
vim # Edit file (more advanced)
mv # Move or rename files or directories
cp # Copy files or directories
# File content and text stream manipulation
grep # Search pattern in file
awk # Pattern scanning and processing
sed # Stream/Text editor
tr # Text transformation
cut # Cutting and isolating text segments
paste # Merge lines from multiple files
sort # Sorting
# Processes and services
ps # List processes
kill # Kill processes
service # List services
systemctl # Manage services
# Web interaction
wget # Download web content
curl # Send web requests
# Package manager
apt # Apt package manager
PowerShell (Windows):
# Note: Commands are built up with Verb-Noun prefix
# Help page and manual for command
Get-Verb # List Verbs
Get-Help OR Help # Help command
Help COMMAND -Examples # Command use examples
Get-Command # Get command based on name
Get-Command -Verb # Get Nouns for given Verb
Get-Command -Noun # Get Verbs for given Noun
Get-Alias # List command for given alias
Get-Alias -Definition # List aliases for given command
# Files and directories
Get-ChildItem # List directory
Set-Location # Change directory
Get-Location # Current directory path
New-Item # Create file or directory
Get-Content # Read file
Move-Item # Move file or directory
Copy-Item # Copy file or directory
Rename-Item # Rename file or directory
# File content and text stream manipulation
-split # Split text
-replace # Replace text
-join # Combine text
# Processes and services
Get-Process # List processes
Stop-Process # Kill processes
Get-Service # List services
Stop-Service # Stop service
Restart-Service # Restart service
# Web interaction
Invoke-Webrequest # Get content from web
Invoke-RestMethod # Send request to REST service
# Package manager
Install-Package # Install package
Uninstall-Package # Uninstall package
Windows Command Prompt (cmd.exe) in PowerShell
Windows PowerShell is generally more powerful than the old cmd.exe - however if you find a command limited to cmd you want to execute, you can use cmd.exe /c COMMAND
Additionally you will find great use of knowing other important system concepts.
A few of which are:
- Storage
- CPU
- Memory
- Core directories
- Filesystem hierarchy
- Windows Registry
You will find resources below to understand these concepts bellow.
Resources
Computer networks
Purpose
Understanding how standalone computers work and how to secure them is great. However, computer networks are the backbone of modern computing and are the primary means of communication between devices. All the computers you are using are most likely connected and talking to other computers all the time. By being able to monitor the networks, we can both identify and analyze cyber threats. So, a thorough understanding of networks and how they work is essential for being an effective cybersecurity practitioner.
Concepts
One common way to visualize how data is transmitted across a network is the OSI model (Open Systems Interconnection). This model describes computer communication with 7 layers.
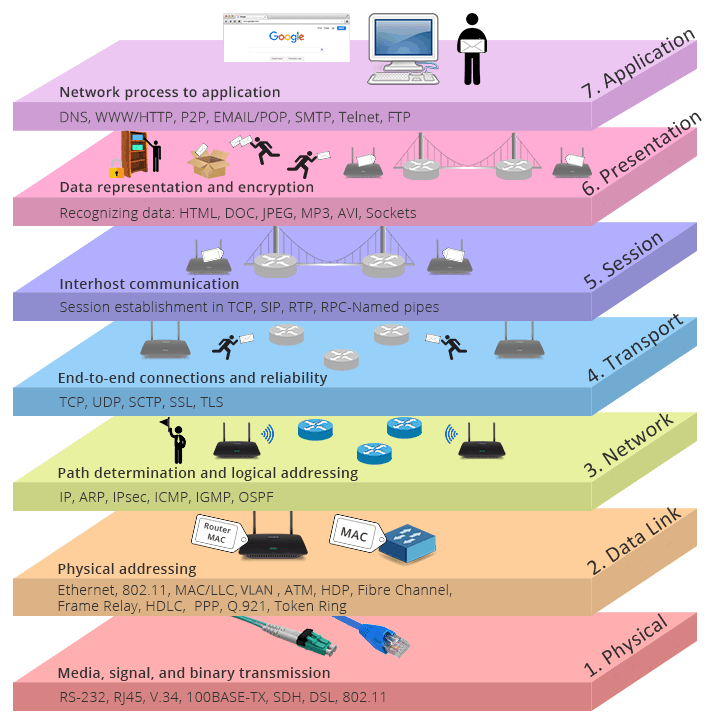
- Physical: The physical medium that sends data in binary code.
- Data Link: Establishes and terminates connections between two physically-connected nodes on a network. Firewalls operate on this layer.
- Network: Responsible for choosing the best path across physical networks and assigning source and destination IP addresses. Routers operate at this level.
- Transport: Manages end-to-end connection and transmission according to the connection speed. Two crucial transport protocols are TCP and UDP, which will be explained more in depth below.
- Session: Handles interhost communication and session management.
- Presentation: Prepares the data for the Application layer by managing the encoding, encryption, and compression of the data so that the application can interpret it.
- Application: Used by the end-user. It could be anything from a web browser to file-sharing applications or email transportation.
Sometimes people within the industry also talk about the 8th layer; the user. In cybersecurity, we often discuss vulnerabilities for the different layers. Just like the other layers can have vulnerabilities, humans have them too. One example could be that we are vulnerable to fake emails or phishing attacks, as mentioned previously.
The most important protocols to gain an understanding of are the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP is connection-based and requires a 3-way handshake between the two clients before transmitting any data.
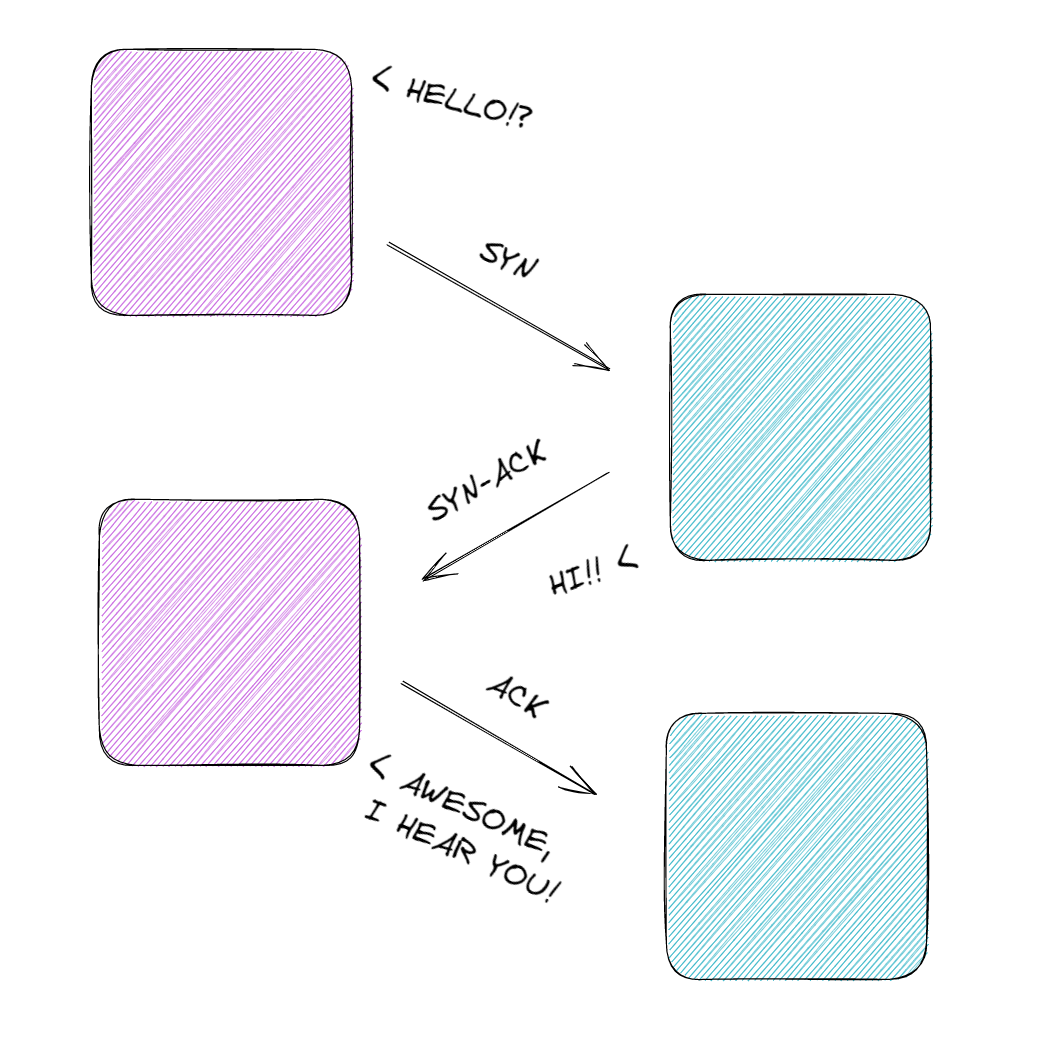
The client who wishes to transmit data begins the communication with a SYN. The second client will then send a response, SYN-ACK, confirming they want to establish a connection. The transmitter will then send a last message, ACK, to confirm and establish a connection and begin sending data. The data packets will also be assigned a segment number to prevent the receiver from receiving the packets in an incorrect order. To finally close the connection, the handshake will be repeated, but instead with the FIN flag instead of the SYN flag.
UDP, however, takes a more direct method for transmitting data. The receiver sends a request for data to the sender. The sender will thereafter send all the information in separate packets with no indicator to tell if the packets are delivered in the intended order.
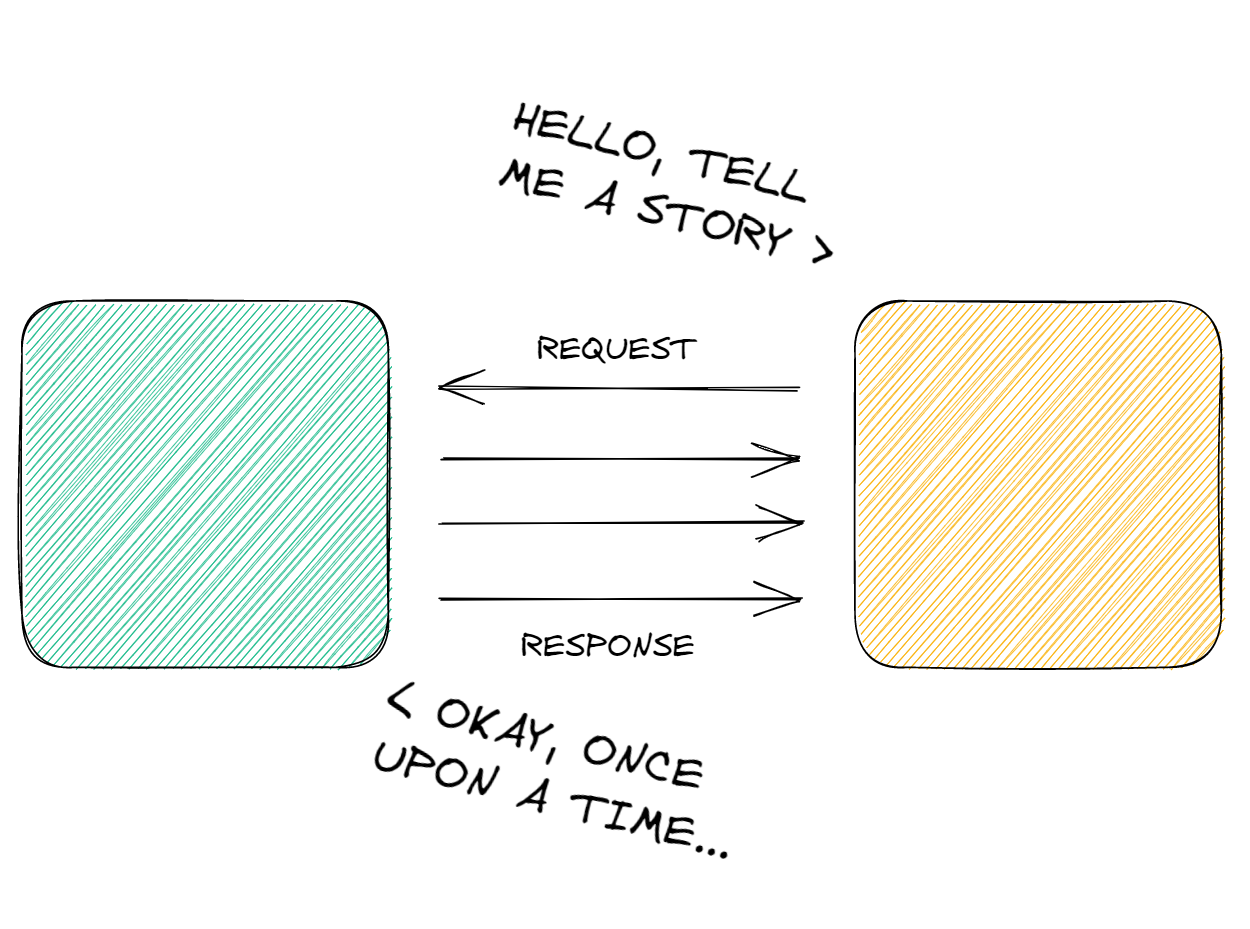
The main differences between the two protocols is therefore:
| TCP | UDP |
|---|---|
| Connection-based | Connection-less |
| Packet reorder mechanism | No mechanism |
| Slow transmission | Fast transmission |
| Acknowledge Mechanism | No Acknowledgement |
| Guaranteed Transmission | No Guarantee |
| Used for transmission where reliability is important: File downloads or displaing a webpage | Time sensitive applications: games, livestreaming |
Other protocols and features worth understanding
- Network ports
- ICMP
- DHCP
- ARP
- STP
- SSH
- Telnet
- VPN / Tunnels
- Proxies
- LAN / VLAN
List with useful commands related to computer networks:
# Linux
ip # Network management
ip a # List ip-addresses
ip n # List neighboring devices
ping # Send ICMP-packet, used to determine if host is reachable
nmap # Send TCP/UDP-packets to scan whether there are, and what, application running on targeted host
arpscan # Send ARP-packet to scan for MAC-address and hardware for given host
tshark # Investigate network traffic (or use Wireshark application)
tcpdump # Tap network traffic
nc # Netcat, used to communicate between machines over TCP
netstat OR ss # Se network connection on machine (netstat also on Windows)
ssh # Remote shell over tcp (also on Windows)
scp # Remote copy of files over ssh (also on Windows)
openvpn OR wireguard # VPN services
iptables # Set up network rules (like a firewall) on local machine
proxychians # Proxy commands via a proxy server
# Powershell
Get-NetAdapter # Lists network interfaces
Get-NetIPConfiguration OR ipconfig # List ip-addresses and overall network configuration
Get-NetIPAddress # Get ip-address information
Get-NetNeighbor # List neighboring devices
netsh # Display or modify the network configuration
Resources
Web
Purpose
Ever since the internet was introduced to us, browsers have been among the most popular computer software for a handful of years. We are all taught not to browse suspicious websites due to the possibility of being infected with a virus. However, what you may have missed is that a large number of intrusions by threat actors occur via public-facing applications, typically websites. A study by SOCRadar claims the number can be as high as 21% of successful unauthorized accesses, making it the third most common tactic after external remote services, such as an exposed VPN service, and phishing.
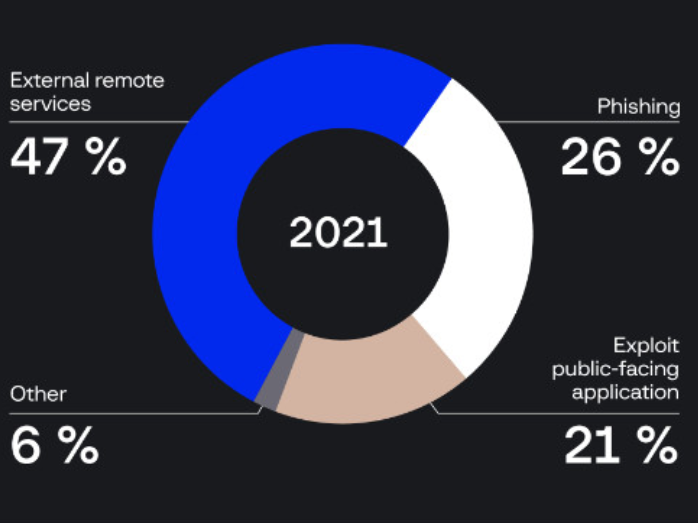
With this in mind, it will be important to both understand how the web works - and how it can be exploited.
Concepts
Websites are generally built up using three different programming languages:
- HTML for website content
- CSS for the aesthetics and styling
- JavaScript (JS) for website animations, scripts, or built in applications
- Can also have a back-end database for e.g. storing user credentials, often use the SQL-query language
Which language to learn?
There are many web protocols - but by right-clicking on a website and choose "view page source" you will see the website before compilation. What you see is the HTML-code with links to other protocols or frameworks used. Therefore understanding HTML is most important followed by JavaScript and SQL due to their impact in cybersecurity.
Websites are stored in web-servers - but since computers talk in IP-addresses, how does the browser know where to find the website "google.com"? It's due to the protocol
Domain Name Server
.
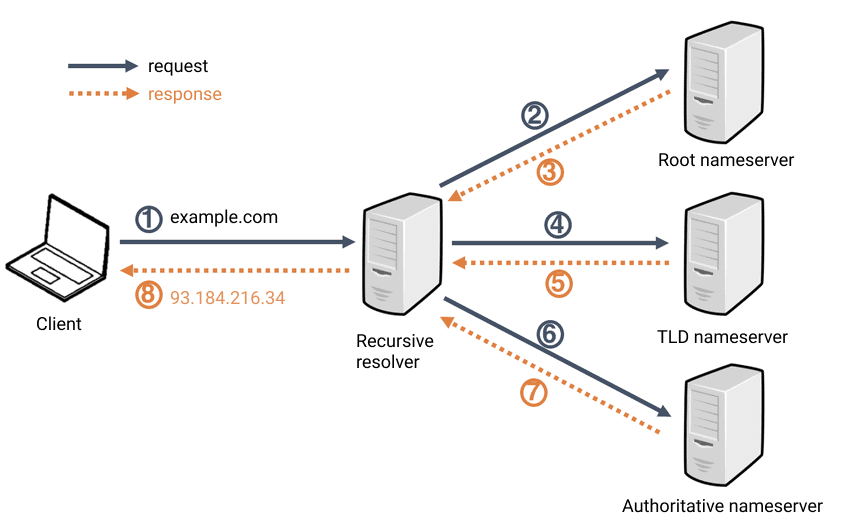
So if we resolve the google domain - we will get the IP 142.250.74.142. By searching on that IP we will arrive at the google landing page.
When we browse to websites we send requests with the protocol HTTP (Hyper Text Transfer Protocol) or HTTPS (Secure). HTTP is however not considered a secure protocol since the data being transmitted is not encrypted and is therefore vulnerable be intercepted or tampered with. HTTPS on the other hand encrypts the data with TLS (Transport Layer Security). Whether a website is using HTTP (🔓) or HTTPS (🔒) is displayed with the padlock in the search-bar. Even if you use HTTPS your IP-address will be exposed since it cannot be encrypted because the receiving server needs it to be visible to establish a connection. To stay anonymous you would have to use a VPN or an anonymity browser such as onion browser to obfuscate your IP, you can read more in the resources.
It is also important for us to understand the entire content of the URI you put into your google search bar:
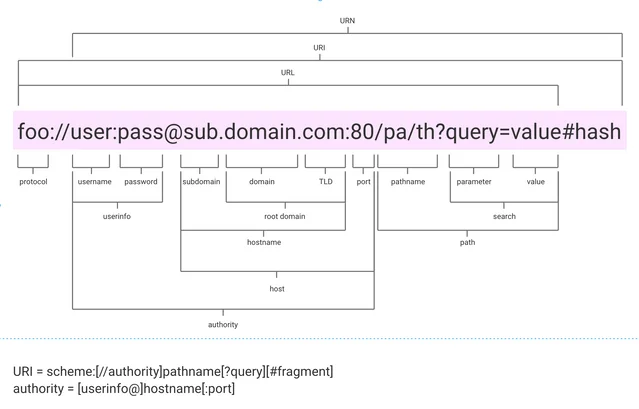
Explanations of the URI parts:
- Scheme/Protocol (
foo://user:[email protected]:80/pa/th?query=value#hash):
The scheme, often referenced as the protocol, dictates how the content or file will be displayed, formatted, and transferred across the web. Some common protocols are http and https, as mentioned before,
File Transfer Protocol
, and
Single Mail Transfer Protocol
.
- Username and password (foo://
user:pass@sub.domain.com:80/pa/th?query=value#hash):
This is an authentication method named "Basic Authentication" and is considered outdated and insecure by today's standard. Mainly due to how it can easily be intercepted, making your credentials susceptible to being stolen.
- Subdomain (foo://user:pass@
sub.domain.com:80/pa/th?query=value#hash):
A part of a larger domain and could be used to structure and organize content. An example could be to host the website blog under <a href="blog.website.com">blog.website.com</a> and the store under <a href="store.website.com">store.website.com</a>.
- Domain (foo://user:pass@sub.
domain.com:80/pa/th?query=value#hash):
Often considered the main part of the URI and what makes it recognizable. Together with the
Top Level Domain
and subdomain, it is the human-readable label to represent the IP. Compare remembering google.com to 74.125.131.138 when wanting to use Google.
- TLD
Top Level Domain
(foo://user:[email protected].
com:80/pa/th?query=value#hash):
The last part of the domain name and is restricted to a set amount. Most common ones are .com, .org, .net, .gov, and country code TLDs like .uk or .se.
- Port (foo://user:[email protected]:
80/pa/th?query=value#hash):
Often forgotten and will be found after the colon. It determines the port the service is running on. Some well-known ones are 443 for HTTPS, 80 for HTTP, and 21 for FTP. You can learn more about what ports are and well-known ports here.
- Path (foo://user:[email protected]:80
/pa/th?query=value#hash):
The path is the directory on the server where the information is stored. So in this example, we are looking for the file/folder th in the directory pa.
- Query, parameter, and value (foo://user:[email protected]:80/pa/th
?query=value#hash):
The question mark indicates that the URI includes a query, which indicates that the browser is querying (or looking for) information from the database or API. The query indicates the parameter we are looking for with the value value.
- Fragment (foo://user:[email protected]:80/pa/th?query=value
#hash):
Finally, we have the fragment, most of the time indicated by a # and will never be sent away to the server. Instead, it will be fully processed on the client side. A common use case is to go to a specific segment of a webpage. Try clicking https://hailstormsec.com/new-to-cyber#concepts-3 and see what happens.
This understanding is highly important for many reasons. It enables you to more easily create or detect a phishing campaign, query for information you shouldn't have permission to see, or even check if a website accepts Basic authentication. The sky's the limit!
Tools for the web:
# Linux
nslookup OR dig # DNS lookup
/etc/<a href="resolv.conf">resolv.conf</a> # DNS configuration
resolvectl # Manage DNS configuration
# Windows
Resolve-DnsName # DNS resolve
Get-DnsClientServerAddress # DNS server addresses
Get-DnsClientCache # Get cached DNS resolve
Other tools
- Burp Suite - Web application security testing tool
- MXToolbox - DNS troubleshooting and lookup
- DNS Dumpster - Historical DNS data
- ViewDNS - Detailed DNS and website enumerating tool
Resources
Programming
Purpose
What you come to realize in cybersecurity is that tools and graphical interfaces will not solve all your problems. More often than not, you have to configure something by yourself or write your own tool to solve a specific problem.
But in what programming language should you start with? There is no right or wrong answer to this question. Ultimately, you will benefit the most from the language you feel the most comfortable in, no matter if it is Java or Lisp.
Concepts
Even though I recommend what you're comfortable with, I will strongly suggest three languages that will dramatically help you as a cybersecurity specialist:
- Python: One of the most well-known programming languages, recognized for its ease of learning. It can accomplish almost anything due to the large user and developer community. It is also easy to debug for the same reason.
- Bash: Due to the significant amount of time you will spend in the Linux operating system and the wide variety of tools it has to offer. Writing scripts in bash will come in handy to make your time more efficient. Also called shell scripting.
- PowerShell: Very similar reasoning to bash - there is no other programming language that can utilize the Windows operating system as well as PowerShell can. It is even often available in Linux operating systems due to its power.
Whenever you've decided on a programming language, I recommend learning the following concepts:
- Data Types
- Variables
- Flow logic (if-else statements)
- Loops
- Functions
- Object-oriented programming (OOP)
Other languages within cybersecurity
- Web & Databases: JavaScript, , SQL
- Malware development & Analysis: C, C++, Assembly
RegEx
Regular Expressions (RegEx) is used for pattern matching and is highly useful in cybersecurity. I therefore highly recommend learning it when possible.
Resources
What's next?
To make a career within cybersecurity, you could wander many paths. Some have gone through college, while others have climbed the work ladder. However, no matter which path you decide to go down, cybersecurity certificates significantly help you land the job you want and stand out from the masses. But there are a lot of them, and I cannot cover which each and every one you should pursue. To get a better understanding, I recommend watching the video below. Both because they have more experience than I do and because it's simply a good video.
There has been a lot of content in this post, and I do not expect you to have gone through it all. However, keep in mind that these things are all important fundamentals within cybersecurity. As you go in your career, you will find things that will pique your interest more than others and will naturally gravitate yourself towards that. The world of cybersecurity is too big to be an expert in all, so find your niche and have fun!
Going forward, I recommend checking out my suggested resources, which are more centered around resources to improve at cybersecurity. I highly recommend following cybersecurity in media, watching videos, and listening to podcasts
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:


